Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.


typically a greyscale image in which finger vein pat-
terns are imaged as dark area.
▶ Finger Vein Biometric Algorithm
Read Noise
For image sensors, each time when a pixel is read out,
there is noise associated with the act of reading the
pixel. This noise is, to first order, independent of the
value of the pixel.
▶ Biometric Sensor and Device, Overview
▶ Iris Device
Real-Time 3D Surface Digitization
Many 3D biometrics applications rely on laser scanners
for surface digitization. Although these devices pro-
duce very accurate 3D coordinates, they have two main
limitations. They are expensive thus prohibiting their
use in a wide scale, and they require the user to stay still
during the acquisition. The latter is because during
acquisition, a laser beam sweeps the object surface,
and thus movement may results to artifacts. 3D acqui-
sition based on the stereoscopic principle is an alterna-
tive without the above limitations, since two plain
cameras are used. However the accuracy of such
devices is usually limited. A solution that is a compro-
mise between the above is using sensors that are based
on the structured light approach. The surface of the
object is illuminated by a l ight pattern (e.g. by means
of a slide or video projector) and the resulting image is
captured by a common camera. By analyzing the de-
formation of this pattern on the surface 3D coordi-
nates may be computed by means of triangulation. The
accuracy of this approach has been shown to be ade-
quate for biometric applications.
▶ Finger Geometry, 3D
Recognition at a Distance
Recognition at a distance is the process of establishing
the identity of humans in a non-intrusive way from a
distance, often without their knowledge. Typically, face
and gait biometrics are used to perform recognition
from small to mid range distance.
▶ Face Recognition, Video-based
Rectilinear
Moving in, consisting of, boun ded by, or characterized
by a straight line or lines. Rectilinear images are those
in which intensity values are recorded as a matrix, w ith
each element in the matrix corresponding to the inten-
sity measured by a single picture element (pixel) in the
image sensor.
▶ Iris Image Data Interchange Formats, Standardization
▶ Iris Standards Progression
Reference Set
Reference set is a set of biometric samples or extracted
features from a biometric trait of a user, which are
stored to perform matching. Stored samples are also
known as templates. Generally, each input biometric
sample will be compared to all the templates in the
reference set in the matching phase. Reference-based
systems are opposed to model-based systems, where
instead of storing genuine samples, a classifier is
trained (or a statistical model is estimated) from the
training set.
▶ Performance Evaluation, Overview
▶ Signature Matching
1110
R
Read Noise

Reflection
When light impinges on a object, part of the light is
reflected, it bounces off the object; part of the light
is transmitted, it passes through the object; and part of
the light is absorbed, it is converted from light into
some other form of energy in the object.
The reflected light can be divided into two compo-
nents, specular and diffus e. A specular reflection is
what you see in a mirror; a single ray of light is
reflected back as a single ray of light in a new direction
determined by the rule that the ang le of reflection with
respect to a normal to the surface equals the angle of
incidence with respect to the same normal. Diffuse
reflection is what you see from a matte surface; a single
ray of light is reflected back over a broad range of
angles. Most materials have specular and diffuse com-
ponents to their reflectivity.
▶ Iris Device
Reflection-Based Touchless Finger
Imaging (RTFI)
RTFI refers to touchless fingerprint sensor.
▶ Fingerprint, Palmprint, Handprint and Soleprint
Sensor
Region-of-Interest (ROI) Encoding
It is often desirable to allocate a coding budget non-
uniformly to an image, especially when compression is
required. This may take the form of space-variant
resolution, so that only some favored region receives
maximal resolution while other areas are encoded
with coarser resolution; or it may take the form of
completely masking out the irrelevant areas. The
capability to specify a Region-of-Interest (ROI) is
built into advanced coding protocols for image com-
pression, especially the JPEG2000 protocol (ISO Stan-
dard 15444) which allows binary masking as well as
code-block selection so that different resolution levels
and different coefficient scaling can be applied to dif-
ferent tiles. The older JPEG protocol (ISO Standard
10918), in its Part 3 extension, also supports variable
quantization for explicitly specifying different quality
levels for different image regions.
In JPEG2000, the MAXSHIF T tool allows specifi-
cation of an ROI of arbitr ary sha pe. ROI methods
have been developed for compact encoding of iris
images so that nearly all of the available coding bud-
get is allocated to the iris itself, and not was ted on
costly irrelevant structures such as eyelashes. In these
methods, the non-iris regions of an image (eyelids,
eyebrows, eyelashes, skin and sclera) are all automati-
cally d etecte d and painted out wi th uniform gray
values before JPEG or JPEG2000 compression, result-
inginalmostnocodingcoefficientsbeingwastedon
them and allowing image file size to be reduced
to 2,000 bytes.
