Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.

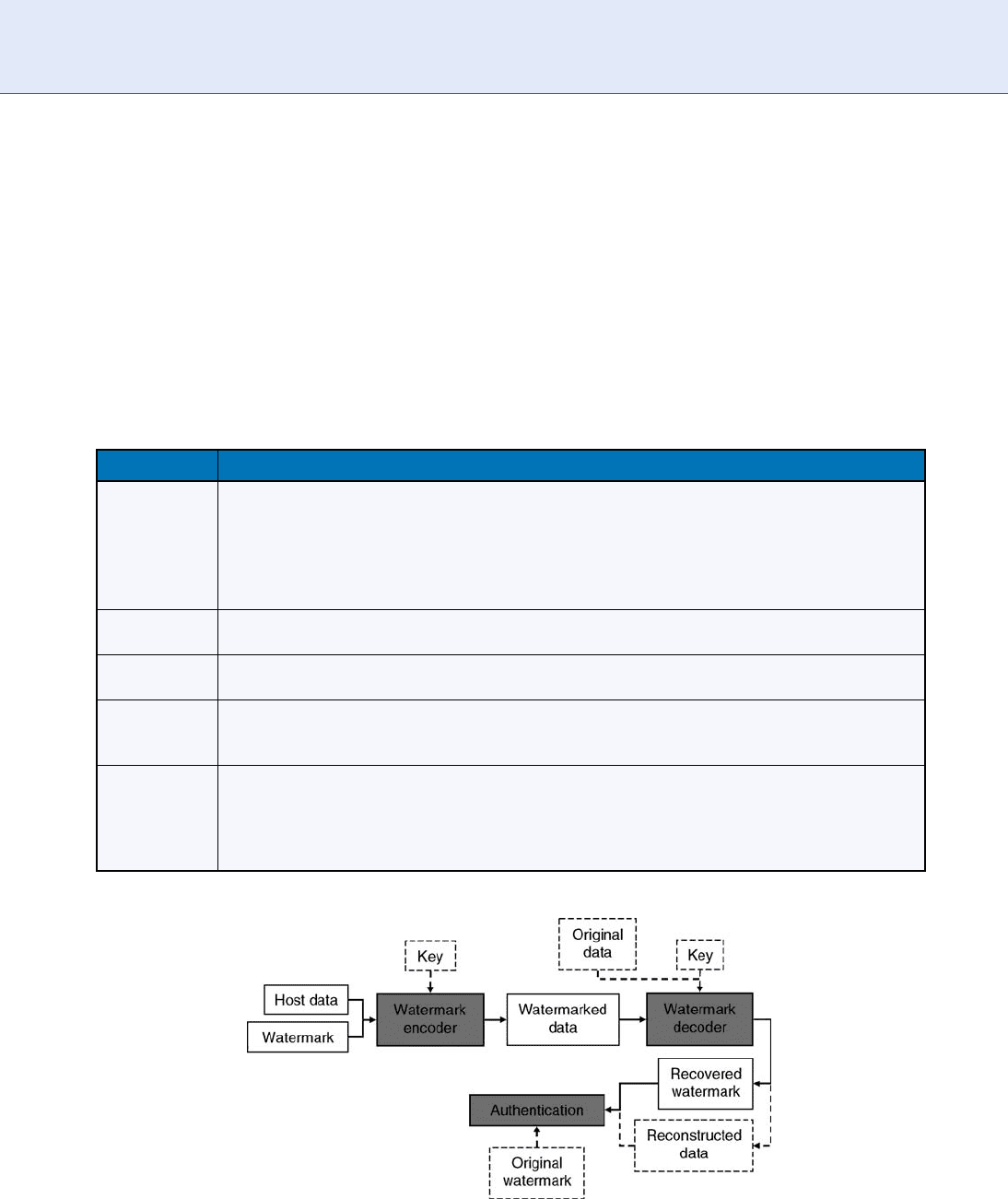
encoding, decoding, and authentication (see Figure 2 ).
The first operating module, the watermark encoder,
embeds the watermark into the host data. The water-
mark can range from a random binary bit sequence to
biometric eigen-face coefficients utilized for face recog-
nition. Additionally, the encoding module may embed a
secret key that enables the system to determine the
embedding location of the watermark in the host data.
The second operating module, the watermark decoder,
takes the watermarked host data as input and processes
them to extract the watermark. If a secret embedding
key was used during the encoding module, then the
same key is required for the decoding process. Depend-
ing on the algorithm employed, the original host data
may also be used explicitly to extract the watermark.
The final module, authentication, compares the recov-
ered watermark with the original watermark to estimate
the similarity between the two sets. If the watermark is
biometric in nature, then this biometric data can be
optionally used by the authentication system.
Watermark encoding and decoding techniques fall
into two categories: spatial and transform domain
Iris Digital Watermarking. Table 2 Characteristics of biometric watermarking systems
Characteristic Description
Imperceptibility The degree to which the host image is visibly altered or distorted due to the presence of the
watermark. Watermarked images that bear no visible difference from their original host image are
said to contain imperceptible watermarks. Rarely, this characteristic may be evaluated beyond the
scope of human perception. In these cases, a question is raised as to whether or not it is possible to
reveal that an image contains a watermark through the aid of a machine or program (without access
to the original host image)
Robustness The ability of the watermark to be detected and extracted after the watermarked image has been
subjected to any variety of transformations (i.e., compression, filters, affine transformations, etc.)
