Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.


at national and international levels. In the United
States, alone, regulators now mandate multi-factor
security for financial services [2–4], health care [5],
and telecommunications [6].
The rise of remote access, concerns about the abili-
ty of existing authentication methods to prevent un-
authorized access, regulation, and other factors have
enhanced the attractiveness of biometrics for automat-
ing remote authentication. According to the National
Institute of Standards and Technology’s (NIST) publi-
cation Introduction to Public Key Technology and the
Federal PKI Infrastructure [7] ‘‘biometrics provide a
very high level of security because the authentication
is directly related to a unique physical characteristic of
the user which is more difficult to counterfeit.’’ (NIST
SP 800–32 pp. 8–9.) Biometrics is ideally suited to
remote authentication because it binds the authentica-
tion event to the physical presence of the human
claimant – even when the event is performed with a
remote user.
Levels of Assurance
Any application requiring authentication can be de-
scribed in terms of its security level, the degree of
potential harm or impact that an authentic ation error
would cause (from minor inconvenience to criminal
offenses and threat to personal safety), and the likeli-
hood that such harm or impact will occur. Those
considerations become extremely important when the
application must authenticate remote users. In re-
sponse to concern about such issues the United States
Office of Management and Budget (OMB) Publisher
E-Authentication Guidance for Federal Agencies [8]to
assist U.S. federal agencies implementing the ‘‘e-Gov’’
program.
OMB’s Guidance defines four levels of authentica-
tion security (called ‘‘assurance levels’’). Table 1 corre-
lates each of the levels with the damage that could
occur as the result of an authenticati on error and the
potential harm to the enterprise.
The National Institute of Standards and Tech-
nology (NIST) translated the OMB’s assurance levels
into electronic authentication solutions and published
them as Electronic Authentication Guideline (NIST SP
800–63) [9]. Technical committee MI (Biometrics)
The American National Standards Institute/InterNa-
tional Committee for Information Technology Stan-
dards (ANSI/INCITS) extended NIST’s categories to
include biometrics and published its work as Study
Report on Biometrics in E-Authentication (M1/07–
0185) [10].
The following provides a summary of assurance
levels in those three publications. The italicized de-
scription of each level is from Appendix A of OMB
04-04 [8]
Level 1: Little or no confidence in the asserted iden-
tity’s validity is required. (OMB Appendix A p. 3.)
There needs to be some assurance that the claimant
is the same person who originally registered.
A single authentication method is sufficient, such
as a plaintext password. No cryptographic methods
are required and no effort is invoked to prevent an
eavesdropper from discovering a password or other
secret that might be used for authentication.
Biometrics: ‘‘It is likely biometric technologies used
alone would be stronger than the necessary security
at this level.’’ (American National Standards Insti-
tute/InterNational Committee for Information
Technology Standards (ANSI/INCITS) 2007 Study
Report on Biometrics in E-Authentication (M1/
07–0185). p. 16).
Remote Authentication. Table 1 Maximum Potential Impacts for Each Assurance Level (from OMB M 04-04) [2]
Potential Impact Categories for Authentication Errors
Assurance Level Impact Profiles
123 4
Inconvenience, distress or damage to standing or reputation Low Mod Mod High
Financial loss or agency liability Low Mod Mod High
Harm to agency programs or public interests N/A Low Mod High
Unauthorized release of sensitive information N/A Low Mod High
Personal safety N/A N/A Low Mod High
Civil or criminal violations N/A Low Mod High
1120
R
Remote Authentication

Examples:
A user presents a self-registered name and user
ID (e.g., a password) as part of creating a per-
sonalized space on a Web site or in a social
network (e.g., MyYahoo or Facebook) where
little or no sensitive, personal information is
stored.
A user participates in an online discussion
group that does not request identifying infor-
mation beyond participant name and organiza-
tion name.
Level 2: Some confid ence in the asserted identity’s
validity [2] is required. This level requires only
single-factor authentication plus approved crypto-
graphic techniques. These credentials are appropri-
ate for operations that require, a user’s identity
details be verified independently during the initial
registration (Bolton, Joshua 2003 E-Authentication
Guidance for Federal Agencies (Memorandum M-
04-04) Office of Management and Budget (OMB)
Appendix A p.3).
Biometrics: ‘‘There is a contention that biometrics
cannot be considered secrets and therefore there is
language in this assurance level that prohibits the
sharing of secrets. This limitation can be overcome,
however, if there are countermeasures put in place
to mitigate the concerns about the sharing of au-
thentication secrets. In particular, through liveness
detection at the point of acquisition and the use
of approved cryptographic techniques to protect
transmission.’’ (ANSI/INCITS Op. cit. p. 16.)
