Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.

2D flat plane introduce distortions, noise and incon-
sistencies on the captured fingerprint image. To over-
come these problems, a new approach to capture
fingerprints has been proposed [6, 7], called touchless
or
▶ contactless fingerprinting . Because of a lack of
contact between the finger and any rigid surface, the
skin does not deform during the capture and the re-
peatability of the measure is improved.
The approaches used to capture a fingerprint
based on touchless technology can be grouped in two
main families:
▶ Reflection-based Touchless Finger
Imaging (RTFI) and
▶ Transmission-based Touchless
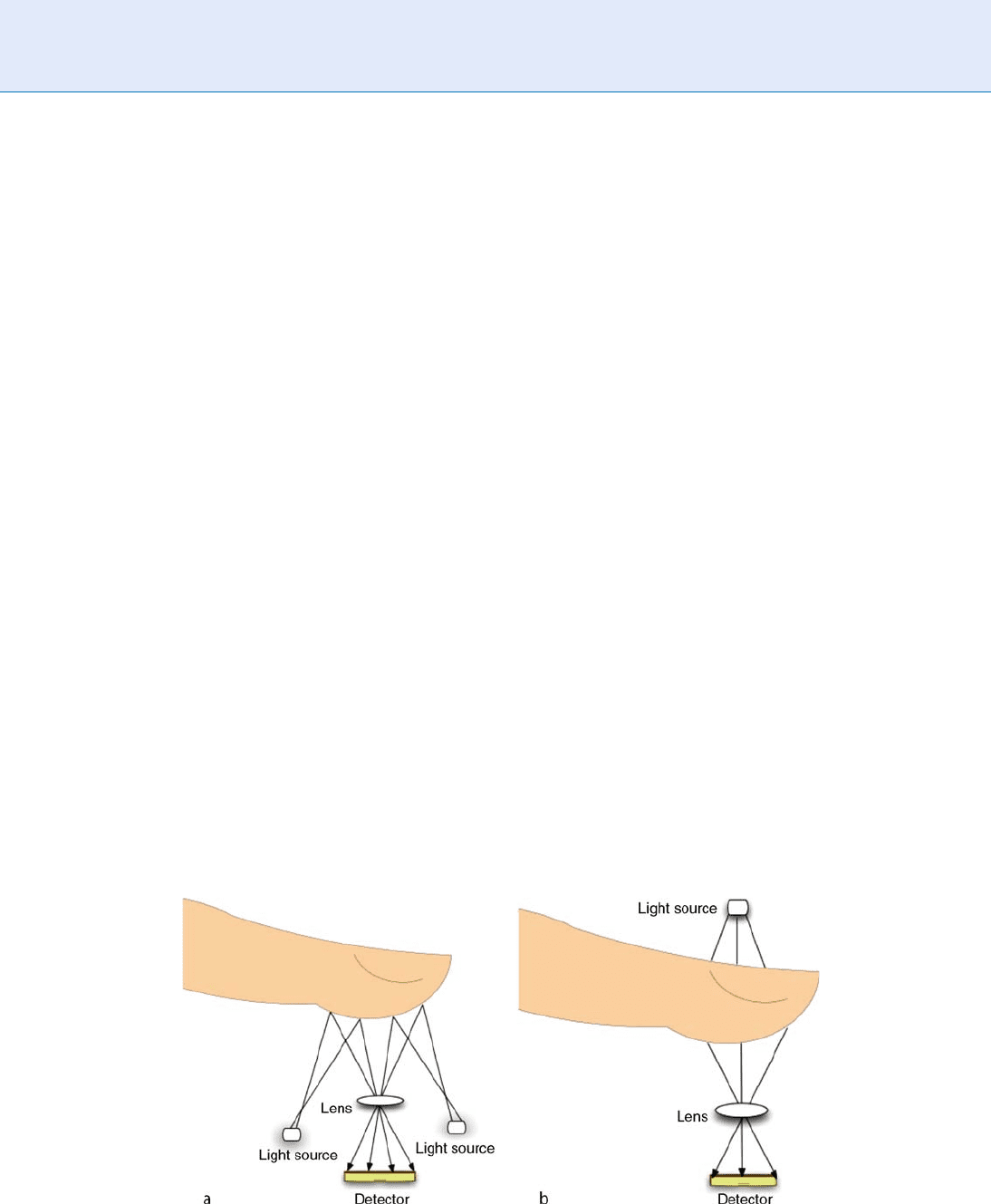
Finger Imaging (TTFI). Figure 3 highlights the two
approaches. In the RTFI approach, the light generated
by monochromatic light sources and reflected on the
finger skin is collected by the detector. In the TTFI
approach, the light penetrating the finger is collected
by the detector positioned in front of the ridge–valley
pattern.
Since both the light reflecting on or penetrating the
valleys and the light reflecting on or penetrating
the ridges are collected by the detector, the final
image has a contrast lower than that in the traditio nal
FTIR technology. This has a huge impact on the min-
utiae extraction algorithm and thus, the advantage
of a lack of skin deformation is negatively compen-
sated by thi s low contrast. Moreover, the illumina-
tion not being perfectly perpendicular to the skin
surface, shadowing effects of the ridges on the valley
provide a wrong representation of small details (min-
utiae, pores, island, branches, etc.). Sophisticated
illumination techniques are required to avoid this rep-
resentation problem and increase the final image con-
trast. The consequence is an increase of the size and
final costs of these devices.
Another disadvanta ge of this technology is repre-
sented by the easy methods that can be used to attack
these devices, which cann ot be definitively used for
high-securi ty applications. In contrst to the FTIR
case, where the ridge–valley 3D structure is important
to generate an image, the touchless approach cannot
discriminate between a 2D and a 3D pattern. Hence,
presenting a photograph or a simple drawing of a
fingerprint to the sensor, a new fingerprint image sim-
ilar to the synthetic one is generated and the access is
granted. Finger positioning, sensor usability, and user
convenience must be still addressed.
Solid-State Sensors
The first solid- state fingerprint capture device appeared
on the market only in the middle of 1990s. It was a
CMOS sensor capable of measuring the electrical ca-
pacity between the finger skin and the sensing surface
(Fig. 4), which is composed by many squared pixels.
