Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.

Forensic Evaluation of Fingerprints
and Fingermarks
▶ Fingerprint, Forensic Evidence of
Forensic Identification Based on
Dental Radiographs
▶ Dental Biometrics
Forensic Science
Forensic science refers to the applications of scientific
principles and technical methods to the investigation
of criminal activities, in order to establish the existence
of a crime, to determine the identity of its author(s)
and their modus operandi.
▶ Forensic Applications, Overview
Forensic Speaker Recognition
▶ Voice, Forensic Evidence of
Forgery Attempt
Active forgery attempt is an impostor attempt in which
an individual tries to match the stored template of a
different individual by presenting a simulated or repro-
duced biometric sample, or by intentionally modify-
ing his or her own biometric characteristics.
▶ Influential Factors to Performance
Forgery Sign
Synonyms
Forgery signature; Impostor sign; Mim icked sign
Definition
Forgery sign is an illegal sign by simulating or tracing a
genuine signature. There are two kinds of forgery signs
such as ‘‘substitution or random’’ and ‘‘freehand or
skilled.’’ The former is called as ‘‘zero effort’’ forgery,
because the forger uses his or her own signature
instead of the signature to be tested. The later includes
signatures imitated as closely as possible by simulating
or tracin g a genuine signature.
▶ Signature Matching
Forward-Backward Algorithm
TheForward–Backwardalgorithmistheconventional,
recursiv e, efficient way to evaluate a Hidden Markov
Model, that is, to compute the probability of an observa-
tion sequence given the model. This probability can be
used to classify observation sequences in recogn ition
applications.
▶ Hidden Markov Models
Fourier Transform
Mathematically, the continuous Fourier transform is
one of the specific forms of the Fourier analysis.
580
F
Forensic Evaluation of Fingerprints and Fingermarks

It transforms the original function in the time-domain
into another functio n in the frequency domain. The
term ‘‘Fourier transform’’ can refer to either the fre-
quency domain representation of a function or to
the process/formula that transforms one function
to another.
▶ Face Recognition, Component-Based
▶ Image Pattern Recognition
▶ Iris Encoding and Recognition Using Gabor Wave-
lets
▶ Iris Recognition Using Correlation Filters
Fovea
The fovea is a small depressed region at the center of
the macula, the central area of the retina. There, the
inner retinal layers are shifted aside, allowing light to
pass unimpeded to the photoreceptors. Only tightly
packed cones, and no rods, are present at the foveola,
the center of the fovea. The elongated axons of these
cone cell bodies are called Henle fibers. The fovea is the
region of maximum visual acuity.
▶ Anatomy of Eyes
Fragile Bits
▶ Iris Template Extraction Via Bit Inconsistency and
GRIT
Fraud Deterrence
▶ Fraud Reduction, Applications
▶ Fraud Reduction, Overview
Fraud Mitigation
▶ Fraud Reduction, Applications
▶ Fraud Reduction, Overview
Fraud Reduction, Applications
VICTOR MINCHIH LEE
International Biometric Group, New York, NY, USA
Synonyms
Biometric fraud reduction; Duplicate detection; Fraud
deterrence; Fraud mitigation
Definition
Fraud is conventionally defined as the deliberate per-
version or withholding of veracity in order to induce
another to surrender something of value. In the con-
text of biometrics, the item of value is typically an
identity or a privilege associated with an identity.
For the purposes of this entry, fraud reduction in
a biometric applications context refers to the use of
biometric technology’s duplicate detectio n capabilities
to deter, inhibit, and mitigate fraud. Duplicate detec-
tion refers to the discovery of multiple identities
claimed by a single, given individual.
Introduction
For numerous decades, individuals have sought to mis-
represent their identities for the sake of obtaining ben-
efits and privileges to which they are not properly
entitled. Such fraud can be costly – both financially
and politically. For fiscal year 2007/2008, the United
Kingdom’s Department for Work and Pensions esti-
mated that it overpaid about £2.7 billion in housing-
related benefits, alone, due to fraud and error [1]. From
October 2002 to September 2005, the US Justice
Department indicted 40 voters (21 noncitizens) for
illegal voting or voter registration fraud [2].
Fraud Reduction, Applications
F
581
F

In 2000, following the United States’ presidential
election, a study in Georgia, USA, discovered over
15,000 deceased individuals on the state’s active
voting rolls. The US Federal Election Commission
also discovered 502,968 names on Alaska’s 1998
voter rolls – yet only 437,000 eligible voters were
estimated by the statewide census conducted that
year [3]. In both cases, several thousand invalid, but
influential, votes could have been cast in close elec-
tions by individuals assuming others’ identities or
fake identities.
