Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.

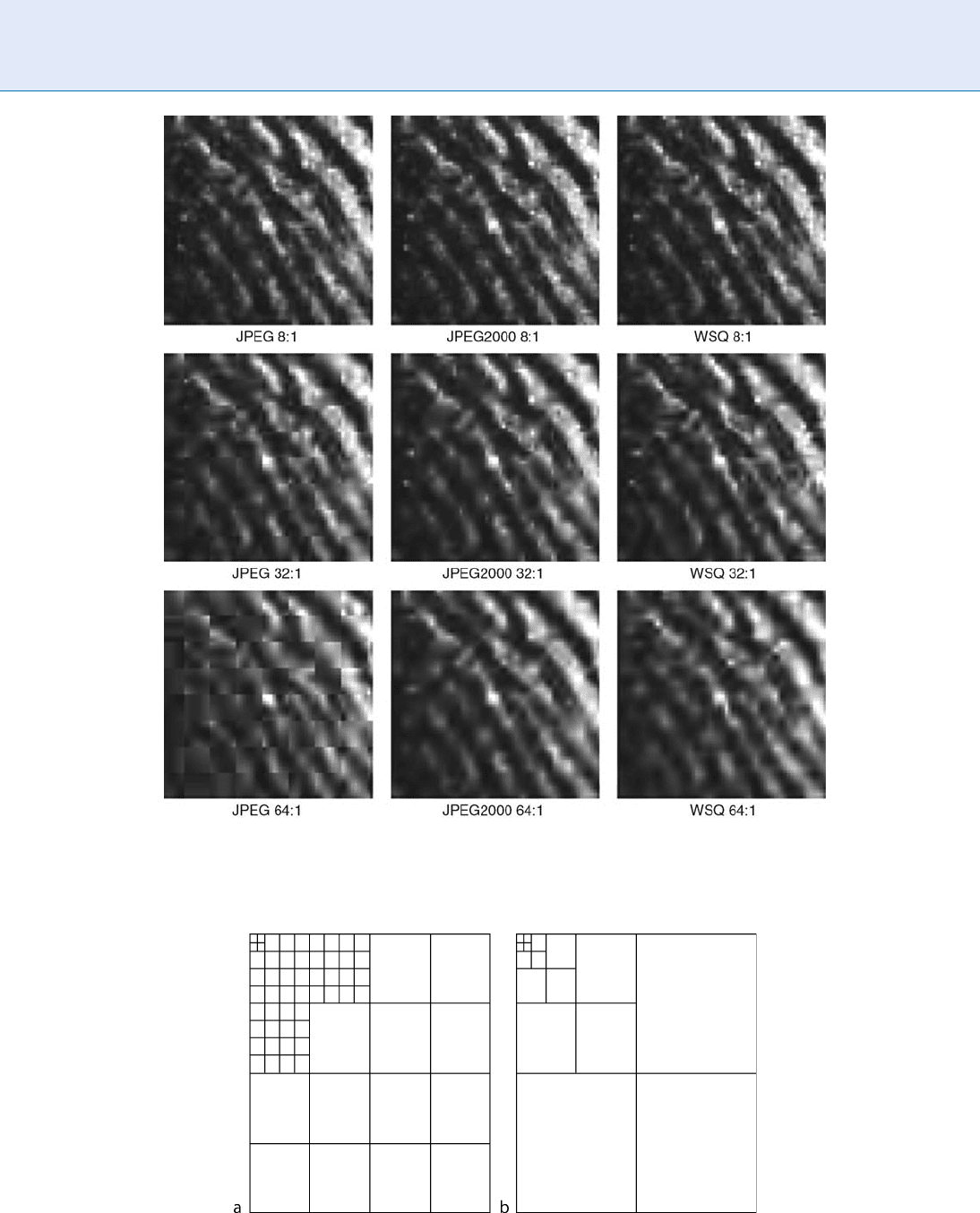
Fingerprint Compression. Figure 2 Comparative example of compressed image of 64 64 pixel region of latent.
Fingerprint Compression. Figure 3 Schematics of decomposition trees, (a) WSQ and (b) JPEG2000 (default).
450
F
Fingerprint Compression

lengthened middle interval. For the last coding step,
WSQ employs Huffman entropy coding while JPEG2000
uses scalar arithmetic or trellis-coded quantization.
Much of the flexibility and power of the JPEG2000
comes from the Embedded Block Coding with Opti-
mized Truncation (EBCOT) algorithm. Wavelet coeffi-
cients from small blocks of the image are processed using
the EBCOT algorithm which adapts the quantizer based
on the statistics of the source image at the bit- plane
level. These blocks are tiled with integrated header infor-
mation concerning with coding details, and further
quantization can be performed on the final bit-stream.
The flexibility of this final stage in JPEG2000 encoding
greatly assists in providing more optimal compression.
WSQ employs a much simpler approach and coding
details is calculated for each image and the coefficients
included in the file header.