A biometric would be suitable and could be stron-
ger than the security required for this level,
especially content-bearing biometrics, such as
▶ text-dependent speaker authentication because
they are two-factor techniques (biometric +
knowledge).
Examples:
A user subscribes to an online educational ser-
vice that must authenticate the person in order
to present the appropriate course material, as-
sign grades, or demonstrate that the user has
satisfactorily completed the training . The pri-
mary risk is that an unauthorized third party
may gain access to the grades.
A beneficiary changes her or his address of
record through the web site of an insurance
company. The primary risk is missing mails
that are sent to the beneficiary’s address.
The insurance company must assess the risk
that an unauthorized individual would access
the information.
Level 3: High confidence in the asserted identity’s
validity [ 2] is required. This level requires a mini-
mum of two authentication factors (e.g., a one-
time password and a biometric). The claimant
must demonstrate that she or he controls the au-
thentication devices (called ‘‘tokens’’). Cr yptogra-
phy must be used to protect the authentication
token against man-in-the-middle, replay, and
other attacks.
Biometrics: ‘‘Assurance Level 3... specifically calls
out the use of biometrics as an op tion in order for
the claimant to prove that he or she controls the
token.’’ (ANSI/INCITS Op. cit. p. 17).
Examples:
A patent attorney electronically submits confi-
dential patent information to the United States
Patent and Trademark Office. Improper disclo-
sure would give competitors a competitive
advantage.
A bank customer uses online or telephone
banking to access account information or trans-
fer restricted amounts of funds.
A corrections agency must monitor non-violent
criminal offenders in home-incarceration and
community-release programs.
An employee or contractor uses a remote system
giving her or him access to sensitive, personal
client information. The transactions occur over
the Internet. The sensitive personal information
available to the employee creates a moderate
potential impact for unauthorized release.
Level 4: Very high confidence in the asserted identity’s
validity [2]. This level requires a minimum of two-
factor authentication that employs the strongest
authentication and cryptographic techniques that
can be applied to remote access.
Biometrics: ‘‘Assurance Level 4 still requires two-
factor authentication and does not prohibit the use
of biometrics as an option in order for the claimant
to prove that he or she controls the token.’’ (ANSI/
INCITS Op. cit. p. 17).
Examples:
A law enforcement official accesses a law enfor-
cement database containing criminal records.
Unauthorized access could raise privacy issues
and/or compromise investigations.
Remote Authentication
R
1121
R

A bank customer uses online or telephone
banking to transfer unrestricted amounts of
funds
A physician uses a remote system to access the
medical records of a patient.
Architectures for Remote
Authentication
Architectures used for biometric remote-authentication
range from highly centralized to widely distributed.
There are two defining elements of those architectures
and they are:
Where reference template/models are stored
Where matching is performed.
ANSI/INCITS’ Study Report on Biometrics in E-Authen-
tication [10] examines four storage and matching
locations:
Central Server
Client/Workstation
Device/Sensor
Physical Token
Central Server
It is a centrally-located computer, sometimes called the
‘‘biometric authentication server.’’ In remote authenti-
cation architectures the ser ver need not be co-resident
with the other resources involved in the authentication
operations, including the biometric verification
engine.
Storage
The most widely-used storage mechanism for remote
authentication is to house all biometric reference mod-
els in a centralized repository that supports authenti-
cation from multiple locations. This approach
1. Allows the enterprise to maintain control over the
reference templates/models
2. Facilitates frequently recurring operations, notably
Adding templates/models for new users
Updating data in the existing templates/models
(adaptation)
Deleting templates/models for users who have been
removed from the system
3. Helps ensure a consistent level of security for all
templates/models in the repository
Conversely, use of a centralized repository places the
responsibility for security and privacy on the enter-
prise. The enterprise must institute policies and pro-
cedures that ensure the integrity and validity of the
data in the repository. If matching is not performed
locally, there is a danger that transmissions may be
intercepted and used for replay attacks. Although
data management for a centralized repository is gener-
ally easier than management of distributed resources,
centralized repositories can become extremely large
and unwieldy.
Matching
The reference template/model and the live biometric
sample obtained from the claimant are compared/
matched with the server. That server may or may not
also house the centralized repository of biometric tem-
plates/models.