In the past, such fraudulent actions were enabled
by the tendency to ascertain identity based upon doc-
umentation with little – if any – connection to the
distinctive characteristics of the legitimate document
holder, aside from often replaceable or forgeable
photographs. Authenticity of transactions was assured
more by anti-forgery, docum ent-oriented techniques
(such as watermarks, holographs, security strips,
microlines, intaglio printi ng, etc.) rather than by
examination of the document bearer.
The advent of biometrics, however, has enabled
a shift of focus from predominantly documents to
a mix of documents and individuals. In 1858, the
United Kingdom’s William Herschel of the Civil
Service of India was precocious in his decision to
capture employee palmprints to help distinguish
amongst his native Indian staff on paydays [4].
Today, automated biometric capture and processing
systems allow for quick determinations and verifica-
tions of identity. They enable the detection of indivi-
duals who may assume multiple nominal identities
through various documents, but who are really the
same, single entity.
This duplicate detection capability deters and inhi-
bits fraud in applications including:
1. Benefits issuance and disb ursement
2. Voter registration
3. Visa shopping
4. Border control
5. Consumer recognition and
6. Time and attendance monitoring
This entry introduces and provides examples of the
first four aforementioned applications. Consumer
recognition (including check cashing) and time and
attendance monitoring are both addressed in other
entries.
Benefits Issuance and Disbursement
Governments are often responsible for the proper and
equitable distribution of benefits to their qualified
citizenry. With large populations of potential benefits
recipients, however, it can be a logistics challenge to
keep track of who is a qualifie d recipient and whether
or not they have previously claimed a given benefit
and are attempting illegitimately to reclaim the same
benefit (a phenomenon sometimes referred to as
‘‘
▶ double dipping’’).
Biometrics can help mitigate the problems asso-
ciated with such challenges. Initially, when biometrics
are first captured and associated with a given identity
in an enrollment process, biometrics are particularly
vulnerable and dependent on the legitimacy and ro-
bustness of
▶ breeder documents. But once a ▶ nomi-
nal identity has been paired with a biometric, a
government can be relatively certain that whenever
that biometric is presented, it is presented by the indi-
vidual with that same nominal identity and not an
imposter. This is because of the fundamental assump-
tion and belief that biometrics based on individual
physiological and behavioral characteristics are more
difficult to steal and forge than are documents.
One example of the benefits that can ensue is
the deployment of fingerprint recognition technology
by the United States of America’s Texas Health and
Human Servi ces Com mission (HHSC). HHSC sought
to ensure that Texas’ limited Medicaid benefits be
distributed only to the truly needy. HHSC wanted
to make sure that it was paying for services actually
rendered and delivered only to those authorized
to receive Medicaid benefits. By lever agi ng finger-
print bio metrics, HHSC sought to confirm that
authorized Medicaid recipients were indeed physical-
ly at treatment facilities when Medicaid benefits were
disbursed [5].
Another example of biometrics applied to fraud
reduction in benefits issuance is the Andhra Pradesh
Ration Card Entitlements program in India. In this
deployment, first announced on 16 June 2005, iris
recognition systems were employed in the issuance of
food ration cards by the state of Andhra Pradesh [6].
Through the incorporation of biometrics in the pro-
gram, Andhra Pradesh officials seek to deter its citi-
zenr y from selling or sharing their food ration cards, as
well as returning to claim multiple cards under differ-
ent nominal identities.
582
F
Fraud Reduction, Applications

Voter Registration
The validity of elections critically depends on ensuring
that only legitimate voters vote and that the general
democratic principle of ‘‘one voter, one vote’’ is fol-
lowed. As with benefits issuance, biometric systems
can help in determining who is voting, that they are
authorized to vote, and that they are not voting, or
registering to vote, multiple times. Biometrics can also
act as a fraud deterrent by, for example, facilitating the
forensic identification of a person who attempts to
vote using a deceased individual’s credentials.
One example of biometrics in a voter registration
application is the Bangladeshi Voter Registration Proj-
ect. This project, run by the Bangladesh Army and
Bangladesh Elections Commission, utilized fingerprint
biometric technology to register voters for Bangla-
desh’s 2008 general elections and to issue national
identity cards. Four fingerprints were captured from
each registrant and checked to see if they matched
those captured from a prior registrant [7].
