FitzGerald J., Dennis A., Durcikova A. Business Data Communications and Networking
Подождите немного. Документ загружается.

HANDS-ON ACTIVITY 8C 305
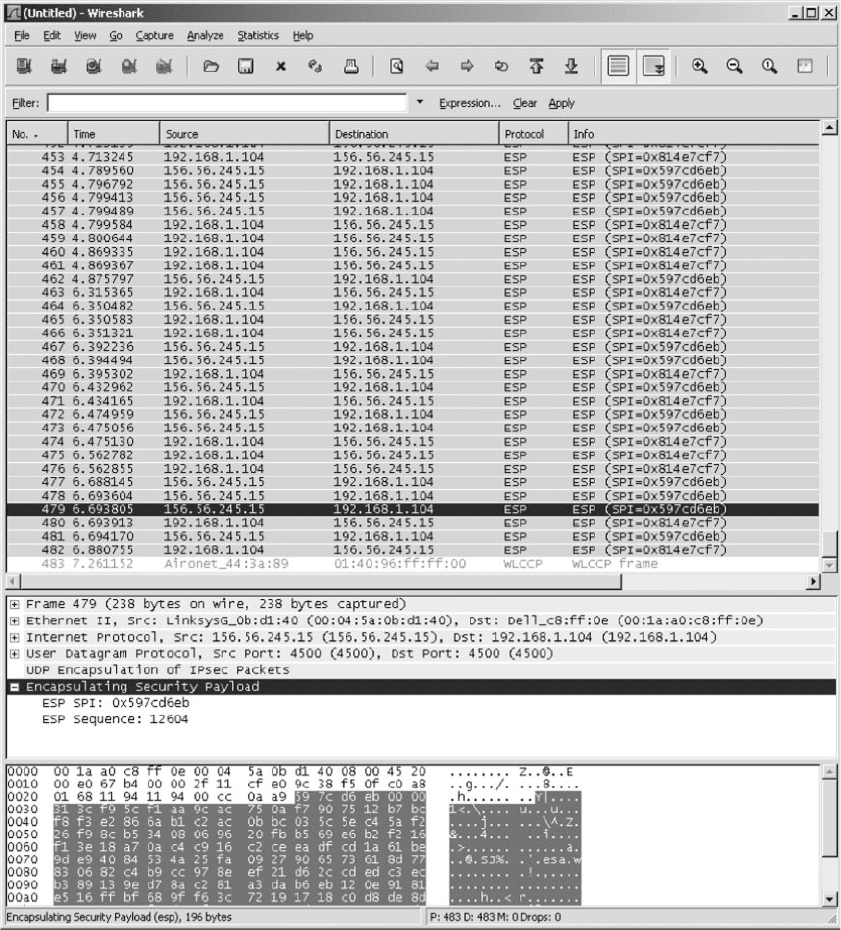
FIGURE 8.19 Viewing encrypted packets
306 CHAPTER 8 WIDE AREA NETWORKS
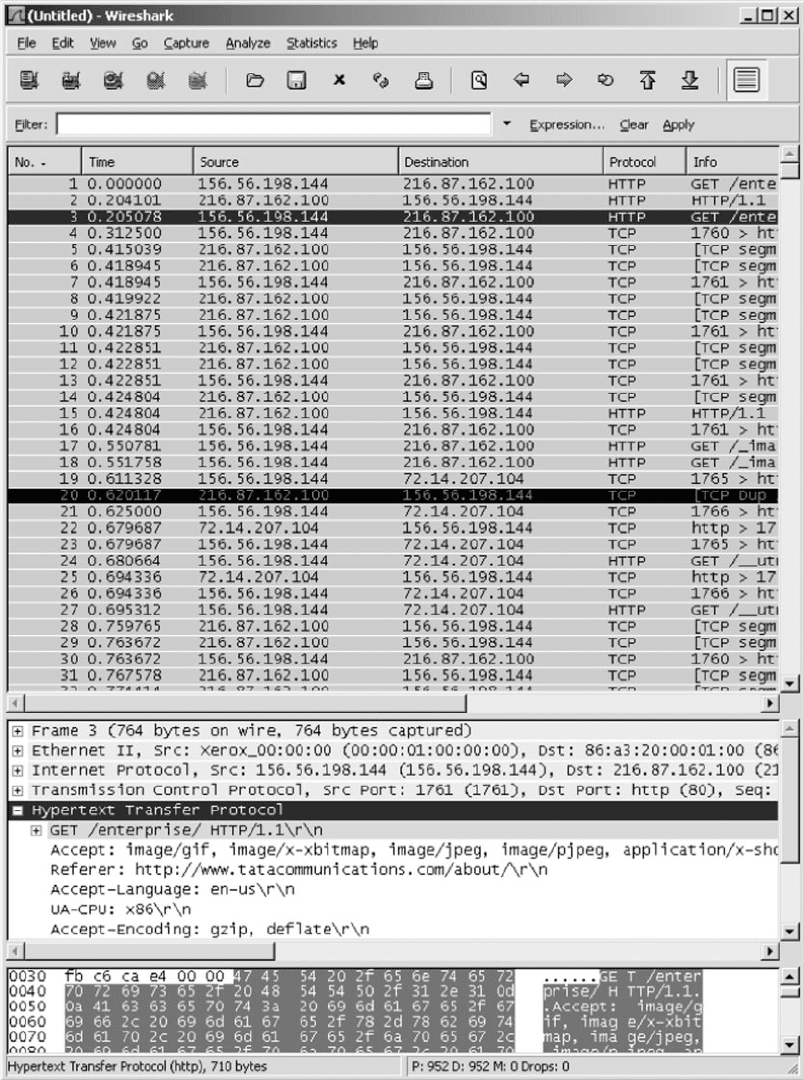
FIGURE 8.20 Packets that enter the VPN tunnel
HANDS-ON ACTIVITY 8C 307
change the size and shape of this window, but it
is not as flexible as a usual window.
2. We will first trace the route from your computers
to two other computers without using the VPN. So
make sure your VPN is not connected.
3. We’ll start by tracing the route from your computer
to a computer on the campus of the site you VPN
into. In my case, I VPN into my university, which