Centralized match ing is useful when biometric
input is highly distributed and is a logical option
when the reference templates/models are stored in a
centralized repository. As with centralized storage, cen-
tralized matching assigns control and responsibility to
the enterprise. In particular, transmission of biometric
samples over networks makes them vulnerable to
network-based attacks.
Client/Workstation
A general-purpose workstation, usually a desktop or
laptop PC. PDAs and other mobile devices may be
included even though such use blurs the boundary
between ‘‘client/workstations’’ and ‘‘devices.’’ The cli-
ent is the location/resource where users initiate the
remote authentication process but none of these clients
is a dedicated biometric authentication server even if
they house other resources used for authentication.
Storage
One ore more reference templates/models are stored in a
local repository. That repository may or ma y not be the
same as the client used to acc ess the authentication
service. This appr oach is usef ul when a small number
of users can access specific data or transactions. It
eliminates a central point of attack for intruders
and reduc es the problem of managing an un wieldy re-
pository . Local storage also makes it possible for a system
to operate even when the central network connection is
unavailable.
1122
R
Remote Authentication

On the other hand, there is less control over the
integrity of the data on the local machine. Also, local
storage of templates/models does not suppor t authen-
tication from multiple locations unless there are mul-
tiple copies of templates/models. Management of
multiple copies adds complexity to the system and
could lead to administration and synchronization pro-
blems. For example, it may not be possible for the
administrator to determine whether there are multiple
enrollments for a single individual under the same or
different names. Removal and updating can be more
difficult which could leave sensitive data and systems
vulnerable when, for example, a disaffected employee’s
templates/models are not purged from the entire system.
Matching
The reference template/model and the live biometric
sample obtained from the claimant are compared/
matched on the local workstation. If the reference
template/model is stored in a central repository it
must be downloaded to the local machine. If storage
and matc hing are both performed on the same ma-
chine there is less chance of network-based attacks on
the biometric data but there is the possibility of having
attacks on the reporting of authentication decisions.
Those possibilities arise from potential malware on the
workstation or an attack on the network.
Device/Sensor
It is a biometric input device. It may be part of a larger
peripheral that is attached to a workstation; embedded
in a workstation or other device, (e.g. a keyboard or a
cell phone) or it may be a telephone. If it is a ‘‘dumb’’
device, it does nothing more than capture and transmit
raw or slightly-processed biometric data (e.g., a stan-
dard telephone). If it has more intelligence, it may be
able to store or process data or perform matching.
Storage
Storage on the device provides rapid access if it is a
device the user controls (e.g., a cellphone Vs. a dedicated
biometric sensor) it can give the user control over the
biometric template/model. Depending on the device, it
may be possible to incorporate cryptographic methods
to further secure the stored template/model.
Template/model deletion can be challenging but
could be accomplished by the system administrator as
part of a provisioning process. Performing deletion in
this way requires the devices to be centrally managed
which is easier to accomplish when the input device is a
dedicated biometric sensor unit rather than a cellphone.
Matching
Matching on a biometric sensor involves embedding
biometric technology into the device in a way that
allows it to operate as a stand-alone system. The
matching process is generally fast because there may
be little or no communication with the outside until
the matching process is complete. As a result, network-
based attacks are eliminat ed as a threat.
Physical Token
An object capable of storing a biometric reference
template/model and possibly performing operations
related to authentication, such as encryption, feature
extraction, and even matching. Physical tokens gener-
ally have technology to resist tampering. Typical exam-
ples of physical tokens a re smart cards, PCMCIA cards,
USB memory sticks, and RF tokens.
Storage
Storage of a single user’s reference template/model on a
token gives the user maximum control and privacy
protection. Only the user determines when her or his
token is used and for what purpose. This form of
storage also makes it possible for the token to be used
at multiple locations.
Since the token and enrolled template/model are
both controlled by the user, it is not possible to deter-
mine whether the user has enrolled multiple times
under different identities. This not only makes it diffi-
cult for the enterprise to maintain a definitive list of
users but also proves harder to prevent fraudulence.
Additional costs may come from the need to deploy
the dual-purpose sensors. Each biometric sensor must
not only be able to accept live samples but must also be
capable of reading the stored template/model on the
token. Another common cost factor is replacement of
lost or damaged tokens.
Matching
When both storage and matching are on the token, the
opportunity for network attack is greatly diminished.
There are some vulnerability in the communication
link between the smart card/token and the reader.
Tokens capable of matching are more complex and
more expensive to replace.