▶ Iris Recognition Performance Under Extreme Image
Compression
Registered Traveler
CATHERINE J. T ILTON
Daon, Reston, VA, USA
Synonyms
Known traveler; Trusted traveler
Definition
Registered Traveler (RT) programs are designed to
expedite legitimate travelers through a border control
or security screening process by conducting a
▶ secu-
rity threat assessment to determine risk levels prior to
acceptance into the program and passage through a
designated travel lane. These programs are generally
Registered Traveler
R
1111
R

voluntary and involve the collection of biographic and
biometric data used in background checks. Often, they
involve the issuance of a secure biometric credential
that can be used as part of an identity verification
process.
Registered Traveler or Trusted Traveler programs
are airline passenger security assessment systems
deployed in the USA and controlled by the transporta-
tion security a dministration (TSA) as public/private
partnerships. Their purpose is to expedite the security
screening procedures for departing air passengers who
have been previously vetted by TSA and deemed, on
the basis of background checks, to be minimal security
risks. To use the expedited fast lanes at airports, trave-
lers must prove their identity and qualification under
the scheme by either fingerprint or iris recognition,
matching their own biometric record that is securely
encrypted on a smartcard issued by TSA and interop-
erable across dozens of US airports.
The larges t such programme is call ed CLEAR oper-
ated by Verified ID, which has enrolled more than
175,000 fee-paying members.
Introduction
Today’s traveling public wants it all – hassle-free, se-
cure, and safe travel. However, security usually means
additional inconvenience. As a result, user-friendliness
is sometimes seen as a trade-off for enhanced security.
In the wake of the events of 9/11, national security and
transportation officials worldwide were faced with this
challenge: How to heighten the security of transporta-
tion, travel, and border systems while minimizing
delays, aggravations, and privacy intrusions?
One idea that has gained some momentum is reg-
istering travelers in advance such that those travelers
can be expedited through one or more of the travel
processes – usually security screening and/or border
control points. The idea is that by prescreening trave-
lers, along with a strong identity authentication
method, they can be segregated into risk categories,
allowing security officials to allocate greater attention
and resources to ‘‘unknown’’ or high-risk travelers [1].
Goals of RT programs generally include the
following [2]:
Enhance security
Facilitate legitimate travel and trade
Protect personal privacy
Participation in registered traveler programs
involves a registration process in which the applicant
provides biographic informati on and enrolls his/her
biometrics. This information is used to conduct risk
assessments (or security threat assessments) that may
include criminal background and watchlist checks. The
cognizant agency then makes an adjudication decision
as to w hether the individual is eligible for the program.
Benefits of participation from a traveler’s perspec-
tive include shorter lines, faster processing, and con-
sistency of experience. So me programs also offer other
commercial benefits (e.g., preferred parking, con-
cession discounts). When used to expedite security
screening, one of the main benefits expressed by parti-
cipants is predictability of wait times, allowing them to
better judge time allowances and thus to spend more
time at home or work prior to travel. This appeals
mostly to frequent business travelers who are willing to
pay for such an advantage. ‘‘The Privium (See ‘‘Example
Systems’’) experience suggests that travelers are a great
deal more willing to submit to fingerprint and iris scans
if they think it will save them time and effort [3].’’
RT programs exist in the US, Europe, and other
locations and are emerging elsewhere. The US program
centers on the security screening function, whereas
many other programs focus on the border control
area (i.e., immigration stations at ports of entry).
Nearly all such programs are implemented at airports;
however, this is not universally true. It is seen by many
as a method for ‘‘simplifying passenger travel’’. A few
such programs are highlighted in the examples section.
The RT Process
The processes used within a registered traveler pro-
gram are similar to those used in typical biometric-
based
▶ credentialing systems. (An example of a
credentialing system is the personal identity verifica-
tion program in the US.) [4] At a high level, the process
comprises three elements: (1) Registration, (2) Authen-
tication (Use), and (3) Administration. Depending on
system architecture (see next section), these can be
further broken down into component operations.
Registration is the process of enrolling and vetting
an applicant to determine and instantiate eligibility.
This generally involves the following steps:
Preenrollment (optional). This step involves the
applicant providing biographical information
(usually via some remote means, such as the
1112
R
Registered Traveler

internet) in advance of in-person, full enrollment.
This may also include the scheduling of the enroll-
ment appointment, receiving instructions, and
payment of any associated fees.
Biographic enrollment. The applicant either pro-
vides the requested biographic data or verifies/
corrects those supplied during preenrollment.
Biographic information would normally include
name, date/place of birth, address, employment,
and relevant identification numbers.