is Indiana University. I can choose to trace the
route to any computer on campus. I’ll choose our
main Web server (www.iu.edu). At the command
prompt, type tracert and the URL of a computer
on your campus.
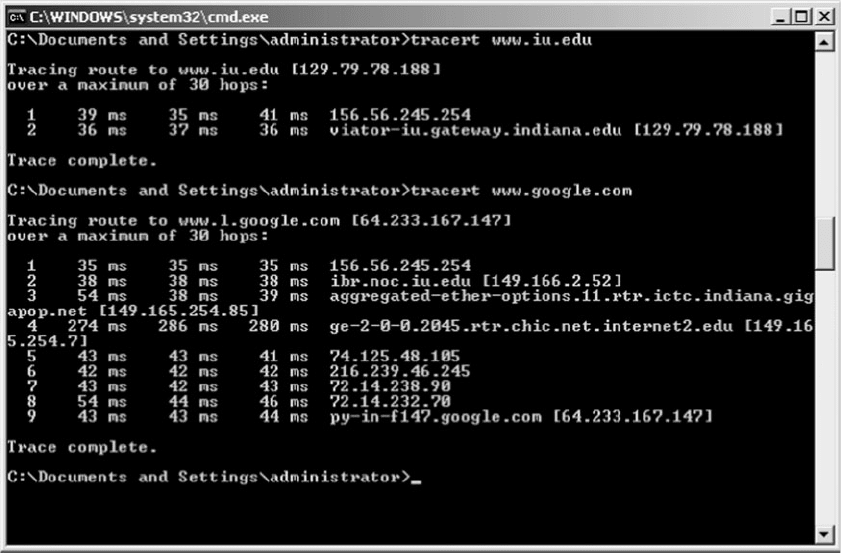
4. The top half of Figure 8.21 shows the route from
my computer to www.iu.edu. There are 18 hops
and it takes about 35 ms. The first hop does not
report information because this feature is turned
off in the router at my house for security reasons.
You can see that my ISP is Comcast (hop 6). If you
compare this to the tracert at the end of Chapter 5,
you’ll notice that my ISP changed (and thus the
route into the Internet changed) between the time I
wrote Chapter 5 and this chapter; Comcast bought
Insight in my town of Bloomington, Indiana.