Remote Authentication
R
1123
R

Kinds of Applications
The most widely- deployed speaker-authentication
applications requiring remote authentication involve
Data security
Transaction security
Remote moni toring
Access security
at levels of assurance that vary with the sensitivity of
the data and other factors. All four types of applica-
tions of remote authentication exist in real-world
deployments.
Most of the examples provided in this section come
from speaker authentication since it is the modality
that exhibits the broadest spectrum of remote-authen-
tication applications today.
Speaker Authentication
Most remote applications of speaker authentication are
centralized for both storage and matching (althoug h
the aut hentication resources including the application,
biometric engine, and the template/model database)
may not all reside on the same server. When authenti-
cation is hosted, for example, the application that
calls the authentication process may reside within the
enterprise but the biometric engine will be located on
the server of the hosting-services provider. The tem-
plate/models may be stored within the enterprise or by
the hosting company.
Figure 1 shows a typical centralized architecture.
The remote-access channel, represented by the cloud in
Fig. 1, can be a wireless or wireline telephone network,
specialized data network (e.g., ATM), the Internet, or a
combination of those channels. If the authenticat ion is
provided as a Web service, the cloud may include a
Web browser. The assurance levels of these applications
vary with the nature of the secured data, the resources
involved, the users, and other factors.
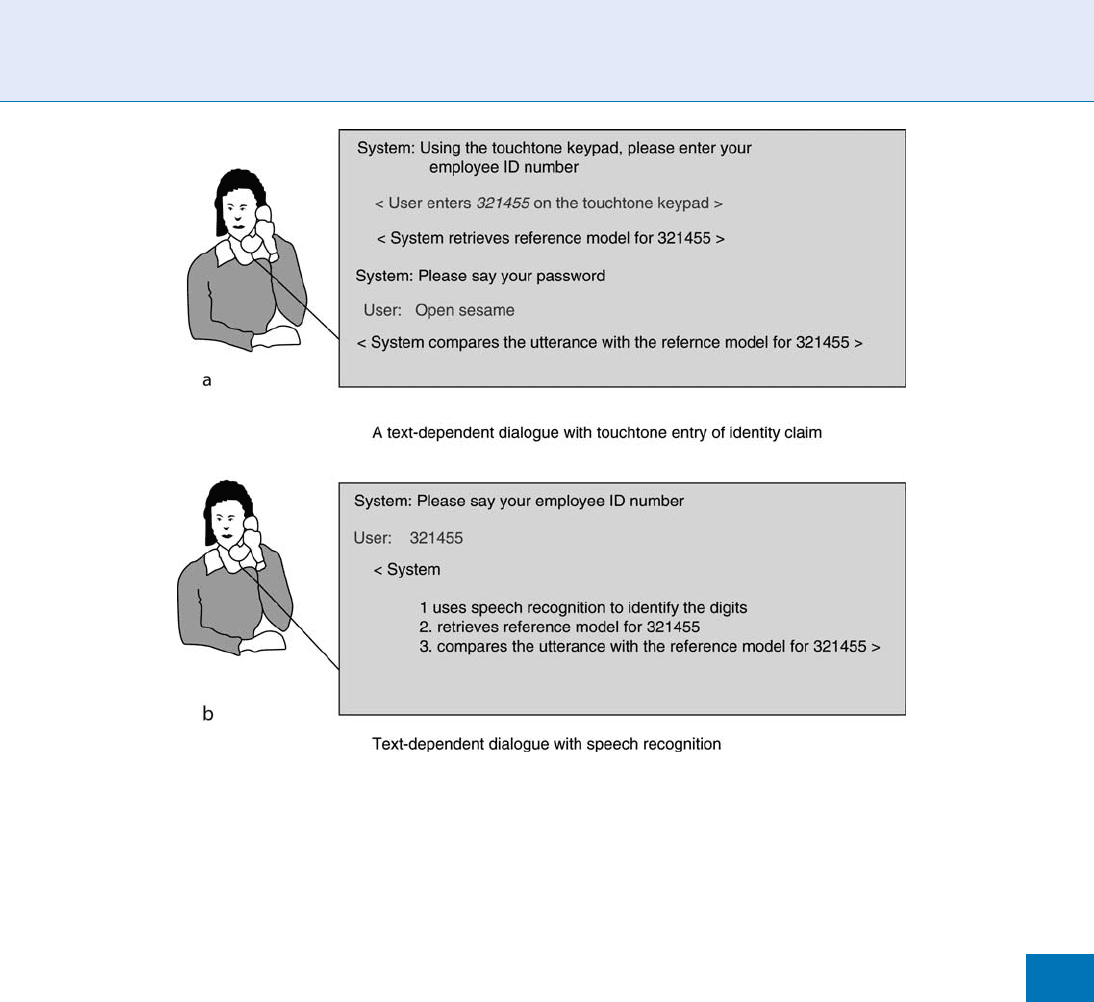
A ty pical deployment using speaker authenti-
cation is shown in Fig. 2. It employs two-factor
authentication that combines password security with
text-dependent, biometric secur ity. The application
consists of a dialogue involving interactive voice re-
sponse (IVR). The IVR system answers the telephone
and prompts the caller for an ID (claim of identity)
and a spoken password (Fig. 2a). In some applications
the system uses the spoken password as both the claim
of identity and password (Fig. 2b). In those applica-
tions,
▶ speech recognition is used to decode the ID
before it is sent to the authentication sub-system for
biometric authen tication.