Each pixel and the corresponding skin portion can
be considered as an electrical capacitor with capacity
C ¼ eA ∕d, where A represents the pixel area and d the
distance between the skin and the pixel and e is the
permittivity (a constant depending on the material) of
the dielectric contained between the two capacitor
Fingerprint, Palmprint, Handprint and Soleprint Sensor. Figure 3 ▶ Touchless or contactless capture approach:
(a) reflection-based touchless finger imaging; (b) transmission-based touchless finger imaging.
540
F
Fingerprint, Palmprint, Handprint and Soleprint Sensor
plates. Each pixel produces a graylevel value propor-
tional to its distance from the skin.
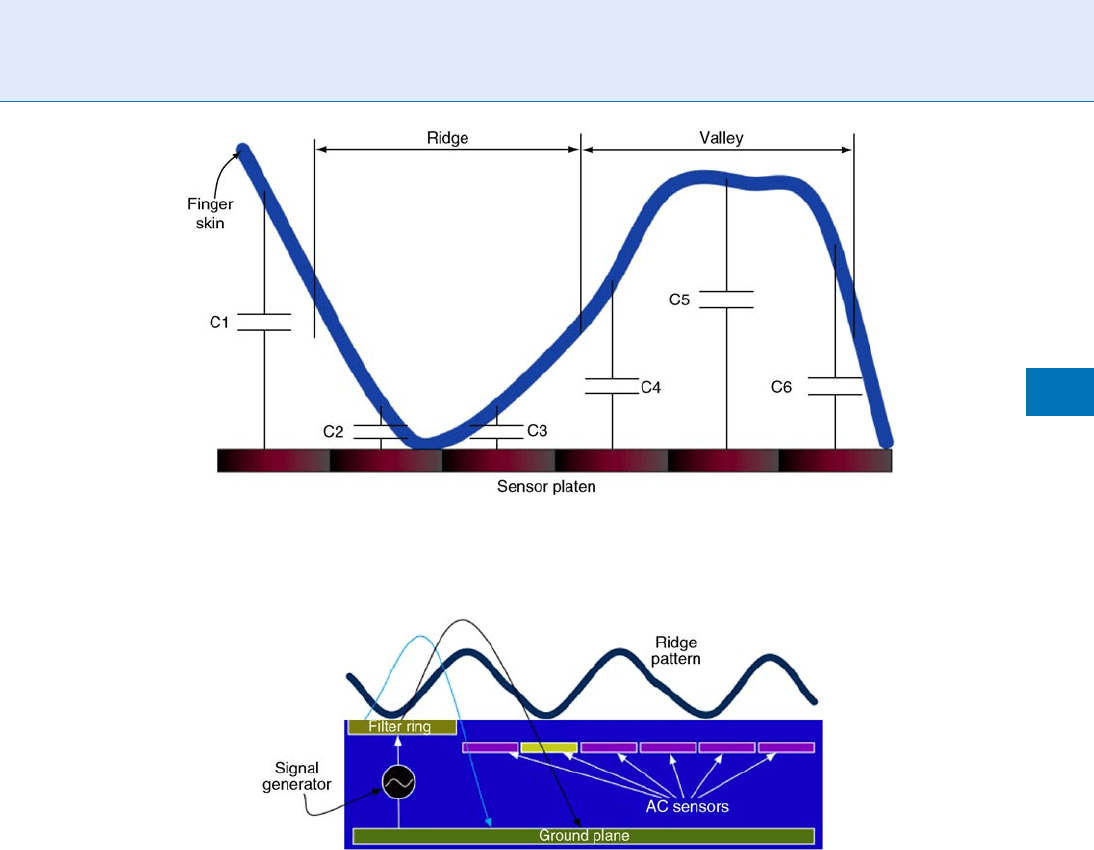
Another approach used to capture the ridge–valley
pattern is based on the Radio Frequency (RF) electrical
field (Fig. 5). A signal generator produces a low-level
RF field traveling through the finger. The signal is then
collected by AC sensors after being attenuated by the
finger skin. The attenuation level of the signal is a
function of the ridges and the valleys; the sensor array
calculates the attenuation to synthesize the fingerprint
structure. RF signal can be dynamically optimized in
frequency and level to obtain the best possible image.
Using pyroelectric materials, it is possible to mea-
sure the difference of temperature between ridges and
valleys. This approach is used while the finger is swiped
on the small sensor surface (Fig. 6). This type of
devices are called
▶ sweep sensors [8, 9]. The thermal
sensing elements detect temperature difference be-
tween valleys and ridges during the finger movement.
This technology is claimed to overcome the skin con-
dition issues of optical sensors. However, the resulting
images are not rich in gray level values, i.e., dynamic
range. Sweep sensors are ver y attractive because of
their small size and low cost. This makes easier their
integration in handheld and mobile devices.
The big advantage of the solid-state technology is
represented by their smaller dimensions and lower
costs with respect to the optical technology. Since
they can be manufactured very thin and their power
consumption needs are very low, solid-state sensors
can be mounted on cards, handheld devices or laptops
and used as logon means. This has an implication on
the range of applications in which solid-state finger-
print sensors can be involved with respect to the
Fingerprint, Palmprint, Handprint and Soleprint Sensor. Figure 4 Capacitive principle for the capture of the
ridge–valley structure.
Fingerprint, Palmprint, Handprint and Soleprint Sensor. Figure 5 Radio Frequency Field principle used to capture the
ridge–valley structure.
Fingerprint, Palmprint, Handprint and Soleprint Sensor
F
541
F
optical devices. However, external environmental fac-
tors (temperature, humidity, dust, etc.) are the major
drawbacks of this technology. The sensing area is a chip
completely open to the external world. Thus, special
electrostatic protection method s must be used to avoid
that external electrostatic charges destroy the chip sur-
face. The same human skin can be the cause of the
surface destruction, since the human body is usually
electrically charged. Dust is another common vehicle
of electrostatic charges that can quickly and easily
degrade the sensin g surface characteristics.
The use of solid-state sensor is mainly limited to
fingerprint for their small sensing area. Palmprint and
soleprint would require very large silicon areas that
would make these sensors completely unaffordable in
term of costs.
Even if their introduction on the market has been
revolutionary and the expert envision new kinds of
applications for fingerprint recognition (domotic,
health-care, id-card and credit-card protection, etc.)
their reduced lifetime and their high sensitivity to the
external environmental factors limit the wide-spreading
of these devices.