The Bangladeshi Voter Registration Project fol-
lows similar voter registration deployments conducted
in countries like Mexico, Mozambique, and Nigeria.
In Mexico, the Instituto Federal Electoral implemented
a multi-biometric system that uses fingerprint and
facial recognition to analyze historical voter rolls for
duplicates, as well as to vet new voters against existing
voter rolls [8].
Visa Shopping
In 2007, the European Parliament recognized a chal-
lenging problem facing several European Union mem-
ber states: visa applicants rejected by a Schengen
country were applying to other Schengen countries
in the hopes of finding one that would issue them
a visa. They were ‘‘visa shopping.’’ In some cases,
applicants would present forged documents as part
of the visa application process.
To counter such attempts, the European Parlia-
ment established the Visa Information System (VIS).
VIS is a database that contains fingerprint and face
images and associates the collected biometrics with
visa applicants’ biographical data, as well as the dates
and locations of application attempts [9]. Authorized
officials responsible for border security can now better
detect if a visa applicant has previously been rejected
by another Schengen nation and is presenting falsified
documents.
One result of the implementation of VIS has been
that some visa applicants who have been rejected pre-
viously, or who have reason to believe they may be
rejected, have mutilated their own fingers to avoid
being processed against VIS. Others have attempted
to perpetuate fraud by trying to alter their fingerprints
using often painful processes with low chances of suc-
cess, given that fingerprints extend beyond the
epidermis.
Border Control
As with visa shopping deployments, border control
deployments seek to protect national borders by deter-
mining with greater certainty who is entering (and,
sometimes, exiting) a nation. These biometric applica-
tions help deter and expose entrance document fraud
and identity fraud. They differ from visa shopping
deployments insofar as they are oriented more towards
identity and credential verification at the arrival and
departure stages, rather than at the registration or
application stages.
One example of a border control fraud reduction
effort using biometrics is the United Arab Emirates’
Iris Expellee Tracking System, deployed in 2003 and
run by the Abu Dhabi Police. United Arab Emirates
(UAE) officials were concerned about foreigners ex-
pelled from the UAE subsequently attempting to reen-
ter the country after changing their name and/or
nationalit y and then obtaining a new passport. The
Iris Expe llee Tracking System involves collecting iris
images from all expelled foreigners. Arriving Passen-
gers have their irises scanned at the UAE borders to
verify that they were not formerly expelled. In 2005,
the UAE reported catching approximately 32,850 pre-
viously expelled individuals [10].
Another program, the Canadian Passenger Acceler-
ated Service System (CANPASS), uses iris recognition
to allow preapproved, low risk travelers to clear
Canadian customs and immigration without having
to present documentation to border officials. Appli-
cants who are approved to participate in CANPASS
have their irises enrolled into the system. They then
present their irises at designated kiosks at participating
border environments (e.g., airports) for quick passage
into Canada. This system not only helps reduce the
Fraud Reduction, Applications
F
583
F
chance of forged documents passing inspection due to
human error, it also allows border control officers to
focus more on persons of greater interest who are more
likely to be potential fraudsters.
Related Entries
▶ Asset Protection
▶ Binding of Biometric and User Data
▶ Biometric Encryption
▶ Consumer Recognition
▶ Forgery Sign
▶ Fraud Reduction, Applications
▶ Liveness and Anti-Spoofing
▶ Spoofing
▶ Time and Attendance
References
1. UK Department for Work and Pensions, Information Director-
ate: Fraud and Error in the Benefit System: October 2006 to
September 2007 (May 2008)
2. Urbina, I.: Voter ID Battle Shifts to Proof of Citizenship,
New York Times. http://www.nytimes.com/2008/05/12/us/poli-
tics/12vote.html?ref = opinion (12 May 2008). Accessed 2 Sept
2008
3. Samples, J.: The Motor Voter Act and Voter Fraud, CATO Insti-
tute. http://www.cato.org/testimony/ct-js031401.html (14 May
2001). Accessed 2 Sept 2008
4. Palm Print Recognition, National Science and Technology
Council. http://www.biometrics.gov/Documents/PalmPrintRec.
pdf. Accessed 2 Sept 2008
5. Front End Medicaid Fraud Reduction Pilot Program Based
on Biometric Front-End System, Texas Health and Human
Services Commission. http://www.hhsc.state.tx.us/OIE/RFP/
FrontEnd/FingerImaging_RFI.pdf (30 June 2003). Accessed
2 Sept 2008
6. LGE Iris Tech Win in India Redefines Biometr ic Scalability.
Findbiometrics.com. http://www.findbiometrics.com/article/115.