The examples in Fig. 2 are typical for telephone
banking (e.g., ABN AMRO, Banco Bradesco of Brazil,
Remote Authentication. Figure 1 Typical Centralized Architecture.
1124
R
Remote Authentication
and Israel’s Bank Leumi), account access (e.g., Bell
Canada, Aeroplan, Australian Health Management,
and Ameritrade), automated PIN/password reset
(e.g., by Wells Fargo Bank, The Hartford Insurance,
Swisscom, Morgan Stanley, VISA, AT&T, and Banco
Santander International), and a range of other deploy-
ments, including
Wells Fargo – credit card activation and customer
helpdesk
Bell Canada, CNRail, Telus – secure reporting,
billing, dispatch instructions for field service
personnel
Austar (Australia) – allow club members to order
movies
United States Department of Homeland Security –
telephone check-in and reporting by visa holders
Municipality of Dubai – reports of littering offenses
Union Pacific Railroad – customers report when
their shipments are delivered (called ‘‘railcar release’’)
Prisons – to ensure that inmates a re not abusing
their outbound-calling privileges.
These applications often include a ‘‘gray area’’ for
matching-scores that fall slightly below the acceptance
threshold. Scores that fall within the gray area trigger
additional authentication procedures. Those proce-
dures may include prompting for repetition of the
password, a text-prompted (challenge-response) inter-
action, use of another authentication techn ology, or
transfer to a human.
If a tape attack is suspected, the application may
engage the user in a
▶ text-prompted interaction.
Some deployments challenge the user to say something
that she or he has never said to the system before, such
as the answer to ‘‘What is today’s date?’’
Another approach using centralized architecture
involves remote authentication of an individual call-
ing the enterprise’s call center and spe aking with
a human rather than interacting with an IVR. Most
such deployments are designed to maintain a high level
of authentication secur ity while reducing the time
needed to do the authentication. The agent initiates
a
▶ text-independent session while speaking with a
Remote Authentication. Figure 2 Examples of two-factor authentication using speaker authentication.
Remote Authentication
R
1125
R

caller when, for example , the caller requests a secured
transaction, such as a sizable funds transfer, or sensi-
tive account/customer information. While the system
is running in the background, the agent may also
be asking the caller questions (knowledge-based
authentication). The combination of the factors pro-
duces the needed authentication. Bank Leumi, one
of the largest banks in Israel, has used this approach
for several years.
A method developed by Authentify, an American
solutions provider, is suitable for authentication
levels 3 and 4. It combines out-of- band voice authen-
tication with a Web session. The following variant is
used by VeriSign to authenticate applicants renew-
ing digital certificates. The system sends an email to
the applicant containing a link that in itiates the
authentication Web session. The system calls the tele-
phone num ber provided by the applicant and per-
forms speaker enrollment. The system then uses a
third-party telephone directory to obtain the phone
number for the applicant’s company, calls that num-
ber, and asks to be connected with the applicant.
When the applicant answers, the Web session displays
a randomly-generated sequence on the applicant’s
computer screen and the telephone session asks the
applicant to say that sequence and their name.
Electronic monitoring of community-released and
home-incarcerated offenders utilizes text-prompted
voice authentication. These systems place outbound
calls to registered telephone numbers of locations
where the offender is supposed to be (e.g., home, school,
work, or AA meetings). The calls are placed at random
times during the day and text-prompting is used to
reduce the chance that offenders will use tape recorders.