Ultrasonic Sensors
The ability to obtain images using ultrasound is based
upon the reflection and transmission coefficients of
ultrasound as it propagates through media of varying
acoustic impedance. What makes sound waves valuable
for the imaging of the ridge–valley pattern is that they
can both reflect and pass through objects. The charac-
teristics of sound waves make it possible for high-fre-
quencies to pass through substances and accurately
measure the ridges and valleys of a fingerprint even if
in presence of dirt, grease, ink, moisture, dye, or other
substances routinely found on fingers.
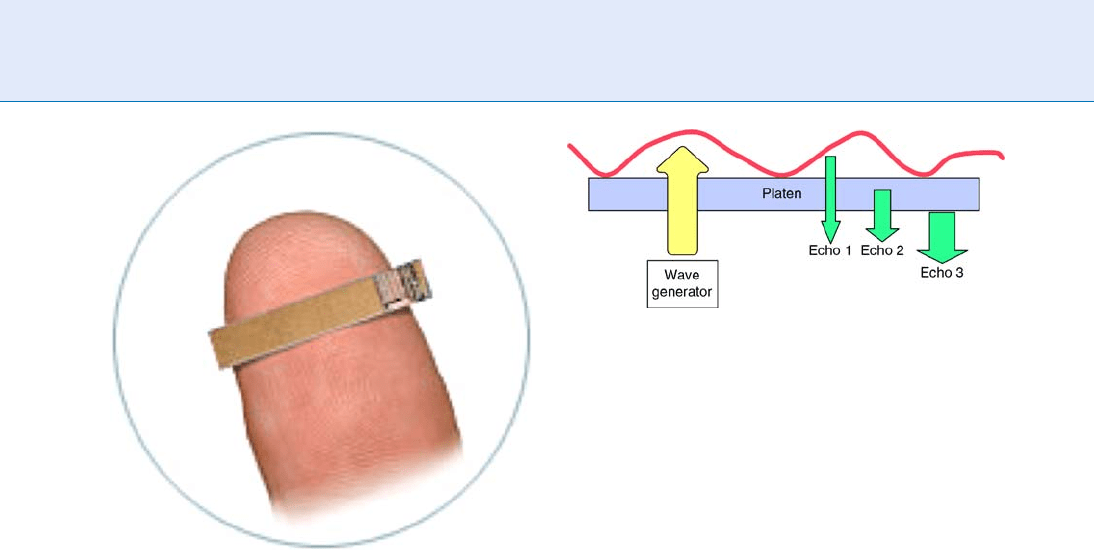
The capture principle of a ultrasonic device is high-
lighted in Fig. 7. An ultrasonic wave generator pro-
duces high-frequency sound impulses. These imp ulses
reflect on each material found on their path producing
echos. The strength of each echo depends on the mate-
rial and the shape of the object on which they were
generated. Special receptors are used to translate the
echos in an electrical signal.
Livescan imaging the fingerprints of children 5
years and younger is a technically challenging task,
since the ridge structure is usually very fine and con-
tains high ‘‘spatial frequencies,’’ meaning that the
ridges very close together. The spatial frequency
of the fingerprint directly determines the resolution
that the imaging device needs to accurately image the
finger. Most live-scan fingerprint scanners have been
designed to image adult fingers where a high-resolu-
tion scan is unnecessary. High-resolution ultrasonics is
the only technology that can reliably and repeatedly
capture clear and useful images of a young child’s
fingerprint.
Next Generation
Although most of the technologies mentioned earlier
are quite new (some of them are still in the prototyping
phase), the research and the development continues to
Fingerprint, Palmprint, Handprint and Soleprint
Sensor. Figure 7 Capture principle of an ultrasonic
capture device.
Fingerprint, Palmprint, Handprint and Soleprint
Sensor. Figure 6 An example of sweep sensor.
542
F
Fingerprint, Palmprint, Handprint and Soleprint Sensor

bring new ideas to this field. The study of the physiol-
ogy and the formation of the furrow pattern allowed
to propose new fingerprint and palmprint capture
approaches. It is important to mention here the Opti-
cal Coherence Tomography (OCT) which is an inter-
ferometric, noninvasive, optical tomographic imaging
technique offering millimeter penetration (approxi-
mately 2–3 mm in tissue) with micrometer-scale axial
and lateral resolution. OCT is like an optical version of
ultrasound imaging. The technique is already routinely
used in medicine, but has not had a forensic applica-
tion until now. The technique provides a transparent
3D structural picture by sending light though the pat-
tern of natural secretions left on a surface by a finger
and combining the reflected beam w ith a ‘‘reference
beam’’ produced by bouncing light from a laser off a
mirror. This produces an interference pattern at
a photodetector the same as those found in a digital
camera which can then be used to reconstruct an image
of the original fingerprint.
This tech nology together with multispectral and
touchless imag ing must be still further developed to
demonstrate their superiority with respect to the FTIR
approach that still remains the most used method to
capture fingerprints and palmprints.
Summary
Livescan furrow sensors represent a family of devices
used to capture fingerprints, palmprints, handprints,
and soleprints. The same anatomical characteristics of
the skin present on finger tips, palms, and soles allow
the use of the same tech nology for the capture of these
biometric treats.
The ink-on-paper method is first method used to
capture fingerprints and palmprints. Optical devices
try to overcome the inconvenience of the ink on the
skin and provide a good alternative method to the
legacy ink-on-paper. Solid-state sensors are very at-
tractive for their very small size and reduced costs,
but they can only be used to capture fingerprints.
Moreover, environmental factors limit the life time of
these devices.
Multispectral and touchless imaging technologies try
to overcome the limitation of the optical devices, but
their relatively higher costs and very low interoperability
with legacy technology limit their wide-spreading.
Related Entries
▶ Biometric Recognition
▶ Biometric Sensor and Device, Overview
▶ Fingerprint Recognition, Overv iew
▶ Fingerprint Verification
References
1. Ashbaugh, D.R.: Quantitative-Qualitative Friction Ridge Analy-
sis: An Introduction to Basic and Advanced Ridgeology. CRC,
Boca Raton (1999)
2. Criminal Justice Information Services Division: Electronic Finger-
print Transmission Specification. Department of Justice (1999)
3. Rowe, R.K., Nixon, K.A.: Fingerprint enhancement using a mul-
tispectral sensor. In: Proceedings of SPIE Conference on Biomet-
ric Technology for Human Identification, vol. 5779. pp. 81–93.