Fingerprint Compression Performance
WSQ has proved to be satisfactory at compressing
fingerprint images by factors up to about 20, though
the original requirement was to compress to 0.75 bpp
(i.e., 10.7:1 compression). Watson and Wilson [10 ]
report that experiments using WSQ compressed images
with three different matching systems under the con-
ditions that a FAR is 0.001 is maintained and the
maximum reduction in the TAR of less than 0.01 is
permitted, then there is little effect on performance for
compression ratios less than 20:1. A few studies have
compared the relative merits of WSQ and JPEG2000.
Figueroa-Villanueva et al. [11] showed a significant
improvement for JPEG2000 over WSQ at 0.75 bpp
compression in terms of PSNR and Receiver Operating
Curves (ROCs) for different sources namely, capaciti ve
sensor, optical sensor, and scanned inked prints.
A study of JPEG2000 and WSQ interoperability [12]
concluded that JPEG2000 produced a slightly lower
quality reconstructed image compared to WSQ for
the same file size. Most studies have focused on coding
high-quality inked prints or live print capture from
various sources, and not on poorer quality latents. One
study that involved latents and performance on an
operational AFIS system [13] concluded that for com-
pression ratios less than 32:1, JPEG2000 consistently
produced higher identification rates than WSQ. There
was also strong indication that moderate degrees of
compression facilitated improved identification rates
under normal operating procedures than uncom-
pressed latent images.
Current national and international standards
[14, 15] recommend that WSQ encoding is used
for 500 ppi fingerprint images with compression lim-
ited to 15:1; but for images with resolutions greater
than 500 ppi, 15:1 JPEG2000 should be employed.
The UK national fingerprint system permits latents
to be transmitted and submitted to Ident 1 at 15:1
JPEG2000.
Conclusions
It may appear that satisfactory standards exist for com-
pressing fingerprint images, certainly for the normal
operational requirements associated with the effective
transmission and storage of reference and livescan
images. General enhancements in providing lower-
cost, higher-capacity mass storage and increased band-
width across both fixed and wireless data networks will
reduce the pressure to develop new compression stan-
dards. However, fingerprints are an unusual and fairly
well-defined class of image. Compression schemes such
as JPEG2000 have been developed to cope well for a
very wide variety of imagery and WSQ, though based
on a principled consideration of the statistical proper-
ties of fingerprints, was developed prior to many more
general advances in image compression. Recent propo-
sals for improved fingerprint image compression are
generally based on wavelet transformations but with
more effective decomposition trees, optimized filter
structures and coefficients through the use of genetic
algorithm optimization, and vector quantization.
The relationship between image enhancement and com-
pression is not fully understood. There are sugges-
tions that the filtering that occurs during compression
may be advantageous in increasing identification, espe-
cially for latents. This is an avenue that needs to be
explored further.
Related Entries
▶ Fingerprint Image Enhancement
▶ Fingerprint Matching, Automatic
▶ Fingerprint Matching, Manual
▶ Fingerprint Recognition, Overv iew
Fingerprint Compression
F
451
F

References
1. Komarinski, P.: Automated Fingerprint Identification Systems
(AFIS). Elsevier Science Technology (2005)
2. Scientific Working Group on Friction Ridge Analysis, Study and
Technology (SWGFAST): Friction Ridge Digital Imaging Guide-
lines, 1 edn. (2001). URL http://www.theiai.org/guidelines/
swgfast/
3. Ghanbari, M.: Image compression to advanced video coding. In:
Standard Codecs, Telecomunications Series 49. Institution Elec-
trical Engineers (2003)
4. Burrus, C., Guo, H., Gopinath, R.: Introduction to Wavelets and
Wavelet Transforms: A Primer. Prentice Hall (1997)
5. Vetterli, M., Kovacevic, J.: Wavelets and subband coding. Prentice-
Hall,Inc.(1995)
6. Nill, N.: Image quality evaluation - image quality of fingerprint
(IQF). Tech. rep., The MITRE Corporation (2007)
7. Hopper, T., Preston, F.: Compression of grey-scale fingerprint
images. In: Proceedings DCC ’92. Data Compression Confer-
ence, pp. 309–318 (1992). DOI 10.1109/DCC.1992.227450
8. Skodras, A., Christopoulos, C., Ebrahimi, T.: The JPEG 2000 still
image compression standard. IEEE Signal Process Mag 18(5),
36–58 (2001)
9. Antonini, M., Barlaud, M., Mathieu, P., Daubechies, I.: Image
coding using wavelet transform. IEEE Trans Image Process 1(2),
205–220 (1992)
10. Watson, C., Wilson, C.: Effect of image size and compression on
one-to-one fingerprint matching. Tech. rep., National Institute
of Standards and Technology (2005)
11. Figueroa-Villanueva, M., Ratha, N., Bolle, R.: A comparative
performance analysis of JPEG 2000 vs. WSQ for fingerprint
image compression. In: Audio- and Video-Based Biometric
Person Authentication, Lecture Notes in Computer Science,
p. 1059. Springer Berlin/Heidelberg (2003)
12. Lepley, M.: JPEG 2000 and WSQ image compression interoper-
ability. Tech. rep., The MITRE Corporation (2001)
13. Allinson, N.M., Sivarajah, J., Gledhill, I., Carling, M., Allinson, L.J.:
Robust wireless transmission of compressed latent fingerprint
images. **IEEE Transactions on Information Forensics and Secu-
rity 2(3), 331–340 (2007). DOI 10.1109/TIFS.2007.902684
14. American National Standards Institute: American national stan-
dard for information systems - data format for the interchange
of fingerprint, facial, & other biometric information. URL
http://fingerprint.nist.gov/standard/
15. International Organization for Standardization: Information
technology - biometric data interchange formats - part 4: Finger
image data. URL http://www.iso.org/
Fingerprint Contrast Enhancement
▶ Fingerprint Image Enhancement
Fingerprint Corpora
▶ Fingerprint Databases and Evaluation
Fingerprint Data Interchange
Format
▶ Finger Data Interchange Format, Standardization
Fingerprint Databases and
Evaluation
FERNAN DO ALON S O -FERNANDEZ,JULIAN FIERREZ
Biometric Recognition Group – ATVS,
Escuela Politecnica Superior,
Universidad Autonoma de Madrid,
Campus de Cantoblanco, Madrid 28049, Spain
Synonyms
Fingerprint bench mark; Fingerprint corpora
Definition
Fingerprint databases are structured collections of fin-
gerprint data mainly used for either evaluation or
operational recognition purposes.