5. Now trace the route from your computer to
another computer on the Internet. The bottom of
Figure 8.21 shows the route from my computer to
www.google.com. There are 17 hops, and it takes
about 35 ms. You’ll see that the routes to IU and
Google are the same until step 6, and then they
diverge.
6. Next we want to see what happens when you have
a VPN connection. Start your VPN software and
connect into the VPN gateway at your school.
7. Trace the route from your computer to the same
computer as in step 3. At the command prompt,
type tracert and the URL of a computer on your
campus.
8. The top half of Figure 8.22 shows the route from
my computer to www.iu.edu. There are two hops
and it takes about 35 ms. The VPN is in opera-
tion and is transparent to my networking software,
which thinks it is on the same subnet as the VPN
gateway. Therefore, it thinks there is just one hop
from my computer to the subnet’s gateway, the
VPN gateway. You’ll see that the time is still about
35 ms, so the packet is still traveling the s ame 18
hops to get there; it’s just that the tracert packet is
encapsulated and doesn’t see all the hops through
the VPN tunnel.
9. Now do a tracert to the same computer as you
did in step 5. The bottom of Figure 8.22 shows
the route from my computer to www.google.com.
There are nine hops and it takes about 43 ms. Of
course, the first hop is really 17 hops and 35 ms;
this is again hidden from view. As we explained
in the text, when the VPN is connected, all pack-
ets go from your computer to the VPN gateway
on your campus before being routed to the final
destination. You can see from this figure that this
adds additional hops and time to packets that are
not going to your campus, compared to not using
the VPN. You can also see that once the packets
leave the VPN gateway they are ordinary packets;
they are no longer encrypted and protected from
view.
The VPN provides security only to and from
the VPN gateway on your campus, not beyond
it. Therefore, you should use your VPN if you
have security concerns to and from campus (e.g.,
someone sniffing your packets). But if most of
your work is going to be off campus, then the
VPN increases the time it takes to send and
receive packets, and only provides security pro-
tection over the last section from your computer
to your school’s campus. Using the VPN may not
be worth the additional response time it imposes
on you.
Deliverables
1. What are the routes from your computer to your
campus Web server with and without the VPN?
2. What are the routes from your computer to
www.google.com with and without the VPN?

308 CHAPTER 8 WIDE AREA NETWORKS
FIGURE 8.21 TraceRt without a VPN
HANDS-ON ACTIVITY 8C 309
FIGURE 8.22 TraceRt with a VPN
CHAPTER9
THE INTERNET
The Three Faces of Networking
The Three Faces of Networking
Fundamental Concepts Network Technologies
The Internet
Network Management
S
ecurit
y
N
e
t
w
o
r
k
D
e
s
i
g
n
N
e
t
w
o
r
k
M
a
n
a
g
e
m
e
n
t
Application layer
Network layer
Data Link layer
Physical layer
LAN
WLAN
Transport layer
Backbone
WAN
Internet

9.1 INTRODUCTION 311
THIS CHAPTER examines the Internet in more detail to explain
how it works and why it is a network of networks. The chapter also examines
Internet access technologies, such as DSL and cable modem, as well as the
possible future of the Internet
OBJECTIVES
▲
Understand the overall design of the Internet
Be familiar with DSL, cable modem, fiber to the home, and WiMax
Be familiar with possible future directions of the Internet
CHAPTER OUTLINE
▲
9.1 INTRODUCTION
9.2 HOW THE INTERNET WORKS
9.2.1 Basic Architecture
9.2.2 Connecting to an ISP
9.2.3 The Internet Today
9.3 INTERNET ACCESS TECHNOLOGIES
9.3.1 Digital Subscriber Line (DSL)
9.3.2 Cable Modem
9.3.3 Fiber to the Home
9.3.4 WiMax
9.4 THE FUTURE OF THE INTERNET
9.4.1 Internet Governance
9.4.2 Building the Future
9.5 IMPLICATIONS FOR MANAGEMENT
9.1 INTRODUCTION
The Internet is the most used network in the world, but it is also one of the least under-
stood. There is no one network that is the Internet. Instead, the Internet is a network of
networks—a set of separate and distinct networks operated by various national and state
government agencies, nonprofit organizations, and for-profit corporations. The Internet
exists only to the extent that these thousands of separate networks agree to use Internet
protocols and to exchange data packets among one another.