Orlando, USA (2005)
4. Rowe, R.K., Corcoran, S.P., Nixon, K.A., Ostrom, R.E.: Multi-
spectral Imaging for Biometrics. In: Proceedings of SPIE Con-
ference on Spectral Imaging: Instrumentation, Applications, and
Analysis, vol. 5694, pp. 90–99. Orlando, USA (2005)
5. Rowe R.K., Nixon, K.A., Butler, P.W.: Advances in Biometrics.
Sensors, Algorithms and Systems, chap. Multispectral Finger-
print Image Acquisition. Springer, Berlin (2008)
6. Parziale, G.: Advances in Biometrics. Sensors, Algorithms and
Systems, chap. Touchless Fingerprint Technology. Springer,
Berlin, New York, USA (2008)
7. Parziale, G., Diaz-Santana, E.: The surround imager: a multi-
camera touchless devide to acquire 3D rolled-equivalent finger-
prints. In: Proceedings of IAPR International Conference on
Biometrics (ICB), pp. 244–250. Hong Kong, China (2006)
8. Parziale, G., Bishof, H.: Image reconstruction and on-the-fly
minutiae extraction of fingerprints acquired with sweep sensors.
In: Proc. of 28th Workshop of the Austrian Association of
Pattern Recognition, pp. 241–248. Austria (2004)
9. Clausen, S.: Advances in Biometrics Sensors, Algorithms and
Systems, chap. A single-line AC capacitive fingerprint swipe
sensor. Springer, New York, USA (2008)
Fingerprints Hashing
JEAN-FRANC¸OIS MAINGUET
Grenoble, France
Synonyms
Biometric encryption; Cancelable biometrics; Finger-
print encryption; Fuzzy extractor; Fuzzy vault; Intri-
cated biometrics
Fingerprints Hashing
F
543
F
Definition
Fingerprint hashing is merging fingerprint recognition
and cryptographic methods. The aim is to perform a
recognition using fingerprint while, at the same time,
hiding the private information related to the finger-
print, thus enabling public fingerprint templates.
Introduction
Keeping a database in a safe place is not easy. Even with
good encryption methods and special care, databases
containing sensitive information, such as bank account
numbers, are vulnerable to being compromised.
Nobody wants something like that to happen when
dealing with fingerprint identification.
Security of a fingerprint-based system can be
divided into two main areas:
1. The electronic security, which poses the question:
‘‘Is the electronic system, at the other end of the
wires, a real trustful authorized fingerprint system ?’’
2. The liveness securit y, which asks a different ques-
tion: ‘‘Is the object touching the sensor a real finger,
alive and connected to a living person?’’
Liveness security is not addressed in this essay.
Fingerprint hashing is part of the electronic security
solution and deals with encryption.
Any bio metric system requires the storage of
a template (or reference). For fingerprint systems, the
most common method consists in storing the minu-
tiae. This information is considered as private infor-
mation and should be protected and ciph ered, not only
for privacy reasons, but also against template replace-
ment. This prevents a hacker from replacing the
owner’s minutiae, or using reverse engineering to get
the minutiae locations and create a fake fingerprint.
Even if biometric data cannot be considered as secret
(they are public information in its cryptographic sense,
always hiding ones face or voice is impossible), it is
important to protect biometric data and the additional
data that goes with them (name, bank account or
whatever).
The template storage problem is generally solved
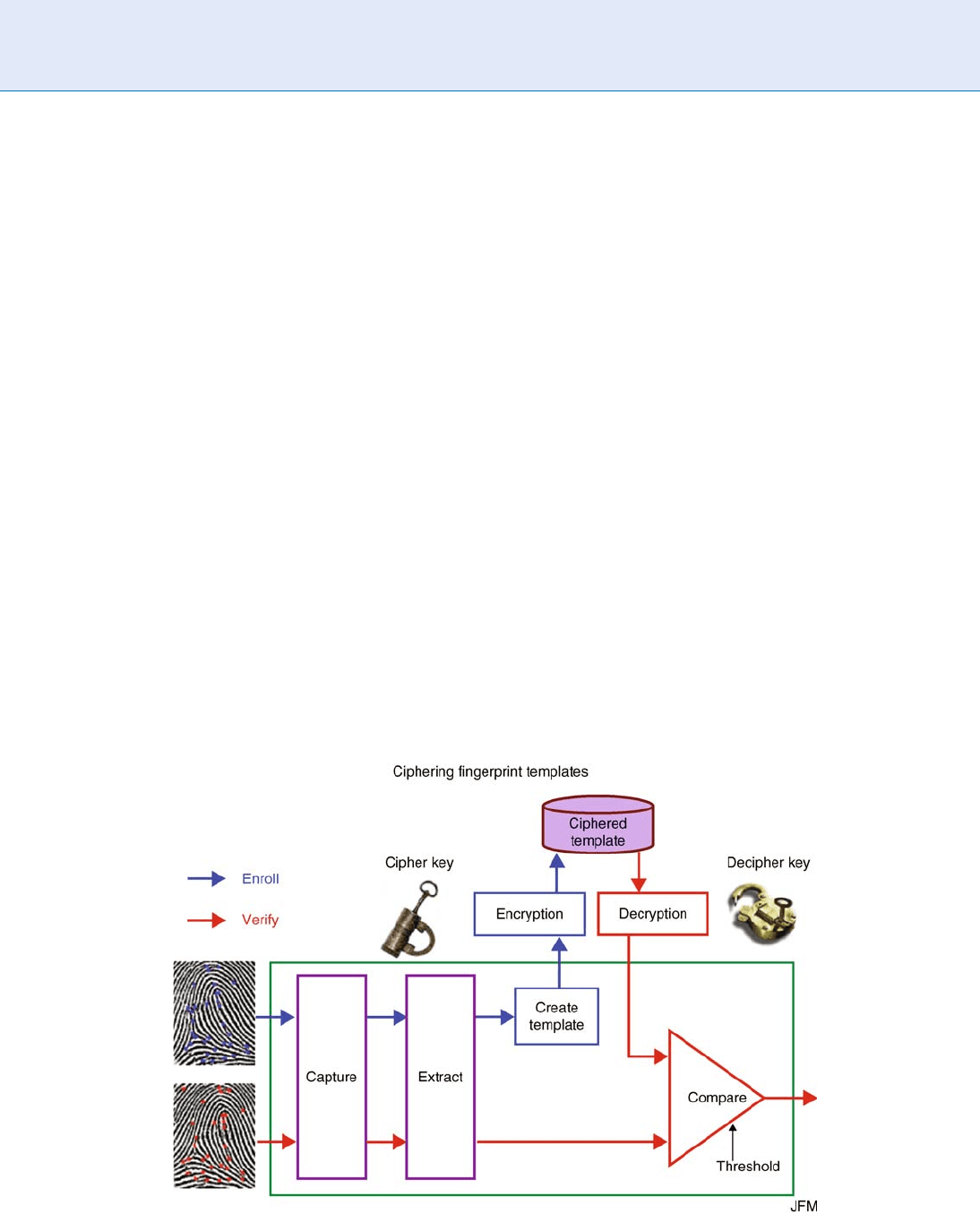
using encryption. A template database can be created
and protected using a single key pair (Fig . 1). Everything
is fine up to the date when the key is compromised or
badly protected, allowing hackers to access the data.