The fingerprints in databases for evaluation are
usually detached from the identity of the corres-
ponding individuals, are publicly available for research
purposes, and usually consist of raw fingerprint images
acquired with live-scan sensors or digitized from inked
fingerprint impressions on paper. These databases are
the basis for research in a utomatic fingerprint recogni-
tion, and together with specific experimen tal pro-
tocols, are the basis for a number of technology
evaluations and benchmarks. This is the type of finger-
print databases further developed here.
452
F
Fingerprint Contrast Enhancement

On the other hand, fingerprint databases for opera-
tional recognition are typically proprietary, usually in-
corporate personal information about the enrolled
people together with the fingerprint data, and can incor-
porate either raw fingerprint image data or some form
of distinctive fingerprint descriptors such as minutiae
templates. These fingerprint databases repres ent one
of the modules in operational automated fingerprint
recognition systems, and will not be addressed here.
Fingerprint Databases for Evaluation
Among all biometric techniques, fingerprint recogni-
tion is the most widespread in personal identification
due to its permanence and uniqueness [ 1]. Finger-
prints are being increasingly used not only in forensic
investigations, but also in a large number of conve-
nience applications, such as access control or online
identification [2].
The growth that the field has experienced over the
past two decades has led to the appearance of increas-
ing numbers of biometric databases for research and
evaluation purposes, either
▶ monomodal (one bio-
metric trait sensed) or
▶ multimodal (two or more
biometric traits sensed). Previous to the databases ac-
quired within the framework of the International Fin-
gerprint Verification Competition series, the only
large, publicly available datasets were the NIST data-
bases [3]. However, these databases were not well
suited for the evaluation of algorithms operating with
live-scan images [1] and will not be described here.
In this section, the authors present some of the most
popular publicly available biometric databases, either
monomodal or multimodal, that include the finger-
print trait acquired with
▶ live-scan sensors.
FVC Databases
Four international Fingerprint Verification Competi-
tions (FVC) have been organized in 2000, 2002, 2004
and 2006 [4, 5, 6, 7]. For each competition, four
databases were acquired using three different sensors
and the SFinGE synthetic generator [1]. Each database
has 110 fingers (150 in FVC2006) with eight impres-
sions per finger (12 in FVC2006), resulting in 880
impressions (1,800 in FVC2006). In the four competi-
tions, the SFinGe synthetic generator was tuned to
simulate the main perturbations introduced in the
acquisition of the three real databases.
1. In FVC2000 [4], the acquisition conditions were
different for each database (e.g., interleaving/not
interleaving the acquisition of different fingers, peri-
odical cleaning/no cleaning of the sensor). For all
the databases, no care was taken to assure a mini-
mum quality of the fingerprints; in addition, a
maximum rotation and a non-null overlapping area
were assured for impressions from the same finger.
2. In FVC2002 [5], the acquisition conditions were
the same for each database: interleaved acquisition
of different fingers to maximize differences in fin-
ger placement, no care was taken in assuring a
minimum qualit y of the fingerprints and the sen-
sors were not periodically cleaned. During some
sessions, individual s were asked to: (1) exaggerate
displacement or rotation or, (2) have their fingers
dried or moistened.
3. The FVC2004 databases [6] were collected with the
aim of creating a more difficult benchmark be-
cause, in FVC2002, top algorithms achieved accura-
cies close to 100% [6]. Therefore, more intra-class
variation was introduced. During the different ses-
sions, individuals were asked to: (1) put the finger
at slightly different vertical position, (2) apply low
or high pressure against the sensor, (3) exaggerate
skin distor tion and rotation, and (4) have their
fingers dried or moistened. No care was taken to
assure a minimum quality of the fingerprints and
the sensors were not periodically cleaned. Also, the
acquisition of different fingers were interleaved to
maximize differences in finger placement. Effects of
quality degradation in fingerprint images can be
observed in Fig. 1.