Identity proofing. This entails the applicant providing
one or more identity documents (e.g., birth certifi-
cate, drivers license, passport, or government issued
ID),whicharethenscannedandvalidated.
Biometric enrollment. Usually ten fingerprints as
well as a facial photograph are captured, as these
are the norm for criminal background checking.
Some programs capture additional or alternative
biometrics such as iris images.
Identity investigation . Using the information
provided by the applicant, one or more of the
following checks may be performed as part of
the security threat assessment (STA):
Name-based background checks, which may
include verification of the existence of the
claimed identity
Biometric duplicate checks, to ensure that an
individual is not enrolled into the system under
more than one claimed identity
Criminal history checks
Watchlist checks, including but not limited to
known or suspected terrorists
Adjudication. Based on the results of the STA, the
cognizant authority makes a decision as to appli-
cant eligibility.
Credential issuance (optional) and notification.
Most RT programs issue to approved participants
a physical credential, such as a smartcard (or
register a previously issued credential, such as an
e-Passport) that is used in subsequent processes;
however, this is not strictly required as a central
server-based architecture is also possible. When
used, these credentials serve as the claim of identity
when presented, but also may contain biometrics
that can be used to verify that claim during an
authentication operation (this is discussed further
in the following section).
Authentication is the process of verifying identity
and program participation at the designated point
in the travel process. This usually involves a claim
of identity (either explicit or implicit), biometrically
verifying that id entity against the enrollment and
validating the privilege of the participant. The last
step may include:
Checking the validity of the credential including
expiration, revocation, integrity, and security
features
Checking that the participant’s priv ileges have not
been revoked or other wise invalidated.
Authentication is frequently performed at
(attended) verification kiosks located at RT privilege
lines. The outbound users may need to first show a
boarding pass and an ID (an RT card or a government-
issued ID) before approaching the kiosk. He or she
would then present his or her RT card e-Passport to the
kiosk (in a credential based system), present his or her
biometrics to the sensor when challenged, and be verified
to pass through if his or her biometrics match. In most
schemes, if biometric verification fails, the participant is
moved the head of the regular queue. Some multibio-
metric RT systems allow the trav eler to select their pre-
ferred verification biometric (e.g., fingerprint or iris).
Administration includes both normal system oper-
ation and maintenance functions as well as ongoing
privilege managem ent such as suspension or revoca-
tion of privileges, renewal and re-issuance, and some-
times periodic refresh of eligibility checks (i.e., running
a participant back against the current watchlist).
Architecture
As you might exp ect, several architectural alternatives
exist for RT schemes. Major architectural decisions
include whether a centralized or distributed model
will be used (this primarily relates to where the bio-
metric matching operations are performed) and
whether or not it will be federated (i.e., the degree of
autonomy and commonality of design among service
locations). Other decisions involve whether or not it