Fragility The ability to detect any file transformation by way of the watermark. The detection might result from
an inability to extract the watermark or from an extracted watermark that in not intact
Capacity The amount of information that can be embedded in the host data of a watermarking system. This is a
function of the type and size of the host data that are being watermarked and the robustness of the
watermarking system in terms of detectability and extractability
Performability The degree to which the watermark affects the performance of the biometric system(s) in question. At
a minimum, biometric watermarks should not have an adverse affect on the performance of the
biometric system(s) that they protect. Here, performance can entail matching error rates, image
quality, efficiency of computation time, etc. Some biometric watermarking schemes may positively
affect the performance of the biometric system
Iris Digital Watermarking. Figure 2 Generalized block diagram of an iris digital watermarking process. Shaded blocks
indicate the main watermarking modules, while dashed blocks/lines indicate optional areas of processing that are
algorithm specific.
780
I
Iris Digital Watermarking

techniques. Each category has specific advantages
and disadvantages, but in general, spatial domain tech-
niques have lower complexity and offer higher robust-
ness to biometric replacement attacks in which the
host biometric region is replaced by an imposter’s
biometric data. On the other hand, transform domain
techniques are of higher complexity, but are more
robust to geometrical attacks such as rotation, scaling,
and translation.
A number of studies have investigated different
approaches to biometric watermarking. Ratha et al.
[5] propose an algorithm for biometric watermarking
to counter replay attacks in on-line fingerprint authen-
tication systems. The authors modify the least signifi-
cant bit (LSB) of the indices obtained as a result of
applying wavelet scale quantization (WSQ) compres-
sion. The indices are chosen based on an embedding
key that is used as a seed for a random number gener-
ator. Similarly, Noore et al. [6], utilize the Discrete
Wavelet Transform (DWT) to watermark fingerprint
images with face and demographic text data. In [7],
Low et al. watermark a nonbiometric host image with
off-line handwritten signature in the form of a discre-
tized bit string. They experiment w ith three water-
marking techniques: LSB, Code Division Multiple
Access (CDMA) spread spectrum in the spatial domain,
and CMDA spread spectrum in a transform domain
such as the DWT. Their experiments show that CMDA
in the wavelet domain provides the most robust results
with respect to jpeg compression and image quality. In
[8], a Quantization Index Modulation (QIM) water-
marking technique is utilized to encode dynamic and
static handwriting signature features into the host sig-
nature from which the features are extracted. Embed-
ding locations are chosen based on the analysis of the
signature in two transform domains: Ridglet and
Radon-DCT (Discrete Cosine Transform). The authors
conclude that although the static and dynamic fea-
tures by themselves provide modest levels of security,
fusion of both feature types improves security and
performance.
Watermark Encoding and Decoding
The encoding portion of an iris digital watermarking
scheme involves embedding the watermark in the orig-
inal host data. The decoding portion, on the other
hand,involves extracting the watermark from the host
image. Bartlow et al. [9] present a watermarking tech-
nique modified from [10], based on amplitude modu-
lation in the spatial domain to protect iris biometric
systems. In the work, iris images are watermar ked with
simulated voice feature vectors. Equations 1, 2,and3
correspond to the amplitude modulation scheme pre-
sented by Kutter in [10]. Equation 4 represents the
adaptation required to watermark iris biometric data
as presented in [9].
Encoding- Amplitude modulation encodes the bits
of the watermark bymodifying pixel intensities in
images. Pixel intensities are modified bychanging
values B
ij
, in the blue channel of the RGB spectrum.
These modification s occurmultiple times over the
extent of the image and are either additive orsub-
tractive, depending on the value of the bit, s,and its
proportionality to the luminance, L
ij
, as seen in
Equation 1.
B
ij
B
ij
þð2s 1ÞL
ij
q
B
ij
2embedding
locations
s 2bit
L
ij
2Luminance
q 2Encoding strength
8
>
>
>
>
<
>
>
>
>
:
ð1Þ
Decoding- The decoding process estimates the
pixel value in the ‘‘encoded’’image by considering
a linear combination of the pixels in a cross-shaped
neighborhood around the encoded bit as seen in
Equation 2.
B
ij
¼
1
4c
ð
X
c
k¼c
B
iþk;j
þ
X
c
k¼c
B
i;jþk
2B
ij
Þ c 2 neighbor size
f
ð2Þ
After decoding and arriving at an estimated pixel B
ij
value, the difference between the estimated and water-
marked pixelsis averaged over all embedding locations
for that bit. Finally, thesign of this value indi cates the
bit (if positive = 1, if negative = 0). However, to
attenuate robustness to compression, cropping, and
affine transformations, an adaptive thresholding meth-
od is introduced: two bits, 0 and 1, are appended to
every bit stream as seen in Equation 3.
bit ¼ 1;d
b
>
d
0
þd
1
2
0;otherwise:
d
0
average diff of all 0 reference bits
d
1
average diff of all 1 reference bits
d
b
average diff of current bit
8
<
:
ð3Þ
Iris Digital Watermarking
I
781
I

Adaptation to Iris Biometric Data- Iris images for
use in biometric systems are usually captured in the
grayscale format. The encoding process has to be
modified to take this into consideration. For exam-
ple, [11] modifies the encoding equation to take in
local image information such as gradient, P
GM
, and
standard deviation, P
SD
, of the cross-shaped neigh-
borhood to adjust the watermarking strength.
Parameters A and B aid in adjusting the strength
of the standard deviation and gradient while mod-
ulating the bits to be encoded (for all experiments
A ¼ 100, B ¼ 1,000). The following equation
represents this adaptation.
P
WM
ði; jÞ¼Pði; jÞþð2s 1ÞP
AV
ði; jÞq
1 þ
P
SD
ði; jÞ
A
1 þ
P
GM
ði; jÞ
B
ð4Þ
P
AV
represents the average pixels in a 5 5 cross-
shaped neighborhood centered around i, j. Finally,
the reconstructed image can be calculated by replacing
the watermarked bit with the pixel value obtained from
Equation 2.