Accessed 2 Sept 2008
7. BIO-key and Tiger IT Bangladesh Voter Registration
Project Nearing Completion, BIO-key International, Inc.
http://www.reuters.com/article/pressRelease/idUS121192 + 17-
Jun-2008 + PRN20080617 (17 June 2008). Accessed 3 Sept 2008
8. The Mexican Instituto Federal Electoral (IFE): Mexico deploys
multi-biometric voting system. Biometric Technol. Today. 14(5),
3–4 (2006)
9. Kablenet: EU aims to stop ‘visa shopping’, The Register. http://
www.theregister.co.uk/2007/06/08/schengen_visa_data/ (8 June
2007). Accessed 3 Sept 2008
10. Lieutenant Mohammad Al-Mualla: The UAE Iris Expellees Track-
ing and Border Control System. http://www.biometrics.org/
bc2005/Presentations/Conference/2%20Tuesday%20September
%2020/Tue_Ballroom%20B/Lt.%20Mohammad%20UAE2005.
pdf. Accessed 4 Sept 2008
11. Study Report on Biometrics and E-Authentication. INCITS/M1
Ad Hoc Group on Biometrics in E-Authentication (2006)
12. Anderson, K.: Consumer Fraud in the United States: Second
Survey. Federal Trade Commission, Washington, DC (2007)
13. Lee, V.: Transcript of Authentication Technologies FTC Proof
Positive Workshop Session. Federal Trade Commission,
Washington, DC (2007)
14. Progress in Tackling Benefit Fraud: Thirty-first Report of Session
2007–2008, UK House of Commons, Committee of Public
Accounts. Accessed 2 June 2008
Fraud Reduction, Overview
VICTOR MINCHIH LEE
International Biometric Group, New York,
NY, USA
Synonyms
Biometric fraud reduction; Fraud deterrence; Fraud
mitigation; Identity theft reduction
Definition
Fraud is conventionally defined as the deliberate per-
version or withholding of veracity to induce another to
surrender something of value. In the context of
biometrics, the item of value is typically an identity
or a privilege associated w ith an identity.
Fraud can assume a variety of forms ranging from
phishing to scams to hacking. In the specific case of
biometrics, fraud can also consist of spoofing, or the
presentation of an artifact designed to imitate a legiti-
mate biometric.
Fraud reduction in a biometric context entai ls both
the use of biometric technology to deter, inhibit, and
mitigate fraud, as well as efforts to counter the exploi-
tation of biometric system vulnerabilities through ille-
gitimate submissio ns.
584
F
Fraud Reduction, Overview

Introduction
With the increased reliance of modern society on
technolog y, fraudsters have developed new exploitative
techniques to prey upon the unsuspecting and the
vulnerable. Internet merchants offer wares at hard-
to-resist discounts, but never deliver their patrons
any of the purchased goods. Sophisticated counterfei-
ters create fake currency and checks that are frequently
difficult to distinguish from their genuine counter-
parts. Identity thieves send realistic, yet illegitimate,
emails designed to harvest passwords and identit y in-
formation from the careless and the inexperienced.
The cost of fraudulent activity, which includes
tangible sums lost and expenditures to recover stolen
goods, identities, or privileges, can be enormous. In
2005, British insurer Norwich Union estimated the
cost of fraud in UK to be around £16 billion, or roughly
1.4% of UK’s gross economic output (http://news.bbc.
co.uk/1/hi/business/4463132.stm). In 2006, this num-
ber soared to £40 billion according to conservative UK
government estimates (http://www.timesonline.co.uk/
tol/news/uk/article633540.ece). The same year, identity
theft alone victimized over 8 million people in the
US to the tune of more than US $49 billion, according
to the California Office of Privacy Protection. Unfor-
tunately, loss due to fraudulent activities is likely
to increase as fraudsters expand their reach thanks to
increased globalization and rapid development of
technolog y.
Technology, however, can be used both to abet, as well
as combat, fraud. Biometric technologies and systems,
especially, enable the deterrence, inhibition, and mitiga-
tion of fraud. For the purpose of this discussion,
biometrics are defined as technologies that perform auto-
mated measurement of human physiological or behav-
ioral characteristics to determine or authenticate identity.