will be credential based, single or multimodal, and
whether a one-to-one (1:1) or one-to-many (1:N)
technolog y will be employed.
In a centralized model, most majo r operations are
performed at a central server. Participant facing opera-
tions are still performed locally (for example, informa-
tion collection and biometric captures). However, all
data storage/management and biometric matchin g are
Registered Traveler
R
1113
R
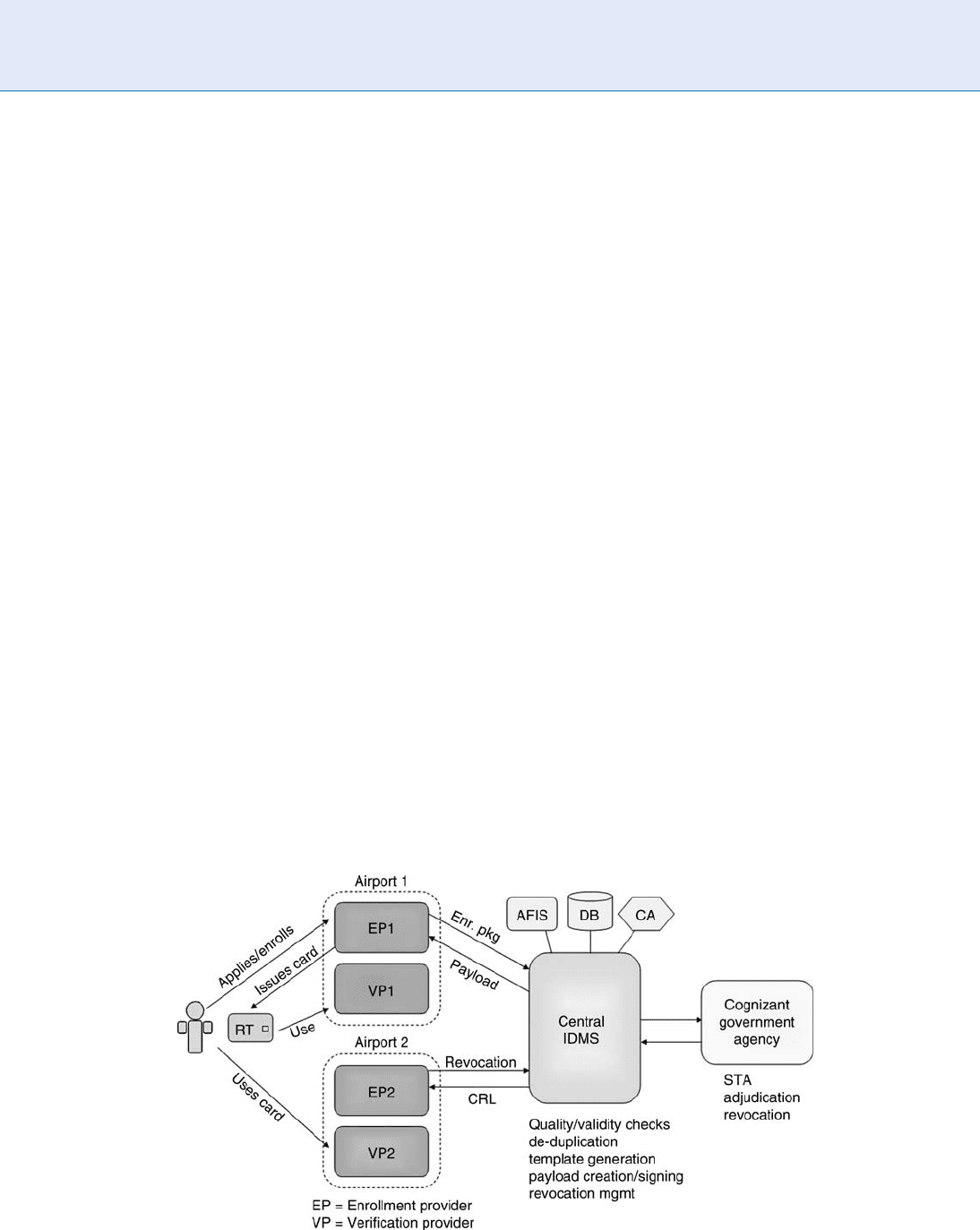
performed at the server. In a distributed model, data
may be stored at the operational site(s) or on a creden-
tial and matching may be performed locally as well.
In a federated system, the architectural model is set
and interfaces between major components are defined,
but the local systems may be defined and controlled by
multiple different entities, although some common
requirements will apply (e.g., security). For example,
in the US Registered Traveler system (see System
Examples, below), which is setup as a public/private
partnership, each enrollment and verification site is
owned and operated by a given
▶ service provider
(SP), which is contracted by a location sponsor (e.g.,
an airport). Design of the specifics of the enrollment
station and verification kiosk, including capture equip-
ment, process flow, and internal databases, is SP-
specific, although elements that affect interoperability
across the system are controlled by a system interoper-
ability specification and conformance testing to that
specification is performed. A central element still
exists, of course, to perform those functions that re-
quire it (e.g., duplicate checking, STA gateway, payload
generation/signin g, etc.)
If a credential-based system is used, then there are a
number of design elements involved including the
card-operating system, data model, and card edge
specification as well as whether the card personaliza-
tion and issuance will be performed centrally, by an SP,
or locally. Depending on the degree of federation, ele-
ments of the card topology (what it looks like on the
outside) may also be strictly specified (e.g., whether/
where a name and facial photo will be printed
on the card). A very basic and important decision is
whether a contact, contactless, or dual-interface card
will be used. Security and privacy models must also
be determined including how the personal information
(including biometric data) will be protected, security
features (topographical and digital), and tamper resis-
tance. For contactless cards, this includes the prevention
of covert reads and sniffing of RF communications
during use. Figure 1 depicts a high level architecture
and process flow for a federated, credential-based RT
system.
In selecting the biometrics to be enrolled, stored,
and verified, needs for background checking and oper-
ational use must be considered. Generally, background
checking requires the collection of ten fingerprints
(tenprints) as this is the standard for such systems;
however, this may or may not be the biometric of
choice for operational use. Considerations such as
social acceptability, accuracy, and ease of use will
drive this decision. To broaden the user population
and reduce false rejections, a multimodal system may
be employed. In this case, multiple biometrics are
captured during enrollment and the participant may
choose a preference at the time of enrollment or at
verification. The need to be able to verify any of the set
of supported modalities will, however, drive up the
cost of the enrollment and verification stations as mul-
tiple capture devices will be required.