A crucial issue while encoding the watermark in the
host image relates to the degree to which it affects
the matching performance of the host biometric. The
algorithm in [9] further extends [11] by including a
parameter that indicate s the proportion of the water-
mark encoded in the iris region of the image. Figure 3
visualizes the variation of this parameter by examining
two extreme cases: the top row shows the most percep-
tible case and the bottom row shows the least percepti-
ble case tested in the work. This location-specific
encoding option may be beneficial not only to iris
digital watermarking but also to biometric watermark-
ing in general.
Application Scenarios and Attacks
Depending on the intended use, iris digital water-
marking systems are vulnerable to a series of applica-
tion scenarios and attacks. Application scenarios can
be thought of as normal usage patterns that a water-
marking system should realistically be expected to
withstand without serious side effects on the perfor-
mance of any of the characteristics outlined in Table 2.
Examples of application scenarios can include, but
are not limited to database (re)compression, partial
progressive decoding, and noisy channel transmission.
Each of these scenarios can have an effect on one or
more characteristics of a biometric watermarking sys-
tem. For instance, a highly compressed watermarked
image may lead to difficulties in the watermark extrac-
tion process, as a compression algorithm often signifi-
cantly alters an image, which in turn alters the
watermark itself. Occasionally, operat ional environ-
ments supporting slow data transmission speeds may
force a system to progressively decode portions of an
image as it becomes available. This type of application
scenario can have an effect on the robustness of the
extraction process, the performance of the biometric
system(s) in question, and potentially the impercept-
ibility of the watermark. In [9], the authors study the
robustness of the decoder after the application of these
three scenarios. Figure 4 shows the performance of the
decoder as measured by the mean percentage bit error
considering 27 different paramet er combinations of
the watermarking system (parameters are specifically
outlined in Table 3).
The graphs demonstrate the ability of the tech-
nique to tolerate the application scenarios, and in
many cases, with little or no effect on the extraction
process. Although this is just one example, many tech-
niques such as those described in [3] are capable of
tolerating scenarios similar to these. However, the
expected application environment should be consid-
ered while selecting a specific watermarking technique,
since a given technique may be well-suited for one
application scenario but ill-suited for another [3].
Perhaps the most notable difference between the
general field of digital watermarking and biometric
watermarking is its relationship to the measure of per-
formability. For obvious reasons, a biometric water-
marking system must minimize the effect it has on the
biometric system it protects. Issues such as matching
performance, image quality, computational efficiency,
and even legal repercussions must not be ignored. A
biometric watermarking system should not negatively
impact on the main modules of the biometric system(s)
in question, viz., the feature extraction and matching
modules. It should be noted that this effect could po-
tentially propagate itself in two ways. Perhaps, the most
obvious effect is when the host data are used in a
biometric system; here, the presence of the watermark
may impede the feature extraction process by adding
noise to the image. Naturally this can lead to inaccura-
cies in the matching module. A less obvious effect is
782
I
Iris Digital Watermarking
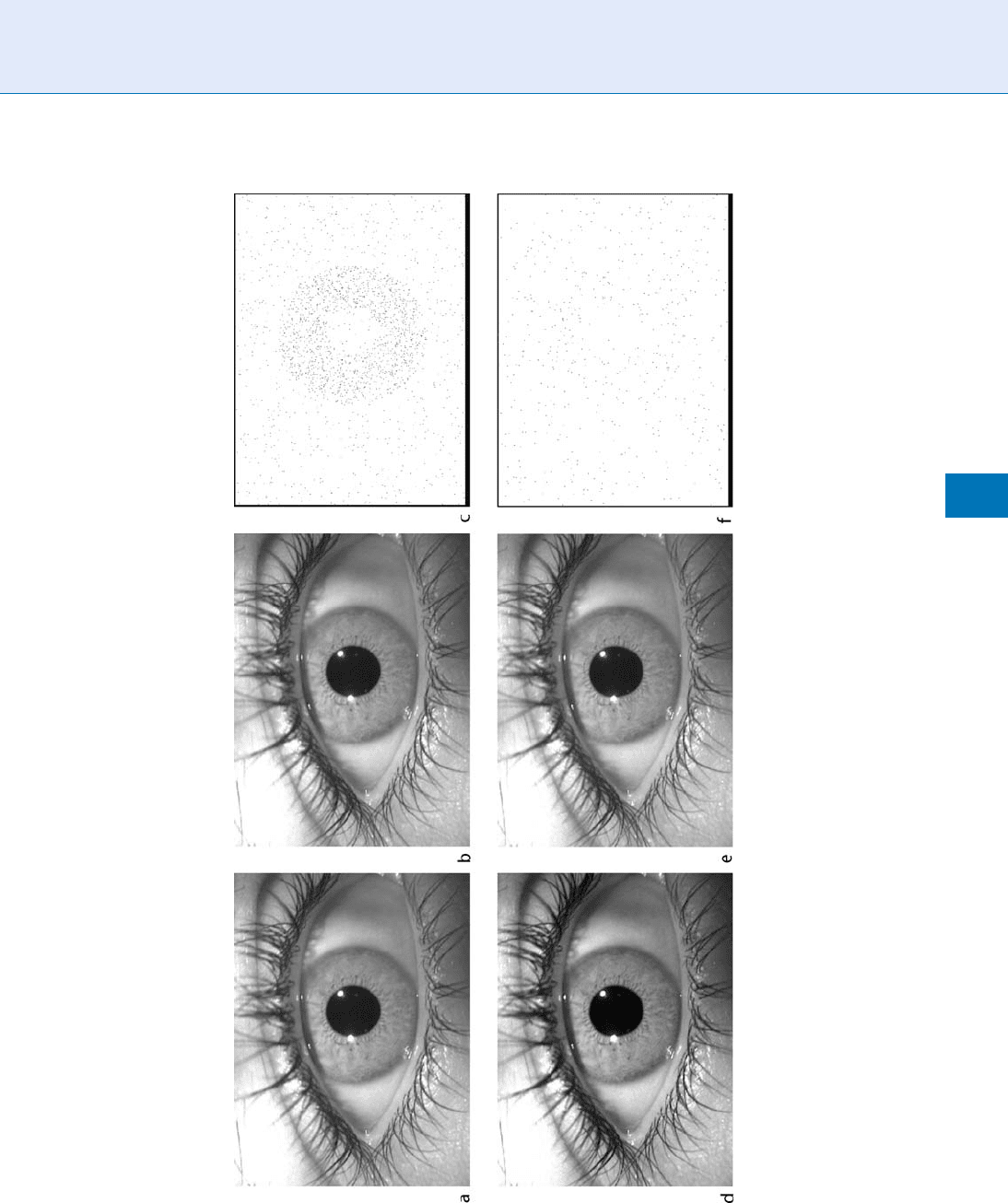
Iris Digital Watermarking. Figure 3 Perceptability of Watermarked Images. Encodings refers to the number of times a watermark is embedded into the host image.