4. For the 2006 edition [7], no deliberate difficulties
were introduced in the acquisition as it was done in
the previous editions (such as exaggerated distor-
tion, large amounts of rotation and displacement,
wet/dry impressions, etc.), but the population was
more heterogeneous, including manual workers and
elderly people. Also, no constraints were enforced
to guarantee a minimum quality in the acquired
images and the final datasets were selected from a
larger database (the BioSec multimodal database
[8]) by choosing the most difficult fingers according
to a quality index, to make the benchmark suffi-
ciently difficult for an evaluation.
Fingerprint Databases and Evaluation
F
453
F

BIOMET Multimodal Database
Five different biometric modalities are present in the
BIOMET database [9]: audio, face image, hand image,
fingerprint and signature. This database was designed
with the additional goal of incl uding unusual sensors
(face images captured with an infrared camera and
with a 3D acquisition system). The database consists
of three different acquisition sessions. The number of
individuals participating to the collection of the data-
base was 130 for the first session, 106 for the second,
and 91 for the last one, resulting in 91 individuals who
completed the whole acquisition process. For finger-
print acquisition, an optical and a capacitive sensor
were used. During the first acquisition campaign, only
the optical sensor was used, whereas both the optical
and capacitive sensors were employed for the second
ant third campaigns. The total number of available
fingerprints per sensor in the BIOMET database is
6 for the middle and index fingers of each contributor.
MCYT Bimodal Database
A large biometric database acquisition process was
launched in 2001 by four Spanish academic institu-
tions within the MCYT project [10]. The MCYT data-
base includes ten-print ac quisition (MCYT Fingerp rint
subcorpus) and on-line signature (MCYT Signature sub-
corpus) samples of each individual enrolled in the data-
base. A total of 330 individuals were acquired in the four
institutions participating in the MCYT project. R eg ard-
ing the MCYT Fingerprint subcorpus, for each individ-
ual, 12 samples of each finger were acquired using
an optical and a capacitive sensor under differ ent con-
trol conditions. The MCYT database has been extended
with the comprehensive BiosecurID multimodal data-
base [11], which includes 8 different biometric traits
from 400 donors collected in 4 sessions separated in
time.
BioSec Multimodal Database
BioSec was an Integrated Project of the Sixth European
Framework Programme which involved over 20 part-
ners from nine European countries. The goal of BioSec
was to leverage the integration of biometrics in a wide
spectrum of everyday’s applications. One of the activ-
ities within BioSec was the acquisition of a multimodal
database. This database was acquired at four different
European sites and includes face, speech, fingerprint
and iris recordings. The baseline corpus [8] comprises
200 subjects with two acquisition sessions per subject.
The extended version of the BioSec database comprises
250 subjects with four sessions per subject (about
1 month between sessions). Each subject provided in
each session four samples of each of four fingers
(left and right index and middle). Fingerprints were
acquired using three different sensors. Some example
images are shown in Fig. 2.
BioSecure Multimodal Database
The acquisition of the BioSecure Multimodal Database
(BMDB) was jointly conducted by 11 European insti-
tutions participating in the BioSecure Network of
Excellence. [11] The BMDB is comprised of three
different datasets [12], namely:
1. Data Set 1 (DS1 ) , acquired over the Internet under
unsupervised conditions (i.e., connecting to an
Fingerprint Databases and Evaluation. Figure 1 Examples of quality degradation in fingerprint images due to factors
like low/high pressure, dryness/moisture, dirt, etc.
454
F
Fingerprint Databases and Evaluation

URL and following the instructions provided on
the screen).
2. Data Set 2 (DS2), acquired in a standard office
room environment using a PC and a number of
commercial sensors under the guidance of a human
supervisor.
3. Data Set 3 (DS3), acquired using two mobile
▶ hand-held devices under two acquisition con-
ditions (controlled-indoor and uncontrolled-
outdoor).
The three datasets of the BMDB include a common
part of audio and v ideo data. Additionally, DS2
includes signature, fingerprint, hand and iris data,
and DS3 includes signature and fingerprint data. The
three datasets were acquired in two different sessions
(approximately 2 months between them). Pending yet
to be distributed publicly, the BioSecure multimodal
database has approximately 1,000 subjects in DS1,
and 700 in DS2 and DS3. Fingerprint data in DS2
were acquired using an optical and a capacitive sensor.
Fingerprint data in DS3 were acquired with a PDA.
The databases MCYT, BiosecurID, BioSec, and Bio-
Secure have some commonalities that enable their
integration for specific research studies, e.g., on time
variability and sensor interoperability [12].