It is important to note that in order to perform
duplicate (uniqueness) checking, the biometric collected
Registered Traveler. Figure 1 Federated RT Model.
1114
R
Registered Traveler

for this purpose must be captured (or attempted to be
captured) from all participants – otherwise, the pur-
pose of such checking is defeated. Another impor tant
consideration for credential-based schemes is which
biometrics will be stored on the credential itself, espe-
cially considering space limitations and data transfer
rates of the card. This may constrain the number,
types, and formats of biometric data to be held. For
example, some image data (even compressed) may be
too large to be feasibly considered, or if used, may
further limit the inclusion of other biometr ics. If
fingerprint data are to be included, the number and
selection of fingers must be determined.
Most registered traveler systems use 1:1 biometric
verification; however, it is possible to use a 1:N identi-
fication technology (e.g., iris recognition). In this case,
no claim of identity is made. The participant merely
presents his or her iris(es) at the kiosk and this is
matched against all other participants’ records, result-
ing in an identification (identity returned as a result of
a match) or a no-match. This is usually performed
using a central server model to avoid the need to
duplicate the datab ase and protect all copies.
Today’s systems are generally built around service-
oriented architectures (SOA) taking advantage of the
internet, existing SOA tools, and the many benefits of
this architecture. These include service requester/pro-
vider decoupling, modularity, scalability, and compo-
nent reuse. It is the basis of most large enterprise
architectures and supports business process orchestra-
tion (BPO) workflow implementation, usually as part
of an enterprise service bus (ESB).
Interoperability
In a nonfederated, single operator, closed RT system,
interoperability is not generally an issue. However, in a
federated system, this is critical as the various system
components must be able to properly function and
interact with one another. Areas in which interopera-
bility are most critical include:
Intrasystem (inter-subsystem) interfaces
Card edge and data model
Security
Examples of intersubsystem interfaces include
those between an enrollment station/system and the
central Identity Management System (IDMS), between
the IDMS and the STA/adjudication agency, and
between the ID MS and the verification station/system.
The enrollment system must transmit collected ‘‘en-
rollment packages’’ to the IDMS for processing. The
data and messaging formats as well as the communica-
tion protocols must therefore be defined. This includes
the format of the biometric data. It is preferred that the
submitted biometric information be in raw image for-
mat with minimal compression; however, some pre-
processing and compression are usually required. For
example, fingerprint data are normally transferred as
three ‘‘slap’’ images in ANSI/NIST ITL1–2000/7 Type-
14 record format using WSQ compression [5]. Mes-
saging protocols are often Web services based, using a
‘‘SOAP over HTTP’’ XML-based implementation. In
addition to the basic set of messages required to per-
form an enrollment, additional messaging is required
to handle a host of error conditions and administrative
needs. These include those related to updates, fees, and
revocation.
With respect to an interoperable credential, the
challenge in a federated system is that a credential
produced by one service provider can be reliably and
securely read and verified by a different provider. This
generally requires a common form factor (e.g., ISO
card), a common ‘‘card edge’’ or card interface/com-
mand set, and a common data model. The card appli-
cation must be accessible and the security mechanisms
usable by all authorized entities. A good model for this
is the US PIV program already mentioned and the
associated technical guidance, most notably NIST
SP800–73 [6]. As an alternative, systems can leverage
the e-Passport as an inte roperable, biometrically-en-
abled credential, w ithout the lost and logistics of issu-
ing another. Common biometric data formats are also
critical for interoperable use across multip le airport
kiosks. For example , fingerprint data may be stored
as ISO/IEC 19794–2 minutiae templates [7]. See also
the chapter on Standardization for more information
on biometric data interchange formats and technical
interfaces.
Security is important in all RT systems, but
becomes a bit trickier in federated systems due to the
key management challenges. The intersubsystem mes-
sages should be signed and either encrypted or passed
via an encrypted channel (i.e., SSL/TLS) using stan-
dard cryptographic protocols. Biometrics on a creden-
tial can be protected by one of the following means:
PIN protection, biometric data encry ption, and (card/
reader) mutual authentication. In all the cases, the
biometrics should be digitally signed either directly or
Registered Traveler
R
1115
R

via a container hashing/signing scheme such as that
used by ICAO for the ePassports.
Example Systems
This section takes a look at a few example registered
traveler system implementations.
Privium
An early, and successful showcase, registered traveler
program is the Privium system that was first intro-
duced in 2002 at Schiphol airpor t in Amsterdam (fol-
lowing a one-year pilot), where participants are
charged €99 for the privilege of bypassing the long
queues at immigration (passport control).
This is a credential-based system where the iris data
are stored on a smartcard issued to the participant. The
enrolled iris data are not stored in a central database –
only on the card, which also contains passport data.