When you are on the Internet, your computer, (iPad, smart phone, etc.) is connected
to the network of an Internet Service Provider (ISP) that provides network services for
you. Messages flow between your client device and the ISP’s network. Suppose you
request a Web page on CNN.com, a Web site that is outside of your ISP’s network.
Your HTTP request flows from your device through your ISP’s network and through
other networks that link your ISP’s network to the network of the ISP that provides
Internet services for CNN. Each of these networks is separate and charges their own
customers for Internet access, but permit traffic from other networks to flow through

312 CHAPTER 9 THE INTERNET
You are here
FIGURE 9.1 The
internet is a lot like the
universe—many
independent systems
linked together
Source: Photo 14 at
http://grin.hq.nasa.gov/
BROWSE/gallaxies.html
them. In many ways, the Internet is like the universe (see Figure 9.1). Each of us works
in our own planet with its own rules (i.e., ISP) but each planet is interconnected with all
the others.
The Internet is simultaneously a strict, rigidly controlled club in which deviance
from the rules is not tolerated and a freewheeling, open marketplace of ideas. All networks
that connect to the Internet must rigidly conform to an unyielding set of standards for the
transport and network layers; without these standards, data communication would not be
possible. At the same time, content and new application protocols are developed freely
and without restriction, and quite literally anyone in the world is allowed to comment
on proposed changes.
In this chapter, we first explain how the Internet really works and look inside one of
the busiest intersections on the Internet, the Chicago network access point, at which 100
separate Internet networks meet to exchange data. We then turn our attention to how you
as an individual can access the Internet and what the Internet may look like in the future.
9.2 HOW THE INTERNET WORKS
9.2.1 Basic Architecture
The Internet is hierarchical in structure. At the top are the very large national Internet
Service Providers (ISPs), such as AT&T and Sprint, that are responsible for large Internet
networks. These national ISPs, called tier 1 ISPs, connect together and exchange data
at network access points (NAPs) (Figure 9.2). For example, AT&T, Sprint, Verizon,
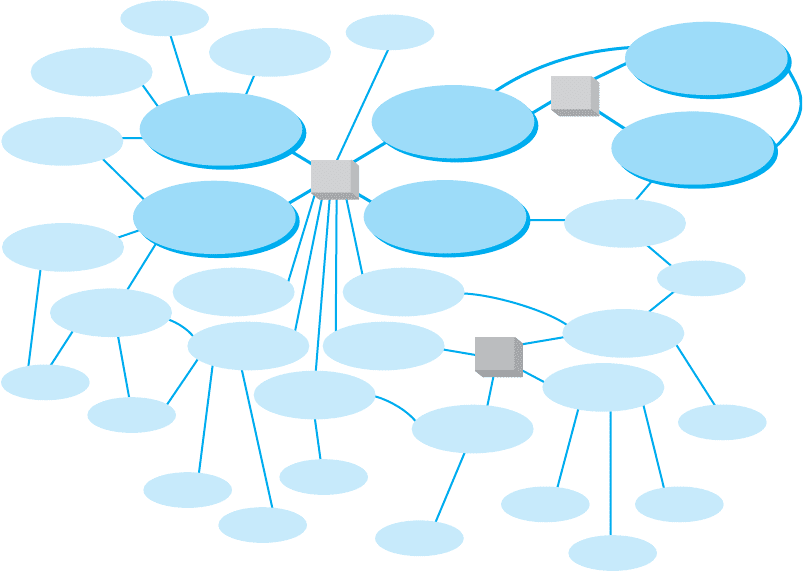
9.2 HOW THE INTERNET WORKS 313
Tier 1 ISP
Tier 1 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 3 ISP
Tier 2 ISP
Tier 2 ISP
Tier 2 ISP
Tier 2 ISP
Tier 2 ISP
Tier 2 ISPTier 2 ISP
Tier 2 ISPTier 2 ISP
Tier 2 ISP
Tier 2 ISP
Tier 2 ISP
Tier 2 ISP
Tier 2 ISP
Tier 1 ISP
Tier 1 ISP
Tier 1 ISP
Tier 1 ISP
NAP
NAP
MAE
FIGURE 9.2 Basic Internet architecture. ISP = Internet service provider;
MAE = metropolitan area exchange; NAP = network access point
Qwest, Level 3, and Global Crossing are all tier 1 ISPs that have a strong presence in
North America.