Iris Digital Watermarking
I
783
I
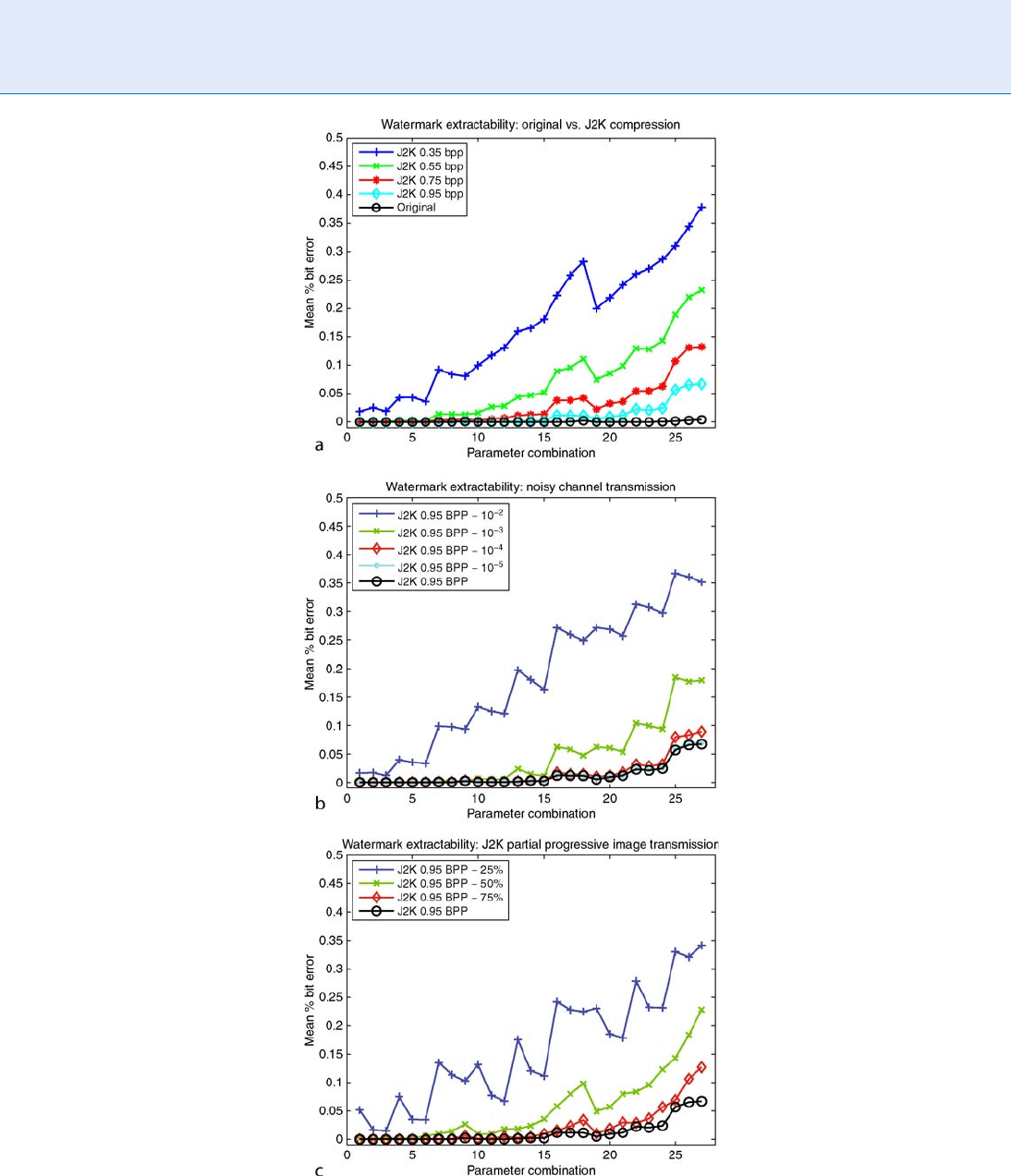
Iris Digital Watermarking. Figure 4 Robustness of the decoder in three application scenarios: (a) Varying levels of
J2K compression (measured in bits per pixel (bpp); (b) J2K compression + varying levels of zero mean white Gaussian
noise (variances shown in legend); and (c) J2K compression + varying levels of partial progressive decoding
(% decoded shown in legend).