Any temporary use of this data is immediately pur-
ged after use to comply with Dutch privacy laws.
Enrollment includes a background check. At the Pri-
vium verification station, a 1:1 biometric match is
performed against the iris template stored on the
Privium card.
The program is available to anyone with a Europe-
an Economic Area (EEA) passport. It is said to cut the
time spent at passport control to 10–15 s and queue
time by up to 30 min [3]. Besides fast-track border
passages, a separate check-in zone and priority parking
are offered (Privium Plus). Participants may check in
at the business class desk regardless of the class of ticket
they hold. Online application and appointments
are available. Onsite registration takes 15–20 min
and includes inspection of identity documents, iris
enrollment, and instructions on system operation.
The Privium card is good for 4 years, but is renewed
annually [8].
UK IRIS
The UK Home Office Border & Immigration Agency
introduced its Iris Recognition Immigration System
(IRIS) in March 2006, as a free service to the traveling
public both to enhance their experience and to reduce
manned immigration platforms. It is the first phase of
the UK e-Borders’ initiative to modernize immigration
controls. Participation allows registered passengers to
enter the UK without queuing to see an immigration
officer at passport control [9]. The intent is to enhance
both security and efficiency.
The Home Office says ‘‘Successfully enrolled pas-
sengers can enter the United Kingdom through auto-
mated immigration control barriers after looking into
an iris recognition camera.’’ Like the Privium program,
IRIS uses iris recognition technology ‘‘because it is a
fast, secure, and fraud-resistant way to verify passen-
gers’ identities. This makes it an ideal biometric for
secure yet expedited clearance [9]’’. It is operational
at Heathrow, Gatwick, Manchester, and Birmingham
airports where enrollment rooms are provided. Enroll-
ment takes approximately five to ten minutes.
Installation followed a trial in 2002 at Heathrow in
which 200 selected passengers were enrolled. This was a
joint project by British Airports Authority, the Immi-
gration Service, British Airways, and Virgin Atlantic
Airways. Figure 2 shows an IRIS verification station
(barrier) at a UK arrival hall. Note the inclusion of
multiple iris cam eras mounted at various heights.
No fingerprint data are collected during IRIS
enrollment – just iris and facial images – although an
interview by an immigration official is conducted. No
credentials are issued. Participation is voluntary and a
marketing campaign is in place, targeting non-EEA
foreign nationals. This has been a very popular system
to date. As of Februar y 2007, 61,000 people had
registered. The original estimate when the program
was announced was t hat over 1 million would be
registered within the first five years.
US Registered Traveler
The United States piloted a registered traveler program
in 2005 at five airports as part of a technology evalua-
tion. Based on the results (including the popularity of
the program which extended the original timeframe)
and one additional private installation, a broader in-
teroperable, national pilot system was deployed in late
2006. The US RT scheme is a fully fee-based public-
private partnership. It uses a credential-based, feder-
ated architecture in which serv ice providers contract
with sponsors (airports/airlines) to operate the system.
A central IDMS operated by the American Associa-
tion of Airport Executives (AAAE) performs the func-
tions identified in Fig. 1. The Transportation Security
1116
R
Registered Traveler

Administration oversees the program and performs all
eligibility adjudications.
As a federated system, an interoperability specifica-
tion was developed by a group called the Registered
Traveler Interoperability Consortium (RTIC). This
group, which included airport operators, technology
vendors, and system integrators with participation
from the TSA, developed the specification over a
4 month period [10]. The TSA developed the program
‘‘to provide expedited security screening for passengers
who volunteer to undergo a TSA-conducted security
threat assessment (STA) in order to confirm that they
do not pose or are not suspected of posing a threat to
transportation or national security [2].’’ The process
generally follows that described in the ‘‘Process’’
section earlier.