Biometrics, thus, revolve around the concept of
identity. Identity, in turn, is often seen as a proxy for
trustworthiness, whether through linkage of identity to
a historical and/or transactional record, or through
connection of identity to a privilege or right.
Trustworthiness is the first victim of a ny fraudulent
act. Security, robustness, and confidence of identity are
therefore critical. Biometrics, if employed judiciously
and with appreciation for the limitations and vulner-
abilities of the tech nology, can satisfy such crucial
needs.
Biometrics Vis-a
`
-Vis Alternative
Authentication/Identification
Technologies
Biometric Advantages in Fraud Reduction
Currently several non-biometric methods and technol-
ogies exist to help combat fraud by serving an
▶ au-
thentication or
▶ identification function. Examples of
such technologies include smart cards, tokens, fobs,
passwords, and personal identification num bers
(PINs). Generally, these technologies can be divided
into two categories: those based on something one has
and those based on something one knows.
Biometrics introduces a third, complementary as-
pect: authentication and identification technologies
based on something one is. By focusing on the ele-
ments that are inherent to an individual, biometrics
offer additional protections that are unavailable or
weaker through more traditional authentication/iden-
tification technologies. These include:
Convenience
Accountability
Security
Convenience
Biometrics can obviate the carry ing of tokens or cards
that can be lost, misplaced, or – more saliently – stolen,
leading to fraudulent access or unauthorized trans-
actions. Biometrics can also eliminate the need to
remember passwords or PINs. Often, people select
simplistic passwords that can be easily guessed or
hacked because they fear that they will forget more
complex passwords.
Losing or forgetting a biometric, however, is con-
siderably more difficult, especially for biometrics pri-
marily dependent on physiological, rather than
behavioral characteristics. Whereas one can suffer
brain damage and forget how to sign one’s name,
rendering signature recognition useless, misplacing or
forgetting a finger that is integrally tied to the rest of
one’s body is harder to accomplish. While violent
criminals can go to extremes to remove a finger from
a target so as to gain access to a fingerprint-secured
facility, it is markedly more challenging to trick a target
into unwittingly giving up suc h a personal feature.
Fraud Reduction, Overview
F
585
F

Accountability
Biometrics are excellent technologies when trans-
ferability is of concern. Instead of relying on force or
compulsion, fraudsters achieve success thr ough convinc-
ing, coercion, and deception designed to encourage vic-
tims to surrender, or provide access to, a privilege, right,
or item of value. Sophisticated scams, for example,
can lead victims consciously and willingly to hand over
precious access cards or passwords to perpetrators of
fraud.
Biometric characteristics, however, are distinct and
very personal. Their transference from one individual
to another can be, as mentioned earlier, extremely
challenging. This can contribute markedly to account-
ability, in addition to deterring and inhibiting fraud. If
it is difficult for a fraudster to trick an individual into
giving up their biometric, then any action taken that
can be linked to that biometric is likely to have been
undertaken by the legitimate possessor of the biomet-
ric in question. This makes it difficult to believe
excuses in which a misdeed was allegedly committed
by another who fraudulently obtained one’s biometric
characteristics.
With more traditional authentication/identifica-
tion technologies, however, transferability can translate
into reduced accountability. One fraudster could
borrow access cards or passwords that allow him to
take advantage of services or privileges intended for
another. There could even be complicity in this effort –
something that would take a high degree of per sonal
sacrifice if biometrics were involved.
Biometrics can also add an element of accountabil-
ity by deterring and inhibiting fraudulent attempts at
establishing or relying on multiple identities. In the
past, for instance, certain fraudsters with notorious
histories of cashing bad checks would assume several
identities so as to avoid the stigma and troubles accom-
panying their negative transactional histories. The in-
troduction of biometric technologies and systems,
however, has helped identify and address problems of
multiple registrations by linking pers onal, biometric
characteristics, rather than just nominal identities, to
transactional histories and other historical records.
This has also aided in the combating of fraudulent
acts including multiple civil ID registrations and visa
shopping.
Additionally, in some case, biometr ics deter and
mitigate acts of fraud by encouraging or necessitating
the leaving behind of distinct, personal characteristics.