784
I
Iris Digital Watermarking
when a biometric feature vector serves as a watermark
and is also used in the authentication stage. In this
scenario, accurate extraction of the watermark is of
utmost importance as small changes in the values of
feature vectors can lead to significant changes in authen-
tication results. Although little or no work exists study-
ing the latter of the two effects, we once again refer
to [9] where the effect of an amplitude modulation
watermarking system on biometric image quality
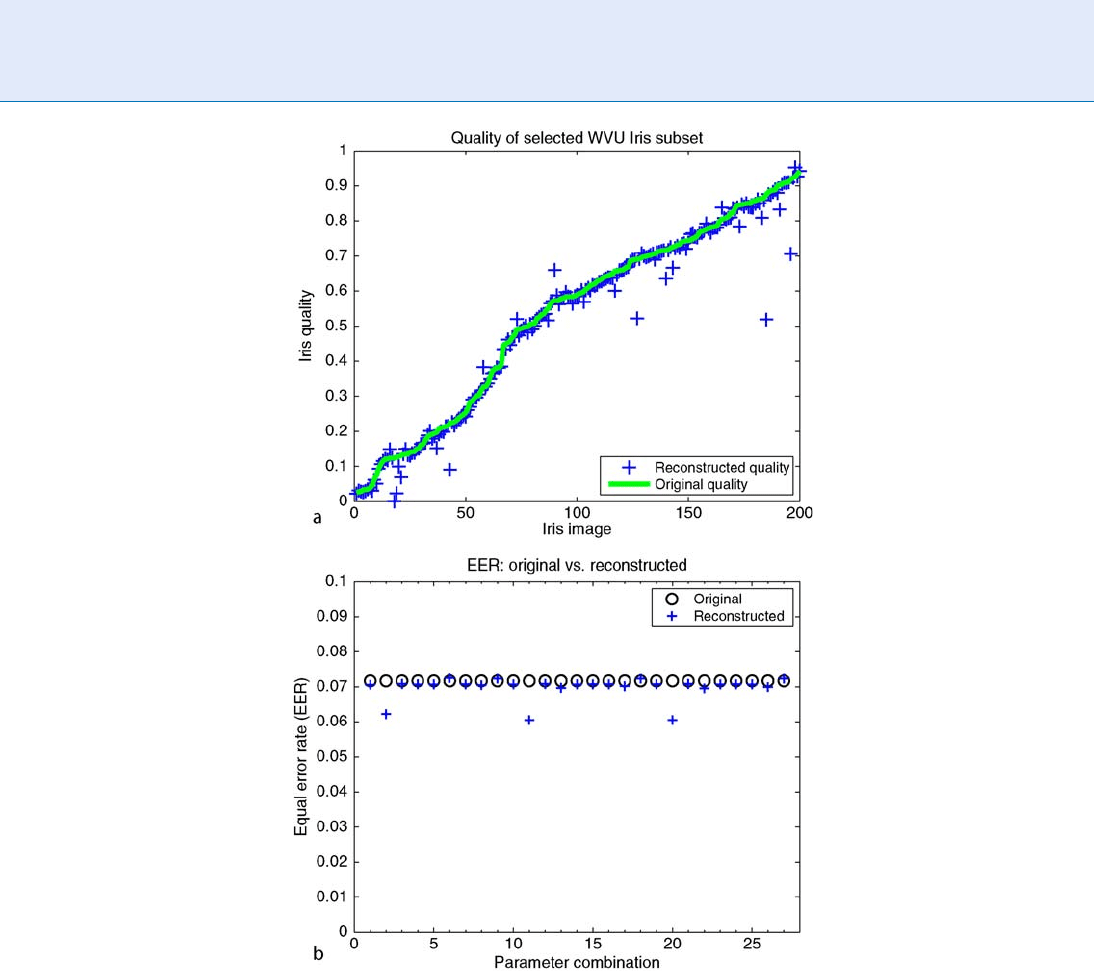
and matching performance is studied. Figure 5 shows
the effect on image quality and matching performance
of the underlying iris biometric system. The graphs
compare the quality and matching results from the
original host images with the images resulting after
watermark extraction and image reconstruction, and
the tables provide averaged results across the entire
dataset.
Much like the three application scenarios men-
tioned earlier, these results provide one example of a
biometric watermarking system that does not produce
unwanted side effects. In particular, image quality is
seldom affected with any level of significance and
matching rates also do not suffer from performance
degradation.
Application scenarios aside, biometric watermark-
ing systems must also deal with attacks or malicious
attempts to subvert a system. Such attacks may involve
removal, alteration, or replacement of the embedded
watermark found in an image. Although some of these
may fall in the application scenarios described earlier,
examples of attacks include rotation, scaling, transla-
tion, cropping, masking, and (re)watermarking. As in
the case of application scenarios, different biometric
watermarking techniques can handle different attacks
with varying degrees of success. Although not specific
to biometric watermarking, Zheng et al. provide an
excellent description of so-called RST (rotation, scal-
ing, translation) invariant watermarking algorithms
in [3]. Often the ability to handle a given attack lies
in the domain in which a biometric watermarking
technique operates. For instance, rotation attacks are
handled with greater ease by watermarking techniques
that operate in transform domains (i.e., Fourier, DCT,
wavelet, etc.). This t ype of attack is arguably more
difficult to handle by techniques that operate in the
spatial domain. Conversely, techniques in the spatial
domain are more likely to handle biometric replace-
ment attacks (i.e., replacing the watermarked iris or
face region of an image), as the biometric ROI can be
easily located in the spatial domain, but more difficult
to localize in a transform domain.