Fingerprint Evaluation Campaigns
The most important evaluation campaigns carried out
in the fingerprint modality are the NIST Fingerprint
Vendor Technology Evaluation (FpVTE2003) [13] and
the four Fingerprint Verification Competitions (FVC),
which took place in 2000 [4], 2002 [5], 2004 [6] and
2006 [7]. A comparative summary between FVC2004,
FVC2006 and FpVTE2003 is given Table 1. An impor-
tant evaluation is also the NIST Minutiae Interopera-
bility Exchange Test (MINEX) [14].
Fingerprint Verification
Competitions (FVC)
The Fingerprint Verification Competitions were orga-
nized with the aim of determining the state of the art
in fingerprint verification. These competitions have
received great attention both from academic and com-
mercial organizations, and several research groups
have used the FVC datasets for their own experiments
later on. The number of participants and algorithms
evaluated has increased in each new edition of the
FVC. Also, to increase the number of participants,
anonymous participation was allowed in 2002, 2004
and 2006. Additionally, the FVC2004 and FVC2006
were subdivided into: (1) open category and (2) light
category. The light category aimed at evaluating algo-
rithms under low computational resources, limited
memory usage and small template size.
For each FVC competition, four databases were
acquired using three different sensors and the SFinGE
synthetic generator [1]. The size of each database
was set at 110 fingers with eight impressions per
finger (150 fingers with 12 impressions per finger in
FVC2006). A subset of each database (all the impres-
sions from ten fingers) was made available to the
participants prior to the competition for algorithm
tuning. The impressions from the remaining fingers
were used for testing. Once tuned, participants
submitted their algorithms as executable files to the
evaluators. The executable files were then tested at the
evaluator’s site and the test data were not released until
Fingerprint Databases and Evaluation. Figure 2 Example fingerprint images of two fingers acquired with
three different sensors (from the BioSec baseline corpus). Fingerprint images of the same finger are shown for
a capacitive sensor (left of each subplot), an optical sensor (center) and a thermal sensor (right).
Fingerprint Databases and Evaluation
F
455
F
the evaluation concluded. In order to benchmark the
algorithms, the evaluation was divided into: (1)
▶ gen-
uine attempts: each fingerprint image is compared to
the remaining images of the same finger, and (2)
▶ im-
postor attempts: the first impression of each fing er is
compared to the first image of the remaining fingers.
In both cases, symmetric matches were avoided.
In Table 2, results of the best performing algorithm
in each FVC competition are shown. Data in the 2000
and 2002 editions were acquired without special
restrictions and, as observed in Table 2, error rates
decrease significantly from 2000 to 2002, demonstrating
in some sense the maturity of fingerprint verification
systems. However, in the 2004 and 2006 editions, it is
observed that error rates increase with respect to the
2002 edition due to the deliberate difficulties introduced
in the data, thus revealing that degradation of quality
has a severe impact on the recognition rates [15].
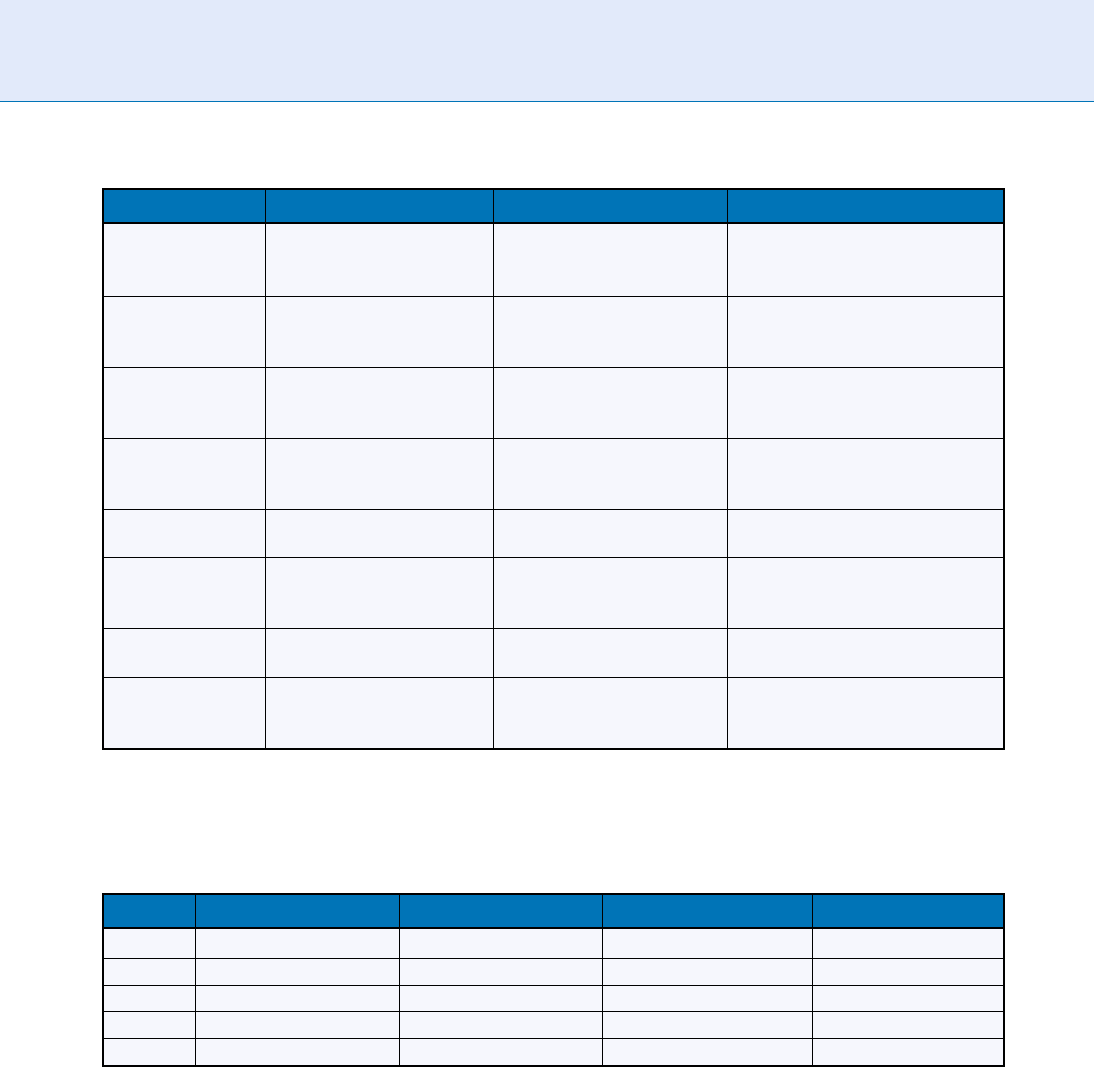
Fingerprint Databases and Evaluation. Table 2 Results in terms of equal error rate (EER) of the best performing
algorithm in each of the four databases of the FVC competitions
Database 2000 2002 2004 2006
DB1 (%) 0.67 0.10 1.97 5.56
DB2 (%) 0.61 0.14 1.58 0.02