For example, some prospective culprits may think
twice before acting if they are aware that their criminal
and fraudulent activity could potentially result in the
leaving behind of biometric markers, such as their
latent fingerprints. Those who proceed anyway and
ignore the concern of enrolling in a biometric system
and leaving behind an image or template of a distinct,
personal characteristic could possibly be identified
later and tracked by the biometrics they previously
presented, a potential advantage for law enforcement
and means of mitigating the severity and impact of a
fraudulent act (e.g., by catching fraudsters before they
are able to take advantage of the captured item of value
or privilege).
Security
As described above, biometrics offers security and anti-
fraud advantages over more traditional authentication/
identification technologies with respect to identity
transference, establishment of multiple fake identities,
and loss or forgetting of credentials. They can render
certain fraudulent activities – like phishing – almost
irrelevant.
Biometric characteristics also provide additional
anti-fraud security benefits thanks to their inherent
nature; compared with passwords/PINs and cards/
fobs/tokens, biometric characteristic is generally more
difficult to capture, steal, replicate, and fake. Cards, for
instance, are often designed to be robust, yet flexible
enough that, in case they are lost, a replacement can
be relatively easily created. PINs can be sniffed out
through tracking or hidden monitoring technologies.
They can also be readily discovered, in several cases,
through brute force and trial-and-error techniques.
Replication of a compromised PIN is then no more
complicated than re-entering the newly revealed PIN.
It can be challenging, however, to create a replica of
a biometric characteristic that has sufficient enoug h
fidelity to work with a targeted biometric system. Cre-
ating a plausible fake iris, for example , often requires
more effort than just copying electronic data onto a
new smart card or retyping a password (in which cases
the artifact will be identical to the genuine sample).
This is due in part to liveness detection, a security
function that is built into several biometric systems.
Liveness detection, a fraud countermeasure, deters or
586
F
Fraud Reduction, Overview

inhibits the presentation of artifacts, called spoofs, as
legitimate biometric characteristics. Examples of live-
ness detection include: measurement of finger perspi-
ration over time, 2D Fourier spectrum analyses, and
behavioral reactions to cues (e.g., blinking upon
command).
In addition, several biometric systems rely on tem-
plates, rather than full images of biometric charact-
eristics, for reasons that range from privacy to cost
to efficiency of data management and processing.
Attempting to regenerate or reverse-engineer a com-
plete biometric image from a select template is a very
challenging, if not, at times, outright impossible, task.
Also, trying alternative, brute-force techniques to rec-
reate a biometric character istic could take extremely
lengthy and impractical periods of time, given the vast
number and variability of components that make up
many biometric characteristics.
Furthermore, biometric systems can often be cost-
ly, expensive, and technologically complex. Spending
large sum of money to obtain a biometric device for
study and identification of vulnerabilities and penetra-
tion points may not be cost effective. Likewise, even
those who have the resources and know-how to create
fake biometric characteristics, however, may find the
effort of doing so to be cost-inefficient, especially when
the value of the item or priv ilege being protected is
outweighed by the cost of fraudulently obtaining it.
In some of the Panasonic’s US offices, for example,
hand geometry biometric readers are employed for time
and attendance functions vis-a
`
-vis custodial staff.
Though several special effects and novelty item firms
have the ability to create fake hand models, the cost and
effort entailed in obtaining a suitable spoof would proba-
bly exc eed the financial return of an extra hour of pay.
Authentication/Identification Trifecta
While biometrics offer significant advantages over
more traditional and conventional authentication/
identification technologies, it is important to note
that this does not mean that biometrics should be
employed in lieu of these other technologies. When
issues of fraud, as well as security and protection of
identity, are at stake, it may be optimal to leverage all
proven options, especially given the potentially high
cost of fraud and the ease with which fraud can ofte n
be committed.
Also, as will be discussed in the following section,
biometrics have their own inherent vulnerabilities.
These potential weaknesses can sometimes be mitigated
by adopting complementary technologies which can
provide an extra – if not necessarily equally effective –
layer of defense. Where fraud is involved, the need for
security may outweigh convenience and cost; such sce-
narios encourage reliance on an authentication trifecta
that consists of:
Something you have
Something you know
Something you are
Biometric Vulnerabilities
While biometric technologies can prove to be relatively
robust and effective tools in fraud reduction through
deterrence, inhibition, and mitigation, biometric sys-
tems themselves are not immune to fraud ulent and
exploitative attacks. Thes e attacks can be classified
according to three overarching categories:
Input level attacks
Processing and transmission level attacks
Backend and storage level attack s
Input Level Attacks
Input Level Attacks generally fall into one of three
categories:
Spoofing attacks
Bypassing attacks
Overloading attacks
Spoofing attacks consist of attempts to deceive biomet-
ric system sensors into accepting an artifact as a legiti-
mate biometric sample, typically for false enrollment,
verification, or identification purposes. Spoofing
attacks are usually considered to be attempts at break-
ing into biometric systems that are predominantly
physiological in their focus. Biometric systems that
are predominantly behaviorally bas ed revolve less
around the creation of spoof items and more around
careful observation and practiced imitation of legiti-
mate behavior.