Patents, Tools, and Commercial
Products
Searching the United States Patent Office (USPO) for
‘‘Biometric Watermarking’’ yields well over 100 entries
of varying relevance to the field. The most notable is
titled ‘‘Biometric Watermarks’’ and was issued in 2001
to GTE Service Corporation [12]. This patent outlines
the general schematic for a biometric watermarking
system. A more recent patent issued to Canon by
the USPO relates specifically to iris digital watermark-
ing and includes an embedded watermarking system
in a camera with the intended purpose of associating
a photographers biometric information with images
taken by the camera [13]. There are a few freely
available tools related to digital watermarking and
biometric watermarking exist. For example, Stirmark
Iris Digital Watermarking. Table 3 Watermarking parameter combinations examined in [9]. The first item of the 3-tuple
represents the degree of pixel modulation; second item represents the number of times the watermark is embedded in
the image; the third item represents the proportion of the watermark embedded in the iris portion of the host image.
Further explanations can be found in [9]
1
0.10-
60-
0.67 2
0.10-
60-
0.33 3
0.10-
60-
0.00 4
0.10-
40-
0.67 5
0.10-
40-
0.33 6
0.10-
40-
0.00 7
0.10-
20-
0.67 8
0.10-
20-
0.33 9
0.10-
20-
0.00
10 0.06-
60-0.67
11 0.06-
60-0.33
12 0.06-
60-0.00
13 0.06-
40-0.67
14 0.06-
40-0.33
15 0.06-
40-0.00
16 0.06-
20-0.67
17 0.06-
20-0.33
18 0.06-
20-0.00
19 0.04-
60-0.67
20 0.04-
60-0.33
21 0.04-
60-0.00
22 0.04-
40-0.67
23 0.04-
40-0.33
24 0.04-
40-0.00
25 0.04-
20-0.67
26 0.04-
20-0.33
27 0.04-
20-0.00
Iris Digital Watermarking
I
785
I
Benchmark 4.0 is a software tool designed to perform
robustness testing of image watermarking algorithms
[14]. Another tool, Checkmark, also provides a bed
of attacks to evaluate the robustness of a watermark-
ing system [15]. Many commercial entities offer a
broad range of digital watermarking solutions that
can potentially fall under the category of biometric
watermarking. Perhaps the most w idely known of
such companies is Di giMarc Corporatio n based in
Oregon, US.
Summary
Iris digital watermarking is a technique utilized in
tandem with cryptographic systems to protect iris bio-
metric images. The watermarking scheme can be used
as a mechanism for proving file authenticity, tracking
chain of custody and data reproduction, or affording
a multimodal biometric option, thereby offering an
additional layer of security after data decryption.
A w ide range of watermarking system s exist that
Iris Digital Watermarking. Figure 5 Effect of watermarking on biometric performability: (a) Compares the quality of 200
original host data images vs. the reconstructed images after watermark extraction; (b) Compares the EER across 100
users before watermarking and after image reconstruction; (c) Average image quality before watermarking and after
reconstruction; (d) Average EER (%) before watermarking and after reconstruction across 100 subjects.
786
I
Iris Digital Watermarking

operate in any one of several domains (spatial, Fourier,
DCT, wavelet, etc.). A system’s expected application
profile and threat model will dictate the choice of
watermarking algorithm, the nature of the watermark
to utilize, and a viable set of algorithmic parameters.
Carefully making these dec isions will result in a formi-
dable layer of postdecryption protection without
compromising on the performance aspects of the un-
derlying biometric system(s).
Related Entries
▶ Binding of Biometric and User Data
▶ Biometric Encryption
▶ Biometric System Design
References
1. Tirkel, A.Z., Rankin, G.A., van Schyndel, R.M., Ho, W.J., Mee,
N.R.A., Osborne, C.F.: Electronic Watermark pp. 666–673
(1993)
2. Artz, D.: Digital steganography: hiding data within data. Internet
Computing, IEEE 5(3), 75–80 (May/Jun 2001). DOI 10.1109/
4236.935180
3. Zheng, D., Liu, Y., Zhao, J., El-Saddik, A.: A Survey of RST
Invariant Image Watermarking Algorithms. ACM Comput.
Surv. 39(2), (2007)
4. Ahmad, S., Lu, Z.M.: A joint biometrics and watermarking based
framework for fingerprinting, copyright protection, proof of
ownership, and security applications. Computational Intelli-
gence and Security Workshops, 2007. CISW 2007. International
Conference on pp. 676–679 (15-19 Dec. 2007)
5. Ratha, N.K., Connell, J.H., Bolle, R.M.: Secure data hiding in
wavelet compressed fingerprint images. In: MULTIMEDIA ’00:
Proceedings of the 2000 ACM workshops on Multimedia,
pp. 127–130. ACM, New York, NY, USA (2000). DOI http://
doi.acm.org/10.1145/357744.357902
6. Noore, A., Singh, R., Vatsa, M., Houck, M.M.: Enhancing secu-
rity of fingerprints through contextual biometric watermarking.
Forensic Science International 169, 188–194
7. Low, C.Y., Teoh, A.B.J., Tee, C.: A preliminary study on biometric
watermarking for offline handwritten signature. Telecommuni-
cations and Malaysia International Conference on Communica-
tions, 2007. ICT-MICC 2007. IEEE International Conference on
pp. 691–696 (14-17 May 2007)
8. Maiorana, E., Campisi, P., Neri, A.: Biometric signature authen-
tication using radon transform-based watermarking techniques.