DB3 (%) 3.64 0.37 1.18 1.53
DB4 (%) 1.99 0.10 0.61 0.27
Average 1.73 0.19 2.07 2.16
Fingerprint Databases and Evaluation. Table 1 Comparative summary between FVC2004, FVC2006 and FpVTE2003
(adapted from [6])
Evaluation FVC 2004 FVC 2006 FpVTE 2003
Algorithms Open category: 41
Light category: 26
Open category: 44
Light category: 26
Large scale test (LST): 13
Medium scale test (MST): 18
Small scale test (SST): 3
Population Students Heterogeneous (including
manual workers and elderly
people)
Operational data from a variety of
U.S. Government sources
Fingerprint format Flat impressions from
low-cost scanners
Flat impressions from
low-cost scanners
Mixed formats (flat, slap and rolled)
from various sources (paper cards,
scanners)
Perturbations Deliberately exaggerated
perturbations
Selection of the most difficult
images according to a quality
index
Intrinsic low quality fingers and/or
non-cooperative users
Data collection Acquired for this event From the BioSec database From existing U.S. Government
sources
Database size Four databases, each
containing 880 fingerprints
from 110 fingers
Four databases, each
containing 1,800 fingerprints
from 150 fingers
48,105 fingerprints from 25,309
subjects
Anonymous
participation
Allowed Allowed Not allowed
Best average EER
(over all the
databases used)
2.07 % (Open category) 2.16 % (Open category) 0.2 % (MST, the closest to the FVC
open category)
456
F
Fingerprint Databases and Evaluation

NIST Fingerprint Vendor Technology
Evaluation (FpVTE2003)
The NIST Fingerprint Vendor Technology Evaluation
(FpVTE2003) [13] aimed at: (1) comparing systems on
a variety of fing erprint data and identifying the most
accurate systems; (2) measuring the accuracy of finger-
print matching, identification, and verification on ac-
tual operational fingerprint data; and (3) determining
the effect of a variety of variables on matcher accuracy.
Eighteen different companies competed in the FpVTE,
and 34 systems were evalua ted.
Three separate subtests were performed in the
FpVTE2003: (1) the large-scale test (LST), (2) the
medium-scale test (MST), and (3) the small-scale test
(SST). SST and MST tested matching accuracy using
individual fingerprints, whereas LST used sets of fin-
gerprint images. The size and structure of each test
were designed to optimize competing analysis objec-
tives, available data, available resources, computational
characteristics of the algorithms and the desire to in-
clude all qualified participants. In particular, the sizes
of MST and LST were only determined after a great deal
of analysis of a variety of issues. Designing a well-
balanced test to accommodate heterogeneous system
architectures was a significant challenge.
Data in the FpVTE2003 came from a variety of U.-
S. Government sources, including low quality fingers of
low quality sources. 48,105 sets of flat slap or rolled
fingerprint sets from 25,309 individuals were used,
with a total of 393,370 fingerprint images. The systems
that resulted in the best accuracy performed consistently
well over a variety of image types and data sources. Also,
the accuracy of these systems was considerably better
than the rest of the systems. Further important conclu-
sions drawn from the FpVTE2003 included: (1) the
number of fingers used and the fingerprint quality had
the largest effect on system accuracy; (2) accuracy on
controlled data was significantly higher than accuracy on
operational data; (3) some systems were highly sensitive
to the sources or types of fingerprints; and (4) accuracy
dropped as subject age at time of capture increased.