Bypassing attacks consist of attempts to circum-
vent biometric system processes by creating artificial
Fraud Reduction, Overview
F
587
F
failures during enrollment or recognition so as to skip
the biometric system altogether. One example of a
bypassing attack would be to alter the quality of a
biometric characteristic in such a way that a biometric
system has difficulty in acquiring that characteristic.
This could, for example, entail artificially filing down
fingerprints so that there is a failure to enroll. The risk,
as a result, is that an individual could then possibly be
excused from biometric system recognition require-
ments and permitted to use a less robust authentica-
tion/identification system.
Closely related to bypassing attacks are variants
called overloading attacks. In an overloading attack, a
fraudster attempts to defeat or circumvent a biometric
system by damaging or overwhelming the biometric
sensor(s). Overloading attacks can range from flashing
strobe lights against an optical sensor to presenting
artificial heat sources to near-infrared-based sensors
to short circuiting of sensitive sensors using liquids.
As with bypassing attacks, the goal of an overloading
attack is to either reduce the robustness, precision, and
accuracy of the targeted biometric system and/or to
encourage the substitution of the biometric recogni-
tion method with a less robust authentication/identifi-
cation process and mechanism.
Processing and Transmission Level
Attacks
Processing and tr ansmission level attacks generally fall
into one of three categories:
Hacking
Skimming/Sniffing
Hill-Climbing
Processing and transmission level attacks are, strictly
speaking, lesser acts of deception and fraud and more
direct, technically based invasions. However, the result
of success in any such attack on a biometric system
could enable future acts of fraud, so it is important to
be aware of these potential vulnerabilities.
Hacking, as herein defined, consists of electronical-
ly based attempts to penetrate a biometric system by
altering the operation and functionality of the system
through non-physical modifications and subterfuge
(often at the code or system communications levels).
A hacker could change the enrollment or recognition
algorithms of a biometric system, lowering thresholds
to accommodate less robust performance and security
checks. They could program the system to forward them
the copies of legitimate samples or instruct the system to
allow them special, otherwise unauthorized, access.
Skimming and sniffing refers to techniques by
which data is captured – often surreptitiously – during
communication or processing of the information.
Skimming devices, for example, could be designed to
read and copy biometric data being submitted on a
smart card to a biometric system for comparison
against a live sample. This data could then be illegally
replicated. Sniffing could occur if moni toring pro-
grams are put in place to capture data packets being
sent from the capture sensor to the backend for
verification.
Hill-climbing attacks first consist of the presenta-
tion of a test biometric sample to a biometric algo-
rithm for comparison against an enrolled sample. A
match score is then obtained and studied so that a
new test sample can be presented for re-comparison
and the achievement of a higher match score. This
process is re-iterated until the biometric system’s
threshold has been discovered and is penetrable.