Biometrics Symposium, 2007 pp. 1–6 (11-13 Sept. 2007). DOI
10.1109/BCC.2007.4430543
9. Bartlow, N., Kalka, N., Cukic, B., Ross, A.: Protecting iris images
through asymmetric digital watermarking. Automatic Identifi-
cation Advanced Technologies, 2007 IEEE Workshop on
pp. 192–197 (7-8 June 2007). DOI 10.1109/AUTOID.2007.380618
10. Kutter, M., Jordan, F., Bossen, F.: Digital signature of color
images using amplitude modulation. In: Proc. SPIE EI, San
Jose, CA, pp. 518–526 (1997)
11. Jain, A.K., Uludag, U., Hsu, R.L.: Hiding a face in a fingerprint
image. In: ICPR ’02: Proceedings of the 16 th International
Conference on Pattern Recognition (ICPR’02) Volume 3,
p. 30756. IEEE Computer Society, Washington, DC, USA (2002)
12. Musgrave, C.: Biometric watermarks. Patent 6,208,746, U.S.
Patent and Trademark Office, Washington, D.C. (2001)
13. Morikawa, G., Tokura, G.: Picture taking apparatus and method
of controlling same. Patent 7,305,089, U.S. Patent and Trade-
mark Office, Washington, D.C. (2007)
14. Petitcolas, F.A., Anderson, R.J., Kuhn, M.G.: Attacks on copy-
right marking systems. In: Information Hiding, pp. 218–238
(1998). citeseer.ist.psu.edu/petitcolas98attacks.html
15. Pereira, S., Voloshynovskiy, S., Madueno, M., Marchand-Maillet,
S., Pun, T.: Second generation benchmarking and application
oriented evaluation In: IHW ’01: Proceedings of the 4th
International Workshop on Information Hiding, pp. 340–353
Springer, London, UK (2001)
Iris Encoding and Recognition using
Gabor Wavelets
JOHN DAUGMAN
Cambridge University, Cambridge, UK
Synonyms
Daugman algorithm; IrisCode; Iris2pi
Definition
The method of encoding iris patterns that is used in all
current public deployments of iris recognition technol-
ogy is based on a set of mathematical functions called
▶ Gabor wavelets that analyze and extract the unique
texture of an iris. They encode it in terms of its phase
structure at multiple scales of analysis. When this
phase information is coarsely quantized, it creates a
random bit stream that is suffic iently stable for a given
eye, yet random and diverse for different eyes, that iris
patterns can be recognized very rapidly and reliably
over large databases by a simple test of statistical inde-
pendence. The success of this biometric algorithm may
be attributed in part to certain important properties of
the Gabor wavelets as encoders, and to the simplicity
Iris Encoding and Recognition using Gabor Wavelets
I
787
I

and efficiency of searches for matches when pattern
information is represented in terms of such phase bit
strings.
Introduction
Different biometric modalities use diverse methods for
encoding the features on which they depend. The over-
all goal in designing biome tric encoders is always the
same – maximizing between-class variation while
minimizing within-class variation – but very different
strategies have been developed for representing the
chosen features and their random variation. Even w ith-
in a single modality, such as fingerprint recognition,
some methods compile lists of discrete minutiae coor-
dinates and angles, while other methods encode global
ridge-flow descriptions. Facial representations may
be two-dimensional (‘‘appearance-based’’) or three-
dimensional ‘‘model-based’’); may try to achieve some
degree of pose-invariance, illumination-invariance,
or expression-invariance; and the scale of analysis may
be global (e.g., eigenface decompositions) or focused
on local, high-resolution, detail (e.g., skin texture anal-
ysis). In the case of iris patterns, one does not find any
easily enumerated lists of distinct features like the fin-
gerprint minutiae, nor indeed any sets of features that
even possess established names. Rather, one finds a
plethora of textures spanning many scales of analysis,
a wide spatial frequency range, and which might be
described using many candidate image statistics.
Whereas a natural feature to mark in a fingerprint is
a ridge ending or a bifurcation, in the case of iris
patterns we find random featu res with no simple geo-
metric or graph-like structure, that adhere to no taxon-
omy, and that are defined across many different size
ranges. We need a language rich enough to capture
subtleties like ‘‘mottling’’ and ‘‘modulation,’’ yet simple
enough that all instances are commensurable, and pow-
erful enough to deliver extremely rapid and confident
recognition decisions. What might be such a language?
Most naturally occurring textures lend themselves
well to mathematical description in terms of both
spectral (Fourier-based) and spatially localized proper-
ties. The spectral language captu res predominant
undulations and quasi-coherences that are the essence
of texture, whose interwoven appearance reveals why
this word shares a root with ‘‘textile:’’ texere – ‘‘to
weave.’’ But at the same time, spatial variation in the
undulations destroys any simple coherence, and breaks
symmetries. To describe natural textures effectively
and efficiently, for examp le in order to build a biomet-
ric recognition system based on iris textures, we need
a language that is able to specify both the spatial and
the spectral proper ties well.