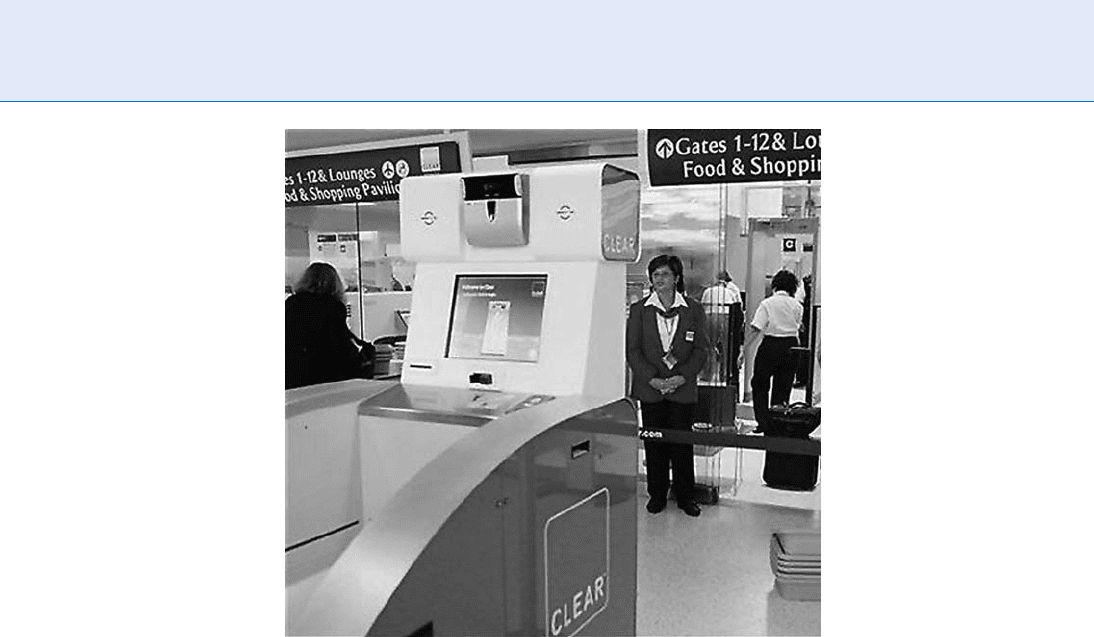
By December 2008, 20 airports had deployed the
RT system and 200,000 par ticipants had been enrolled,
and over 2 million trips made through RT lanes. At this
point, seven vendors had qualified as service providers.
Participants can verify (against their RT card) using
either fingerprint or iris recognition. Figure 3 depicts
one of the US RT airport installations.
Canpass/Nexus-Air
In 2002, the Canadian Customs and Revenue Agency
(CCRA) and Citizenship and Immigration Canada
piloted an ‘‘express lane’’ through customs and immi-
gration based on iris recognition. It is operational at
airports in eight of the largest Canadian cities. The
program allows preapproved low-risk air travelers to
clear customs and immigration by using a self-service
kiosk.
The goal was to streamline airport operations while
maintaining a safe and secure border.
Now run by the Canada Border Services Agency
(CBSA), this system was subsequently expanded via a
bilateral Canada/US agreement into the NEXUS-AIR
program which pre-clears travelers returning to the US
from all major Canadian airports. CANPASS likewise
pre-clears travelers returning from US (and some other
international) locations.
Self-service kiosks use iris recognition to verify
CANPASS membership. Through an agreement with
CATSA, NEXUS-AIR members may also use the prior-
ity la ne through the security screening checkpoint. In
2007, fees were $80 CDN. Key findings of a 2006 pilot
evaluation found that par ticipants were extremely
satisfied with the program and reported saving an
average of 27 minutes per passage. According to a
survey conducted by EKOS Research Associates, the
average NEXUS-Air participant enters Canada 12.8
times per year [11].
Others
RT systems have been implemented in other countries
besides those highlighted earlier. For example, Germany
has deployed a system in Frankfurt. Japan has recently
Registered Traveler. Figure 2 UK IRIS Barrier.
Registered Traveler
R
1117
R
announced an RT component to their Japan Biometrics
Identification (Border) system. And the EU has been
investigating the possibility of an ‘‘international’’ RT
program.
Issues and Considerations
Although apparently popular and workable, some
issues and considerations exist with the establishment
and use of RT systems.
Usability encompasses a range of issues related to
ergonomics, accessibility, user interface, general ease of
use, universality, and social acceptance. Biometric sys-
tems are typically not a ‘‘one-size fits all’’ arrangement,
and care must be taken in their design to make them as
usable as possible to the broadest possible use r popu-
lation. For example, nearly every biometric technology
has a finite failure to enroll rate and some schemes are
not able to be used by disabled individuals.
Privacy concerns also must be dealt with sensitively.
Systems must take privacy considerations into account
from the earliest point in system design and gover-
nance. Fortunate ly, this seems to be the case in the
examples noted earlier.
Criticism has been levied against RT schemes as
being a ‘‘pay to go to the head of the line’’ rather
than a security improvement program – a so-called
‘‘Lexus line’’. ‘‘Not everyone is comfortable with what
amounts to a two-tier system: some say it unfairly
disadvantages infrequent travellers, and may make
them susceptible to undue scrutiny [12].’’
Summary
Biometric-based registered traveler programs are not
only becoming more popular but also being proved to
be workable and to provide benefits both to the imple-
menters (i.e., governments and airports) and to the
traveling public. Althoug h similar in many areas, a
variety of different schemes, processes, and architec-
tures are employed to implement these programs.