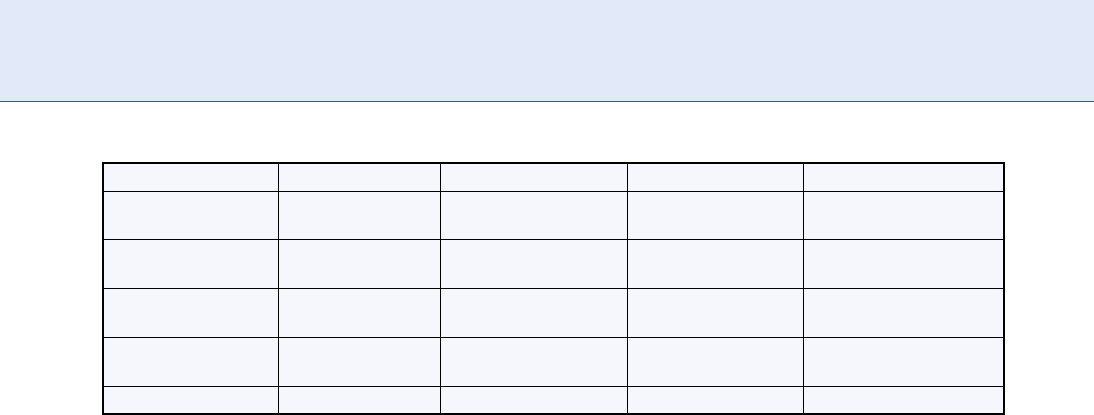
Examples of spoof types for five established biometric modalities include:
Fingerprint Face Iris Hand geometry Voice recognition
Prostheses Prostheses Prostheses Prostheses Audio playback
recordings
Props/Models/Gag
items
Masks/Disguises Video playback
recordings
Props/Models/Gag
items
Audio composite
recordings
Photograph
imitations
Photograph
imitations
Photograph imitations
Residual prints Imprinted contact
lenses
Latent prints
588
F
Fraud Reduction, Overview

Backend and Storage Level Attacks
Backend and storage level attacks generally fall into
two categories:
Infiltration
Implantation
As with the process and transmission level, the back-
end and storage levels are susceptible to malicious
hacking. Skilled hacker-fraudst ers could alter the per-
mission levels tied to specific images or templates
stored in databases. They could infiltrate the backend
and alter the way biometric data that is classified and
stored. More of concern, they could perhaps steal bio-
metric characteristics data and try to generate spoofs
using the information captured.
In addition, acts of fraud can be facilitated if
fraudsters are able to gain unautho rized or complicit
access to backend and storage databases of biometric
information to perform acts of implantation. In this
attack, fraudsters mig ht implant their own biometric
characteristics into a targeted biometric system’s
database. By doing so, fraudsters would be able to
appear as legitimately authorized indiv iduals with
free access to the rig hts or priv ileges o ther wise se-
cured by the biometric system.
Countermeasures
In order to counter – or at least inhibit – the three
aforementioned types of attacks, certain countermea-
sures can be enacted. These countermeasures can be
classified according to the level of attack they are best
suited to address.
At the input level, spoofing is typically counter-
acted by the attempt to determine whether a live, real
human sample is being presented to the capture device.
This is, as mentioned earlier, called liveness detection
and is based on the assumption that, with the excep-
tion of some cadaver recognition applicati ons, a legiti-
mate biometric will always be presented by the live
possessor of that biometric characteristic.
As for bypassing and overloading attacks, counter-
measures include increased ruggedization of capture
devices and sensor equipment, conscientious form factor
design (e.g., creating shielding from external light
sources that could be potentially malevolent), supervi-
sion of enrollment and recognition submission
processes, as well as rigorous fallback procedures and
processes. After all, those who seek to accomplish fraud
will often target the weakest link. If this means taxing a
biometric system out so that, for example, access to a
secure facility can be obtained through a potentially
more fallible human guard inexperienced at identifying
fake identity documents, which will often be the strategy
of choice for motivated fraudsters.
At the processing and transmission levels, counter-
measures may entail proven information systems and
information technology security techniques, such as
the use of firewalls and encryption. After all, at a
certain level, biometric data is often converted into
streams of digital data that should be accorded no
less than the rudimentary security protections already
commonplace for digital information that is less per-
sonally sensitive. In addition, best practices should be
implemented, such as requiring the use of data trans-
mission shields (that limit the range at which data can
be sniffed from contactless smart chips), as well as
strict limitation of access to matching score data.
At the backend and storage levels, highly advisable
countermeasures include firewalls, as well as extensive
auditing functions and logs of modifications executed
(whether they are additions, subtractions, or altera-
tions of biometric data). A best practice countermea-
sure would also be the frequent, though not necessarily
habitual or scheduled, review of random images and
templates for evidence of tamp ering, alteration, miss-
ing presence, or unexpected presence.
In order to further deter or inhibit the abuse of bio-
metric systems by fraudsters, biometric systems may also
be designed with the following four countermeasur es:
▶
Multifactor or ▶ multimodal authentication
requirements
Randomization of modality
System challenges
Emphasis on internal/subcutaneous characteristics
By adopting multifactor or multimodal systems,
deployers increase the challenge for fraudsters by requir-
ing them to defeat several disparate systems for which
the optimum exploitation and penetration techniques
may be very different. Though there is a convenience
tradeoff, the security that accrues can be significant,
particularly when security of identity is at stake. The
main caveat, however, is that potential fraudsters are not
encouraged to pretend to be unable to use one of the
modalities so as to simplify their, say, spoofing task.
Fraud Reduction, Overview
F
589
F