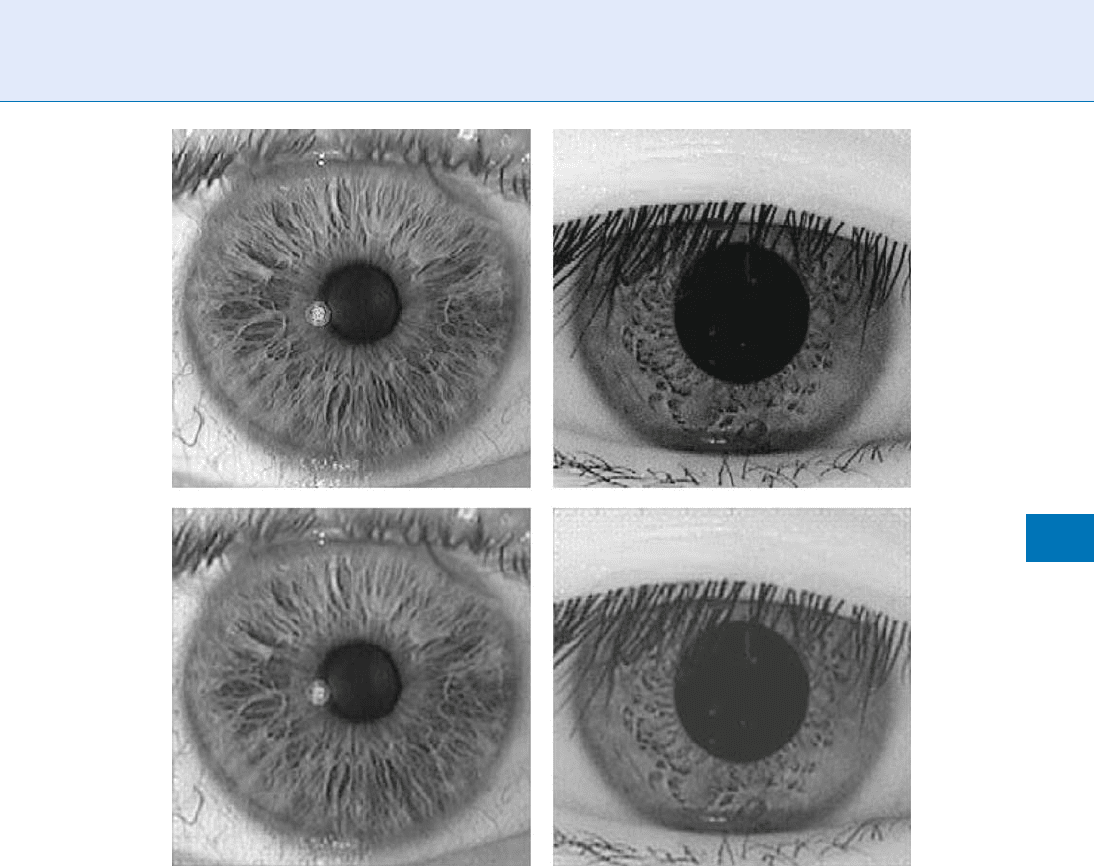
The upper panels of Fig. 1 illustrate two human iris
patterns, Caucasian on the left, oriental on the right.
They reveal rich and unique textural structure, and
also characteristic ethnic differences in their appear-
ance. For example, the Caucasian iris has finer detail
and longer radial correlations, whereas the oriental
iris has somewhat coarser and more isotropic (less
elongated) features, which are also more concentrated
near the pupil. All of these general aspects of iris
patterns – their undulatory textures, their spatial vari-
ation, their statistical structure in correlation distances,
and, above all, their rich randomness, motivated the
author nearly two decades ago to develop a method for
encoding and recognizing iris patterns using a particu-
lar mathematical family of localized undulations called
▶ Gabor wavelets. Today, that algorithm [1, 2] remains
the metho d used in all public deployments of iris
recognition. This chapter reviews some of the essential
aspects of this approach to image analysis, encoding,
and pattern recognition.
Gabor Wavelets as a Complete
Image Basis
Classical signal processing divided broadly into analy-
sis performed in the signal domain (time in the case of
time-varying signals like sound waveforms, or space in
the case of images), versus analysis performed in the
Fourier domain in which the signal is represented as a
linear combination, or superposition, of global sinu-
soids. Although a bedrock of signal processing , Fourier
analysis is hampered by its excessively global perspec-
tive: in the Fourier domain, every coefficient associated
with a particular frequency component summarizes
the presence of that frequency component over the
entire extent of the signal. Similarly, every local point
in the signal has an influence on every coefficient in the
Fourier domain (i.e., on every frequency component).
This extreme, reciprocal, mapping ‘‘from local to global’’
and ‘‘from global to local’’ across the two domains
is reflected in the fact that their respective independent
variables are themselves reciprocals: time versus
788
I
Iris Encoding and Recognition using Gabor Wavelets
(temporal) frequency, as Hertz (1/s); and for images,
space versus spatial frequency (cycles per degree).
In the 1980s a number of mathematicians, most of
them Francophone, began to formulate a new synthesis
of these two domai ns based on a kind of compromise
between the global (spectral) and local (punctate) per-
spectives. It came to be called wavelet theory (translated
from a French neologism “ondelette’’ – a small wave).
The key insight of wavelet theorists like Yves Meyer [3]
and Ingrid Daubechies [4] was that it was possible to
construct complete representations of functions by
superposition of a set of universal elementary
functions all of which were dilates and translates of a
single shape on finite support, forming a dyadic set.
Typically the successive dilation (stretching) factors
were powers of 2, and the translation intervals scaled
reciprocally, so that self-similarity was preserved across
all scales. Originally there were five requirements for
such sets of basis functions to be deemed wavelets: they
must all be (1) dilates and (2) translates of each other;
they must have (3) strictly compact support; (4) all of
their derivatives must exist; and (5) they must be
mutually orthogonal (i.e., have zero inner products
with each other). These constraints and admissibility
Iris Encoding and Recognition using Gabor Wavelets. Figure 1 The upper two panels illustrate the rich textures
found in the iris, and also some typical ethnic differences: on the left is a Caucasian iris, and on the right an oriental iris.
Some significant differences include the longer radial correlation distances and finer detail in (especially blue-eyed)
Caucasians, and the tendency of oriental eyes to have more of their iris texture near the pupil. The lower two panels
show reconstructions of the upper two images using only a sparse discrete set of 2D Gabor wavelets, incorporating
just six spatial frequencies (one octave apart) and six orientations, as seen in Fig. 2.
Iris Encoding and Recognition using Gabor Wavelets
I
789
I