NIST Minutiae Interoperability Exchange
Test (MINEX)
The purpose of the NIST Minutiae Inte roperability
Exchange Test (MINEX) [14] was to determine the
feasibility of using minutiae data (rather than image
data) as the interchange medium for fingerprint infor-
mation between different fingerprint matching sys-
tems, and to quantify the verification accuracy
changes when minutiae from dissimilar systems are
used for matching fingerprints.
▶ Interoperability of
templates is affected by the method used to encode
minutiae and the matcher used to compare the tem-
plates. There are different schemes for defining the
method of locating, extr acting, formatting and match-
ing the minutiae information from a fingerprint image
[1]. In the MINEX evaluation, proprietary template
formats were compared to the ANSI INCITS 378-
2004 template standard.
The images used for this test came from a variety of
sensors, and included both live-scanned and non live-
scanned rolled and plain impression types. No latent
fingerprint images were used. Participants submitting
a system had to provide an algorithm capable of
extracting and matching a minutiae template using
both their proprietary minutiae format and the ANSI
INCITS 378-2004 minutiae data format standard. The
most relevant results of the MINEX evaluation are:
1. In general, proprietary templates lead to better
recognition performance than the ANSI INCITS
378-2004 template.
2. Some template generators produce standard tem-
plates that are matched more accurately than others.
Some matchers compare templates more accurately
than others. The leading vendors in generation are
not always the leaders in matching and vice-versa.
3. Authentication accuracy of some matchers can be
improved by replacing the vendors template gener-
ator with that from another vendor.
4. Performance is sensitive to the quality of the data-
set. This applies to both proprietary and interoper-
able templates. Higher quality datasets provide
reasonable interoperability, whereas lower quality
datasets do not.
Related Entries
▶ Biometric Sample Acquisition
▶ Fingerprint Device
▶ Interoperability
▶ Performance
▶ Performance Evaluation
Fingerprint Databases and Evaluation
F
457
F

References
1. Maltoni, D., Maio, D., Jain, A., Prabhakar, S.: Handbook of
Fingerprint Recognition. Springer, New York (2003)
2. Jain, A., Ross, A., Pankanti, S.: Biometrics: A tool for informa-
tion security. IEEE Trans. Inf. Forensics Secur. 1, 125–143 (2002)
3. NIST Special Databases and Software from the Image Group,
http://www.itl.nist.gov/iad/894.03/databases/defs/dbases.html
4. Maio, D., Maltoni, D., Capelli, R., Wayman, J., Jain, A.:
FVC2000: Fingerprint verification competition. IEEE Trans. Pat-
tern Anal. Mach. Intell. 24, 402–412 (2002)
5. Maio, D., Maltoni, D., Capelli, R., Wayman, J., Jain, A.:
FVC2002: Second fingerprint verification competition. Proc.
Intl. Conf. Pattern Recognit. 3, 811–814 (2002)
6. Cappelli, R., Maio, D., Maltoni, D., Wayman, J.L., Jain, A.K.:
Performance evaluation of fingerprint verification systems. IEEE
Trans. Pattern Anal. Mach. Intell. 28, 3–18 (2006)
7. FVC2006. Fingerprint Verification Competition, http://bias.csr.
unibo.it/fvc2006/default.asp (2006)
8. Fierrez, J., Ortega-Garcia, J., Torre-Toledano, D., Gonzalez-
Rodriguez, J.: BioSec baseline corpus: a multimodal biometric
database. Pattern Recognit. 40, 1389–1392 (2007)
9. Garcia-Salicetti, S., Beumier, C., Chollet, G., Dorizzi, B., les
Jardins, J., Lunter, J., Ni, Y., Petrovska-Delacretaz, D.: BIOMET:
A multimodal person authentication database including face,
voice, fingerprint, hand and signature modalities. Lecture
Notes Comput. Sci. 2688, 845–853 (2003)
10. Ortega-Garcia, J., Fierrez-Aguilar, J., Simon, D., Gonzalez, J.,
Faundez-Zanuy, M., Espinosa, V., Satue, A., Hernaez, I., Igarza,
J., Vivaracho, C., Escudero, D., Moro, Q.: MCYT baseline cor-
pus: a bimodal biometric database. IEE Proc. Vision Image
Signal Process 150, 395–401 (2003)
11. Fierrez, J., Galbally, J., Ortega-Garcia, J., et al: BiosecurID:
A multimodal biometric database. Pattern Anal. Appl. 12 (2009)
12. Ortega-Garcia, J., Fierrez, J., Alonso-Fernandez, F., et al: The
multi-scenario multi-environment BioSecure multimodal
database (BMDB), IEEE Trans. Pattern Anal. Mach. Intell.