However, in the case of fingerprints, this is ones very
private information that is stored, and so it seems
desirable to have an even better security scheme.
Fingerprints Hashing. Figure 1 Protecting fingerprint templates: Key is not protected.
544
F
Fingerprints Hashing
Another problem occurs when one tryies to create a
system enabling encryption/decryption features (like
▶ Pretty Good Privacy (PGP)). One needs to protect
the access to the encryption/decryption module, which is
done using a passwor d . If one tries to replace the pass-
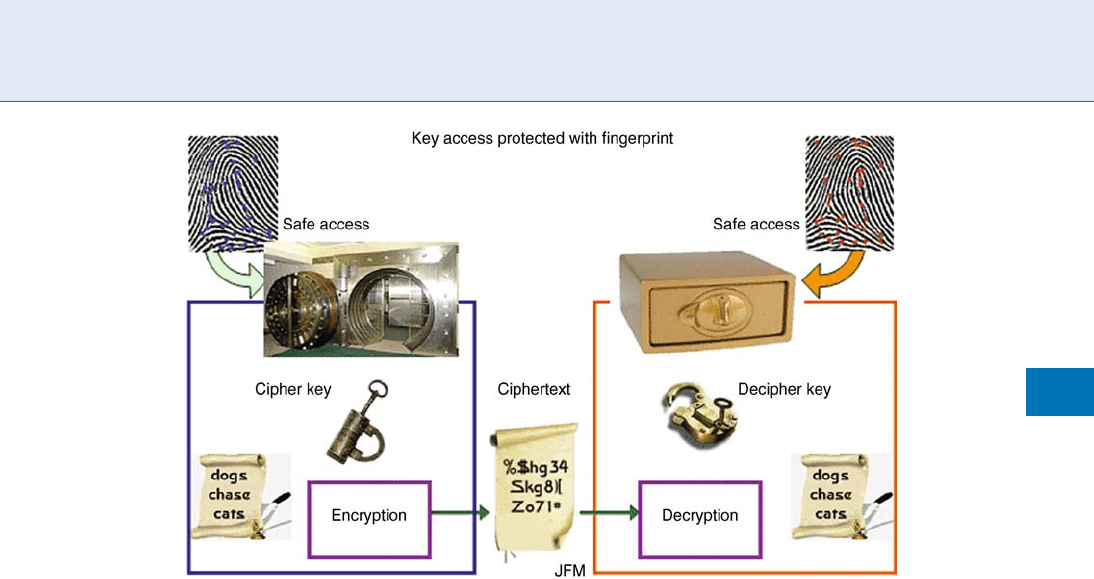
word with a fingerprint (Fig. 2), then one faces the
problem of protecting the template, and cannot use
the encryption/decryption scheme, because it is not yet
enabled! It is the same problem as ‘‘you cannot put the key
of the safe inside the safe itself.’ ’ One needs another safe.
There is also an additional problem from a secur ity
point of view. The result of matching is only one bit of
information that is easy to find and hack (too low
entropy). It would be better to eliminate this weakness.
Desirable Features, Definitions
A better finge rprint system includes:
1. The storage of the template (minutiae) in a nonre-
versible way. It is still possible to perform a match,
but it is impossible to recover the original minutiae
and impossible to derive the secret key.
2. It is possible to revoke (cancel) a template. If a
template is not to be used anymore, it is possible
to forbid its use and create a new one.
3. There is no step with a single yes/no bit
corresponding to the match/no match result.
Properties #1 and #2 are generally linked, because it
would be very impractical and dangerous to use a
transform that is unique. Ea ch individual would have
a unique number ID for his or her whole life, impossi-
ble to change.
Fingerprint hashing is the use of a non-reversible
transform (similar to a hash function) over a finger-
print. It is also called ‘‘cancellable biometrics,’’ because
it is possible to cancel or to revoke the template.
Fingerprint hashing involves using some kind of cryp-
tographic scheme, similar to a hash function, but it is
not a hash function.
Property #3 requires a stronger merge between
biometrics and cry ptography. Having all the properties
at the same time is pretty hard to achieve and to prove,
but has been originally proposed under the name of
‘‘Biometric Encryption’’ [1, 2 ]. Unfortunately, ‘‘bio-
metric encryption’’ can be a simple combination of a
biometric template and a simple encryption scheme.
But it is much more; it is a real merge. In quantum
cryptography, the word ‘‘
▶ intricated’’ is used to des-
ignate the non-separable nature of some properties in
quantum mechanics, and so ‘‘Intricated Biometrics’’
seems a better designation.
Fingerprints Hashing. Figure 2 Protecting access to cryptographic secret keys using a fingerprint system: Fingerprint
template is not protected.
Fingerprints Hashing
F
545
F
Cancelable Biometrics
Fingerprint hashing seems pretty close to password
protection. A password is protected using a hash func-
tion, which is basically a method to transform some
data into a relatively small number, the hash value,
sometimes called fingerprint (which causes confu-
sion), because of its uniqueness property (no collision
should occur). A hash function is not reversible, and in
most cases, some original data is lost as the result-
ing hash value is much shorter. This works well for
password storage. You just need to apply the same hash
function to the proposed password and perform a bit-
to-bit comparison for checking. It is not useful to
regain access to the original password.