Biometrics are used both in the registration process,
as part of the eligibility determination, and in the
authentication process, during operational use to
verify identity as a precleared program member.
Related Entries
▶ Border Management Applications
▶ Iris Recognition at Airports and Border-Crossings
▶ Standardization
▶ System Design
Registered Traveler. Figure 3 US Registered Traveler System.
1118
R
Registered Traveler

References
1. Registered Traveler Forum: What is an RT Program? (undated,
online), http://www.registered-traveler-forum.com/
2. Transportation Security Administration: Registered Traveler
page: http://www.tsa.gov/what_we_do/rt/index.shtm
3. Taylor, R.: All Eyes on Airport Security. The Guardian, 29 April
2004, http://www.guardian.co.uk/travel/2004/apr/29/travelnews1
4. Federal Information Processing Standard (FIPS) 201–1, Personal
Identity Verification (PIV) of Federal Employees and Contrac-
tors, March 2006, NIST, http://csrc.nist.gov/groups/SNS/piv/
index.html
5. ANSI/NIST ITL1–2000, Data Format for the Interchange of
Fingerpint, Facial, & Scar Mark and Tatoo (SMT) Information,
July 2000
6. NIST Special Publication 800–73–1, Interfaces for Personal Iden-
tity Verification, April 2006, http://csrc.nist.gov/publications/
nistpubs/800–73–1/sp800–73–1v7-April20–2006.pdf
7. ISO/IEC 19794, Biometric Data Interchange Formats, Parts 1–10
8. Amsterdam Airport Schiphol, Privium Program website: http://
www.schiphol.nl/privium/privium.jsp
9. Home Office, Border & Immigration Agency, IRIS project web-
site: http://www.ind.homeoffice.gov.uk/applying/iris/
10. Registered Traveler Interoperability Consortium, RTIC Techni-
cal Interoperability Specification, Ver 1.2, 2 May 2007, http://
www.rtconsortium.org/
11. Canada Border Security Agency (CBSA), NEXUS Air Pilot Proj-
ect Evaluation Study, http://cbsa-asfc.gc.ca/agency-agence/
reports-rapports/ae-ve/2006/nexus_air-eng.html#note_1
12. Calder, S.: How to bypass passport queues and leap the UK
immigration hurdle in the blink of an eye. The Indepen-
dent, 13 Aug 2007, http://travel.independent.co.uk/biztravel/
article2872060.ece
Remote Authentication
JUDITH MARKOWITZ
J. Markowitz, Consultants, Chicago, IL, USA
Synonyms
e-authentication, Remote access (par tial); Remote
monitoring (partial); Remote verification
Definition
As with any form of authentication, remote authenti-
cation involves the verification of a person’s claim of
identity. What makes remote authentication different
is that it is performed on individuals located beyond
the physical boundaries of the organization – what
some call as the
▶ extended enterprise.
Remote authentication is distinct from contactless
and at-a-distance. Those two methods refer to the
absence of direct contact or proximity between the
individual being authenticated and a biometric sensor.
Their focus is on the physical relationship between the
individual and the sensor.
In contrast, remote authentication says nothing
about the proximity of the user to the input device.
Both the user and the device are outside the perimeter
of the enterprise and may involve contact, contactless,
or at-a-distance input of biometric samples.
Remote authentication is also distinct from remote
identification. ‘‘Authentication’’ is a synonym for veri-
fication which means the individual has made a claim
of identity and the function of the biometric system is
to determine whether the claim is valid.
Introduction
Historically the boundaries of enterprises, whether
they were private corporations or government
agencies, were largely defined by brick and mortar.
Anyone wanting to do business with the enterprise
would appear in person and their identity would be
validated in situ. The primary forms of remote access
were via wireline telephone and mail, and remote au-
thentication was performed by humans.
Today, communication, transactions, and access
to information are available to anyone who has any
kind of telephone or Web-enabled computing device.
This extended enterprise is an essential co mponent of
e-government and e-business which, in turn, are fueled
by the Internet, globalization, and the mobile revolu-
tion. Furthermore, the individuals accessing the enter-
prise remotely include employees as well as partners,
suppliers, customers, and the public. Furthermore,
enterprises must specify the policies and procedures
that govern the access granted to each of these indivi-
duals and groups.
Access to the extended enterpris e has become in-
creasingly electronic and dominated by automation,
including
▶ interactive voice response (IVR) systems,
email, chat, SMS, and Web sites.
The growth of remote access has exposed the failure
of ID + password/PIN security to prevent or even
attenuate unauthorized access to personal data. There
has been a global escalation of identity theft and the
perpetration of new types of fraud [1]. In response,
security-enhancing regulations have been promulgated
Remote Authentication
R
1119
R