31 (2009)
13. Wilson, C., et al: Fingerprint Vendor Techonology Evaluation
2003: Summary of Results and Analysis Report. NISTIR 7123,
http://fpvte.nist.gov (2004)
14. Grother, P., et al.: MINEX – Performance and interoperability
of the INCITS 378 fingerprint template, NISTIR 7296, http://
fingerprint.nist.gov/minex (2005)
15. ANSI-INCITS 378, Fingerprint Minutiae Format for Data Inter-
change, American National Standard (2004)
Fingerprint Device
▶ Fingerprint, Palmprint, Handprint and Soleprint
Sensor
Fingerprint Encryption
▶ Fingerprints Hashing
Fingerprint Fake Detection
JEAN-FRANC¸OIS MAINGUET
Grenoble, France
Synonyms
Liveness detection; Cut finger problem; Dead finger
detection; Fake finger detection; Gummy bear finger;
Latex finger; Liveness detection
Definition
Fingerprint fake detection is used to identify a fake
finger, such as a cast made of latex. By extension, it
also includes tests to detect a cut finger or dead finger,
or a latent print remaining on a sensor after usage.
Introduction
In ‘‘Diamonds are forever’’ (1971) [1] James Bond took
the identity of Peter Frank with a thin layer of latex
glued on his fingertip to spoof Tiffany Case’s camera.
James was using a simple fake finger, but the situa-
tion can be worse. With automated fingerprint recogni-
tion systems becoming more widely used, concerns over
fingerprint fake detection have increased. In March
2005, a team of carjackers in Subang Jaya in Malaysia
chopped off part of the owner’s left index finger, when
they realized that his S-Class Mercedes Benz had a
security feature which would immobilize the car with-
out his fingerprint. Even with more reliable cut finger
detectors in use, it is likely that this will happen again.
Security of a fingerprint-based system can be
divided into two main areas:
1. The electronic security, which poses the question:
‘‘Is the electronic system, at the other end of the
wires, a real trustful authorized fingerprint system ?’’
458
F
Fingerprint Device

2. The liveness securit y, which asks a different ques-
tion: ‘‘Is the object touching the sensor a real finger,
alive and connected to a living person?’’
Answers for electronic security deal with cryptography,
using challenge-response schemes and cryptographic
codes. Since the focus of this essay is to answer the
second question, we will suppose that the electronic
system is perfect and cannot be broken.
To begin, we know 100% security does not exist.
However, what we would verify is that, ‘‘I’m Mr X, a
living person not under threat and I agree to this
action.’’ Lacking the ability to read a person’s mind,
this is an impossible task. At the opposite end, a basic
fingerprint system w ill identify a particular fingerprint
image as likely the same one as registered in the tem-
plate, which is only a small brick within a full security
system.
To fill the gap, we need to acquire more informa-
tion that will enable us to say ‘‘this is a real alive finger.’’
If we can do that, then we have a good chance to know
that a real person is making the transaction, rather a
cast or cut finger being applied to the sensor. This will
not answer the problem of detecting a person under
threat, but it should be enough under normal usage,
although some situations will never be detectable. For
example, it will be impossible to detect a graft. In
France, a man received two hands from a donor, a
great medical achievement [2]. But at the same time,
he received 10 brand new fingerprints! There is also
the case of George who attempted to enter the US
illegally on 24 September 2005 through the Nogales,
Arizona Port of Entry during which time US Customs
and Border Protection officers noted that his finger-
prints had been surgically replaced with skin from
his feet. George stated that this procedure had been
done by a doctor in Phoe nix to ‘‘clean’’ his identity [3].
But these should be extremely rare cases. What is
primarily desired is to avoid anyone stealing a finger-
print to impersonate someone else. So, while it is
impossible to create an absolute fake finger detection
system, it is possible to make things extremely hard
to be cracked.
Compromised Fingerprint
When someone creates a fake of one of the fingerprints
and use it to spoof a fingerprint system, then we say
that this fingerprint is compromised. With a smart
card (or a key), the smart card can be revoked. Further
use of the card can be prevented and a new one can be
created. But with fingerprints, this is limited to the
10 fingers. Biometric traits – the basis of biometrics
cannot be revoked.
Liveness detection solves the compromised finger-
print problem. If the system can check that it is the
real alive finger, then there is no possibility of using
a fake.
Attended/Unattended System
It is commonly admitted that an attended biometric
system does not need any liveness detection because
the superv isor ‘‘obviously’’ checks that a real alive
person is present. In the case of fingerprints, this
would be true if the supervisor was checking the finger:
is the finger really connected to the body, and without
any glued cast (Fig. 1)?
Fingerprint Fake Finger Detection Levels
There are three fake finger methods and detection
levels described, starting from the easiest to the hardest
to detect:
1. Latent print left on the sensor
2. Fake/copies:
a. Printed fingerprint imag e
b. Fake made of gelatin, latex, or other material
Fingerprint Fake Detection. Figure 1 Thin fake made of
gelatine glued on a real finger.
Fingerprint Fake Detection
F
459
F