Unfor tunately, this scheme cannot apply to a fin-
gerprint, because you never enter exactly the same
fingerprint image. Every acquisition is different, and
usual hash functions will return a different value,
forbidding a further comparison. The problem is
much more complex as it needs to be accepted that
there will be some variabili ty of the data. Fingerprint
hashing must use a non-reversible transform like a
hash function, but the comparison stops here. The
other properties of a hash function, such as fixed
length and uniqueness, are not required, but there
needs to be a comparison, a match at the end, as
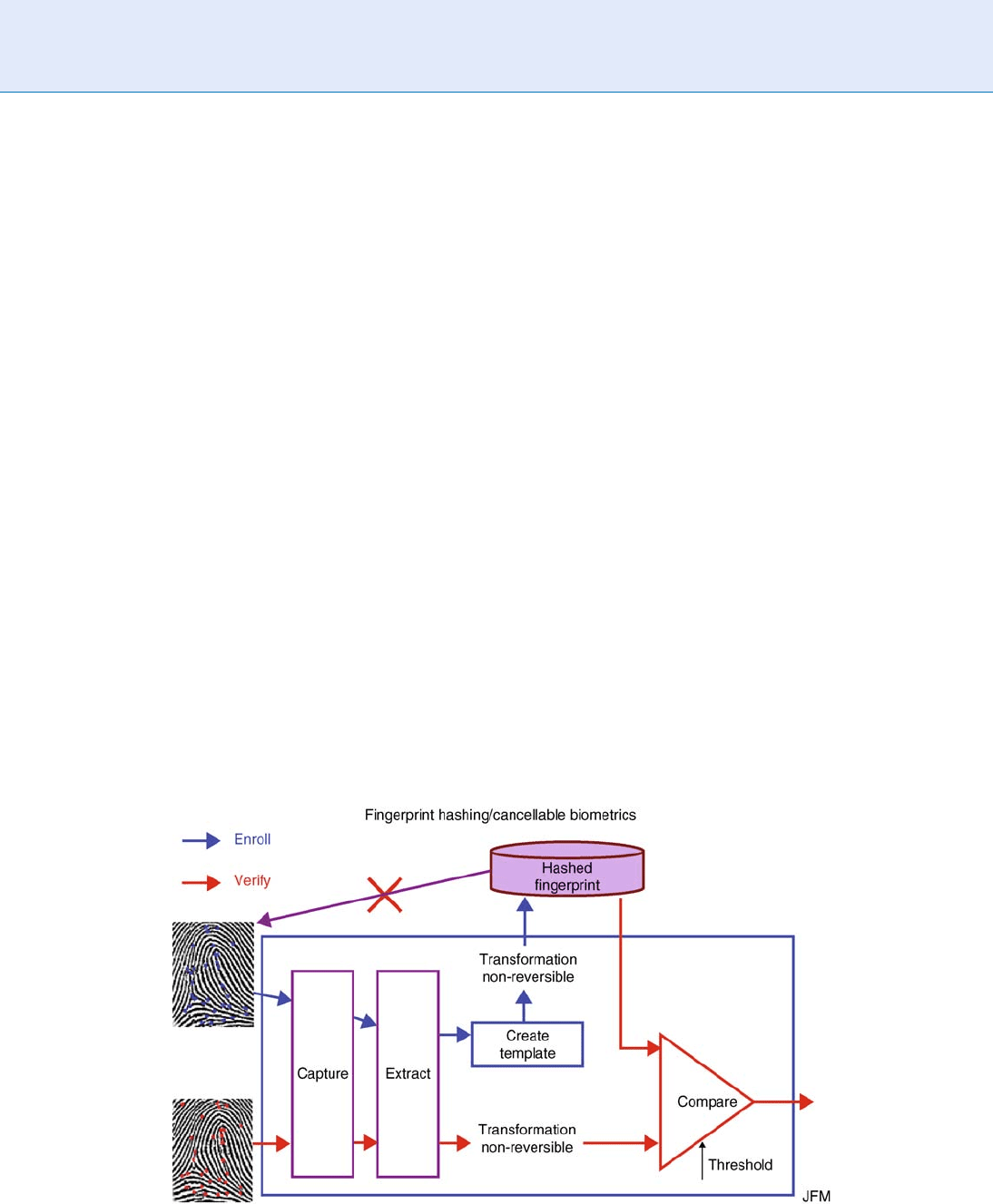
depicted in Fig. 3.
General concepts related to cancelable biometrics
have been discussed by Ratha et al. [3]. Davida et al. [ 4]
added data to create a non-reversible template. Lin-
nartz and Tuyls [5] proposed the use of specific shield
functions before a hash function.
Lumini and Nanni [6] proposed the BioHash, a
combination of a hash code, a Gram–Schmidt normal-
ization and using a Hamming distance for comparison.
This has been tested using the FVC-2002 fingerprint
database.
Boult et al. [7] proposed another scheme called
BioToken, and also tested on the FVC-2002 and 2004
fingerprint datab ases, which showed some enhance-
ments of the accuracy of the system.
As usual in cryptography, proving that the trans-
form is non-reversible or reversible with an extremely
long computation time is very hard to achieve.
Although there are some good reasons to believe that
some solutions exhibit the right properties, nothing is
mathematically proven yet. It took a long time for the
security of regular cryptographic schemes to be accepted,
and biometrics is in a similar situation, still in its infancy .
Intricated Biometrics
Cancelable biometrics shows interesting features,
but still shows the potential weakness of the
Fingerprints Hashing. Figure 3 Fingerprints hashing/cancellable biometrics: It is not possible to extract the original
biometric data from the template as the transform is non-reversible.
546
F
Fingerprints Hashing
match/no-match bit. This type of weakness may not be
as critical when speaking of a physical or logical access,
because of the need of a go/no go answe r. But in most
cases, the aim of the biometrically enabled system is to
provide a service, and secure systems always use some-
where a cryptographic key when a transmission is
involved in a non-secured environment.