In the early 1990s, when the Internet was still primarily run by the U.S. National
Science Foundation (NSF), the NSF established four main NAPs in the United States to
connect the major tier 1 ISPs. When the NSF stopped funding the Internet, the companies
running these NAPs began charging the ISPs for connections, so today the NAPs in the
United States are all not-for-profit organizations or commercial enterprises run by various
common carriers such as AT&T and Sprint. As the Internet has grown, so too has the
number of NAPs; today there are about a dozen NAPs in the United States with many
more spread around the world.
Network access points were originally designed to connect only large tier 1 ISPs.
These ISPs in turn provide services for their customers and also to regional ISPs (some-
times called tier 2 ISPs) such as Cogent Communications Comcast, or France Telcom.
These tier 2 ISPs rely on the tier 1 ISPs to transmit their messages to ISPs in other
countries. Tier 2 ISPs, in turn, provide services to their customers and to local ISPs
(sometimes called ISPs) who sell Internet access to individuals. As the number of ISPs
grew, a new form of NAP called a metropolitan area exchange (MAE) emerged. MAEs
are smaller versions of NAPs and typically link a set of regional ISPs whose networks
come together in major cities (Figure 9.2).
314 CHAPTER 9 THE INTERNET
Because most NAPs, MAEs, and ISPs now are run by commercial firms, many of
the early restrictions on who could connect to whom have been lifted. Most now openly
solicit business from all tiers of ISPs and even large organizations. Regional and local
ISPs often will have several connections into other ISPs to provide backup connections
in case one Internet connection fails. In this way, they are not dependent on just one
higher-level ISP.
In general, ISPs at the same level do not charge one another for transferring mes-
sages they exchange. That is, a national tier 1 ISP does not charge another national tier 1
ISP to transmit its messages. This is called peering. Figure 9.2 shows several examples
of peering. It is peering that makes the Internet work and has led to the belief that
the Internet is free. This is true to some extent, but higher-level ISPs normally charge
lower-level ISPs to transmit their data (e.g., a tier 1 will charge a tier 2 and a tier 2 will
charge a tier 3). And of course, any ISP will charge individuals like us for access!
In October 2005, an argument between two national ISPs shut down 45 million
Web sites for a week. The two ISPs had a peering agreement but one complained that
the other was sending it more traffic than it should so it demanded payment and stopped
accepting traffic, leaving large portions of the network isolated from the rest of the
Internet. The dispute was resolved, and they began accepting traffic from each other and
the rest of the Internet again.
Peering has risen to a new level in recent years with the arrival of Internet
Exchange Points (IXPs). An IXP, which is often run by a not-for-profit cooperative
organization, permits any ISP (or large organization) to connect to its network. Some
IXPs charge connection fees, others charge membership fees, and others don’t charge at
all. Once connected to the IXP, the ISP negotiates peering agreements with other ISPs
who are members of the IXP, and then begins exchanging Internet traffic.
In Figure 9.2, each of the ISPs are autonomous systems, as defined in Chapter 5.
Each ISP is responsible for running its own interior routing protocols and for exchang-
ing routing information via the Border Gateway Protocol (BGP) exterior routing pro-
tocol (see Chapter 5) at NAPs, MAEs, IXPs, and any other connection points between
individual ISPs.
9.2.2 Connecting to an ISP
Each of the ISPs is responsible for running its own network that forms part of the Internet.
ISPs make money by charging customers to connect to their part of the Internet. Local
ISPs charge individuals for broadband or dial-up access whereas national and regional
ISPs (and sometimes local ISPs) charge larger organizations for higher-speed access.
Each ISP has one or more points of presence (POP). A POP is simply the place at
which the ISP provides services to its customers. To connect into the Internet, a customer
must establish a circuit from his or her location into the ISP POP. For individuals, this is
often done using a DSL modem or cable modem (Figure 9.3). This connects to the DSL
multiplexer at the ISP and from there to a remote-access server (RAS), which checks
to make sure the user is a valid customer. Once logged in, the user can begin sending
TCP/IP packets from his or her computer to the POP. Figure 9.3 shows a POP using a
switched backbone with a layer-2 switch. The POP backbone can take many forms, as
we discussed in Chapter 7.