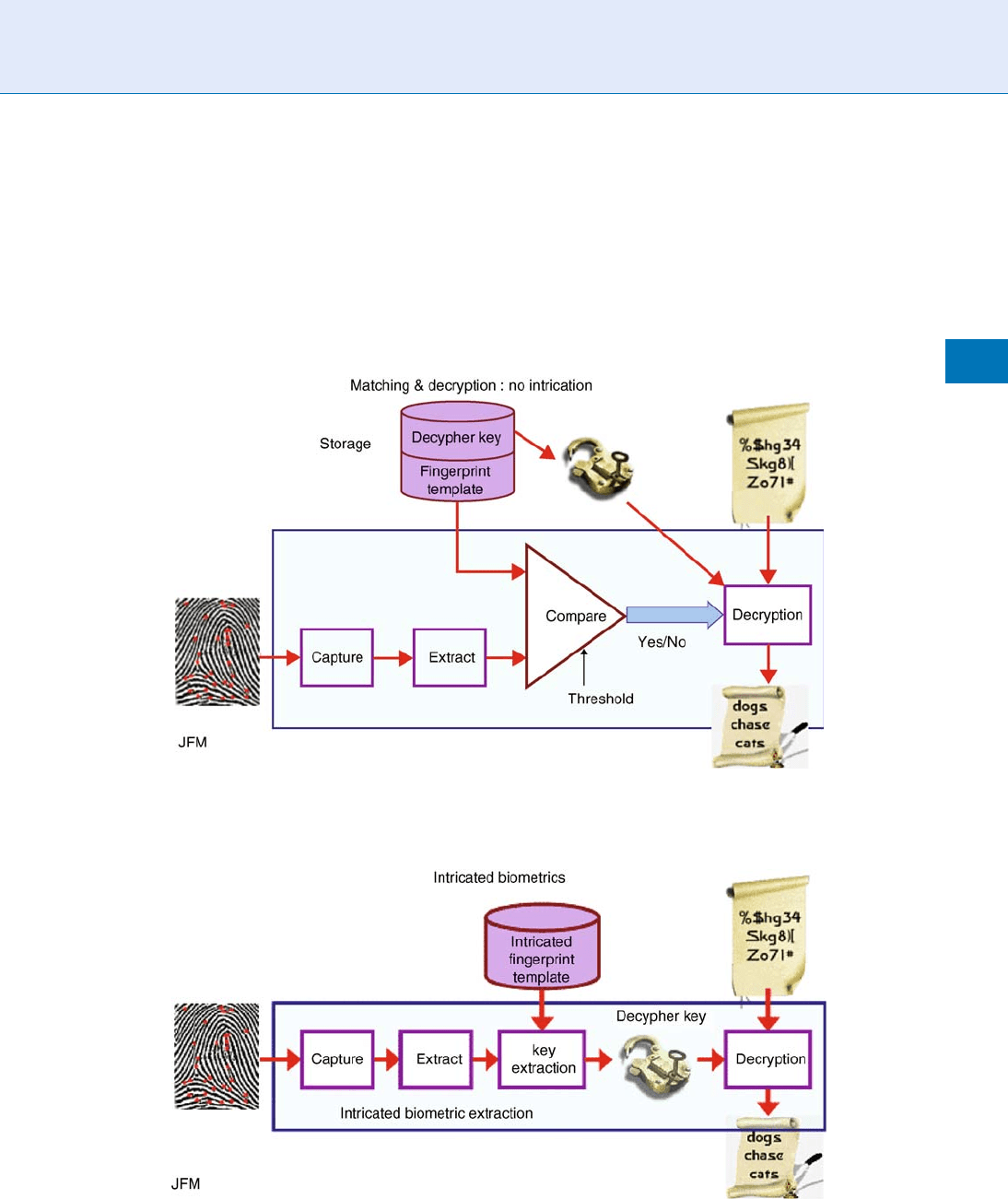
A simple scheme use s the result of the match to
enable the decipher key, as shown in Fig. 4. The
template and the key are not protected. This requires
external means; another secret key and method. There
is still the one bit matc h/no match result. Intricated
biometrics proposes to merge the decipher key with
the template, so that neither the biometric template
(the minutiae) nor the decipher key can be obtained
from the stored template alone; they are intricated
(Fig. 5). The intricated biometric template can be
stored anywhere, even in a non-secured area.
Fingerprints Hashing. Figure 4 A simple use of biometrics to use a secret key: fingerprint and secret key are not yet
protected, and the 1-bit match/no match still exists.
Fingerprints Hashing. Figure 5 Intricated biometrics: It is not possible to get the secret key and the original
fingerprint data from the intricated fingerprint template, and the extracted key appears only for a short while for
deciphering. The 1-bit match/no match step is eliminated.
Fingerprints Hashing
F
547
F

When the decipher key is to be used, t he live
fingerprint can be scanned. If the extracted minutiae
corresponds to the stored template, then the rig ht
decipher key will be regenerated, immediately used
to decipher the message (this is the service) and
destroyed (the key never leaves th e secure area). If
the extracted minutiae are not the genu ine min utiae,
a key is still generated but not the correct key. The
message is then incorrectly deciphered, giv ing a
meaningless result. At the end, there is no informa-
tion revealed, which is a very good p roperty o f
a secure system, and it is not p ossible to apply a
scheme such as hill-climbing, based on access of the
matching score.
It is possible to reach these objectives, but it is hard
to achieve and to prove, especially for fingerprints.
Cryptography is Accurate; Biometrics is
Fuzzy
In cancelable biometrics, a function similar to a
hash function had to be applied, but the data varia-
bility was a problem. Intricated biometric involves
re-generating a cryptographic key and the same prob-
lem. Every bit must be correct; no error is allowed. With
biometrics, there is always some uncertainty. Each time
a fingerprint is scanned or applied to a sensor, it may
not be exactly the same area. The person may have a new
cut or scar; the finger could be dirty, wet, or dry.
A par tial solution would be to extract a stable
sequence from a fingerprint image, always the same,
and then combine it with a cryptographic key. This is
like extracting a stable signal from a noisy, fuzzy envi-
ronment. Some research proposed the use of error-
correcting code, with the so-called ‘‘fuzzy extractor’’
[8, 9] that can be applied to different biometric mod-
alities, and then specifically over fingerprint databases
[10, 11].
The ‘‘
▶ fuzzy vault’’ was proposed in 2002 by Juels
et al. [12]. The proposal involved secret being merged
with biometric data such as minutiae that does not
need to be in a specific order.
▶ Chaff points [ 13] are
added to hide the genuine minutiae. The experiment
was later enhanced using lattice [ 14], tested on the
FVC-2002 database and enhanced with helper data by
Uludag et al. [15, 16].
Soutar et al. [2] proposed in 1999 using filters to
extract stable characteristics of the fingerprint and then
merged them with a secret.
One example scheme is:
Enroll
A set of M minutiae is extracted from a
fingerprint.
A secret key is divided into M pieces of data;
each piece is linked to one minutiae.
Random chaff po ints are added, corresponding
to non-existing minutiae and wrong pieces of
secret key.
Recognition
A live set of N minutia e are extracted from a live
fingerprint.
The matching minutiae enable extraction of the
correct piece of the secret key.
As the live minutiae may not be exactly the same, it
is important to introduce some kind of redundancy for
the secret key. A subset of the M enrolled minutiae is
needed to perform a match. Lagrange interpolation has
been proposed to recover the full secret key, with the
advantage of not depending on the order of the points
or minutiae.
But some problems arise:
Brute force attack: It is important to add enough
chaff points to hide the genuine points and to
create too many possible combinations for a brute
force attack to succeed.
Generating chaff points is not a simple operation,
becausecaremustbetakentoavoidflaws.The
chaff points must be indistinguishable from gen-
uine points. It is a similar problem to random
number generators, wher e it is difficult to pro ve
that they are really random. Alwa ys using the same
chaff points would make it too easy to find them.
Matching minutiae for key extractio n will likely
require more computation.
Chaff points may lead to wrong alignments,
especially with poor fingerprints, making min-
utiae matching less robust.
Intricated fingerprint template requires more
memory space than a simple template (but
another key and program would be needed for
protection).
Conclusion
Fingerprint hashing (intricated biometrics) seems to
be the ultimate protection scheme. This is not a proven
technolog y yet, but achieving the objectives would lead
548
F
Fingerprints Hashing

to a better protection of privacy without worrying
about databases.
Related Entries
▶ Encryption, Biometric
▶ Fake Finger Detection
▶ Fingerprint Features
▶ Fingerprint Matching, Automatic
▶ Fingerprint Templates
References
1. Cavoukian, A., Stoianov, A.: Biometric encryption: A positive-
sum technology that achieves strong authentication, security
and privacy. White paper, Information and privacy commiss-
ioner of Ontario, March (2007)
2. Soutar, C., Roberge, D., Stoianov, A., Gilroy, R., Vijaya Kumar,
B.V.K.: Biometric Encryption, chap. 22, McGraw-Hill (1999)
3. Ratha, N.K., Connell, J.H., Bolle, R.M.: Enhancing security and
privacy in biometrics-based authentication systems. IBM Syst. J.
40(3), 614–634 (2001)
4. Davida, G.I., Frankel, Y., Matt, B.J., Peralta, R.: On the relation of
error correction and cryptography to an off-line biometric based
identification scheme. In: Proceedings of the Workshop on Cod-
ing and Cryptography, Paris, France, pp. 129–138 (1999)
5. Linnartz, J.P., Tuyls, P.: New shielding functions to
enhance privacy and prevent misuse of biometric templates.
In: Proceedings of the Fourth International Conference on
Audio and Video based Biometric Person Authentication, Guild-
ford, UK, pp. 393–402 (2003)
6. Lumini, A., Nanni, L.: An improved biohashing for human
authentication. Pattern Recognit. 40, 1057–4065 (2007)
7. Boult, T.E., Scheirer, W.J., Woodworth, R.: Revocable Fingerprint
Biotokens: Accuracy and Security Analysis. In: Proceedings of
the IEEE Conference on Computer Vision and Pattern Recogni-
tion (CVPR’07), Minneapolis, USA, pp. 1–8, 17–22 June (2007)
8. Dodis, Y., Reyzin, L., Smith, A.: Fuzzy extractors: How to gener-
ate strong keys from biometrics and other noisy data. In:
Proceedings of the Eurocrypt 2004, pp. 523–540 (2004)
9. Burnett, A., Byrne, F., Dowling, T., Dury, A.: A biometric identity
based signature scheme. In: Proceedings of the Applied Cryptog-
raphy and Network Security Conference, New York, USA (2005)
10. Costanzo, C.R.: Biometric cr yptography: Key generation using
feature and parametric aggregation. Online techreport, School
of Engineering and Applied Sciences, Department of Computer
Science, The George Washington University, October (2004)
11. Al-Tarawneh, M.S., Khor, L.C., Woo, W.L., Dlay, S.S.: Crypto key
generation using contour graph algorithm. In: Proceedings of
the 24th IASTED International Multi-Conference Signal Proces-
sing, Pattern Recognition and Applications, Insbruck, Austria,
February (2005)
12. Juels, A., Sudan, M.: A fuzzy vault scheme. In: Lapidoth, A.,
Teletar, E. (eds.) Proceedings of the IEEE International Sympo-
sium on Information Theory, p. 408. IEEE Press (2002)
13. Chang, E.-C., Li, Q.: Hiding secret points amidst Chaff. In:
Proceedings of the Eurocrypt, Saint Petersburg, Russia (2006)
14. Zheng, G., Li, W., Zhan, C.: Cryptographic key generation from
biometric data using lattice mapping. In: Proceedings of the 18th
International Conference on Pattern Recognition (ICPR’06),
Washington, DC, USA, pp. 513–516. IEEE Computer Society
(2006)
15. Uludag, U., Jain, A.K.: Fuzzy fingerprint vault. In: Proceedings
on Workshop: Biometrics: Challenges Arising from Theory to
Practice, August 2004, pp. 13–16 (2004)
16. Uludag, U., Jain, A.: Securing fingerprint template: Fuzzy vault
with helper data. In: Proceedings of the 2006 Conference on
Computer Vision and Pattern Recognition Workshop, June
2006, pp. 163–170 (2006)
First Level Detail
This reflects the general flow of the papillary ridges
which may form certain patterns such as arches, loops,
whorls, and deltas.
▶ Fingerprint Matching, Manual
Fisher Criterion
Fisher criterion is a discriminant criterion function
that was first presented by Fisher in 1936. It is defined
by the ratio of the between-class scatter to the within-
class scatter. By maximizing this criterion, one can
obtain an optimal discriminant projection axis. After
the sample being projected on to this projection axis,
the within-class scatter is minimized and the bet ween-
class scatter is maximized.
▶ Non-linear Techniques for Dimension Reduction
Fixed Pattern Noise
It is characterized by the same pattern of ‘‘hot’’ pixels
occurring with images taken under the same condi-
tions of temperature and exposure.
▶ Face Device
Fixed Pattern Noise
F
549
F