Challenge response is also used for remote authen-
tication employing other biometric mod alities. This
approach is used for employees, customers using net-
worked devices (e.g., ATMs), and for registered airline
travelers seeking to move quickly through security
lines. Applications that require higher levels of authen-
tication may request more than one fingerprint or
samples for multiple biometric modalities.
Other Biometrics
A growing number of deployments are using smart-
cards with fingerprint, face, iris, or finger/hand
vascular templates embedded in them. This include s
e-passport, national ID, and trusted traveler programs.
Matching is almost always done on the device or
centrally (Fig. 2). One large-scale deployment in pri-
vate industry is by ICICI Prudential Life Insurance
of India. Its smartcard contains a fingerprint as well
as the individual’s policy information. Some biometric
ATMs also use card-based storage.
Related Entries
▶ Biometrics, Overview
▶ Speaker
▶ Speaker Recognition, Standardization
References
1. Bosen, B.: Network Attacks: Analysis of Department of Justice
Prosecutions 1999 – 2006. Pleasanton, CA: Trusted Strategies
Ltd. (2006)
2. Authentication in an Internet Banking Environment (FIL
03–2005). United States Federal Deposit Insurance Corporation
(2004)
3. Guidance on Authentication in an Internet Banking Environ-
ment. United States Federal Financial Institutions Examination
Council (2005)
4. Q&A on Guidance on Authentication in an Internet Banking
Environment. United States Federal Financial Institutions
Examination Council (2006)
5. Health Insurance Portability and Accountability Act of 1996
(Public Law 104 191). United States Department of Health and
Human Services (1996)
6. Telecommunications Carriers’ Use of Customer Proprietary
Network Information and Other Customer Information (FCC
07–22A). Federal Communications Commission (2007)
7. Kuhn, D.R., Hu, V.C., Polk, W.T., Chang, S.-J.: Introduction
to Public Key Technology and the Federal PKI Infrastructure
(SP 800–32). National Institute of Standards and Technology
(2001)
8. Bolton, J.: E-Authentication Guidance for Federal Agencies.
(Memorandum M-04–04, Appendix p. 3) Office of Management
and Budget (OMB) (2003)
9. Burr, W.E., Dodson, D.F., Polk, W.T.: Electronic Authentication
Guideline (SP 800–63 v 1.01.2). National Institute of Standards
and Technology (2006)
10. Tilton, C., Young, M. (eds.): Study Report on Biometrics in
E-Authentication (M1/07–0185). American National Standards
Institute/International Committee for Information Technology
Standards (2007)
1126
R
Remote Authentication

Remote Monitoring (Partial)
▶ Remote Authentication
Remote Verification
▶ Remote Authentication
Rendering
▶ Face Sample Synthesis
Replay Attack
Replay attack is a term used in computer security
where an attacker records a successful authentication
procedure between a legitimate client and a computer
system, or also between two computer systems, and
then replays that recording in order to be falsely
authenticated by the system. In the context of voice
authentication, a replay attack involves a recording –
analogue or digital – of a legitimate client’s voice and
the playing back of that recording to the authentication
system by the attacker in order to be falsely accepted by
the system as the legitimate client.
▶ Biometric Secutiry, Standardization
▶ Biometric Spoof Prevention
▶ Biometric System Design, Overview
▶ Liveness Assurance in Face Authentication
▶ Liveness Assurance in Voice Authentication
▶ Remote Authentication
▶ Security Issues, System Design
▶ Synthesis Attack
▶ Tamper-proof Operati ng System
Residence Time
The length of time a subject must reside in the capture
volume of a biometric capture dev ice to ensure that the
device captures a good quality image.
▶ Iris Device
▶ Iris on the Move™
Resolution
In image analysis, a measure of the ability of a system
to distinguish two features that are close together – to
recognize that there are two features rather than one.
In image displays, a measure of the a bility of a system
to present two features that are close together as dis-
tinct features rather than a single feature. In digita l
images and digital image processing, resolution is
often described in terms of the number of pixels in
the image or the number of pixels/unit length.
▶ Iris Device
▶ Photography for Face Image Data
Response Time
The time required by a biometric system to return a
decision on identification or verification of a presented
biometric sample. Response time includes the time for
collecting data, extracting features, and matching
against the enrolled biometric templates.
▶ Performance Evaluation, Overview
Response Time
R
1127
R
Retina
The retina is the multilayered sensory tissue of the
posterior eyeball onto which light entering the eye is
focused, forming a reversed and inverted image. It
contains photosensitive receptor cells, the rods and
cones, which are capable of converting light into
nerve impulses that are conducted and further relayed
to the brain via the optic nerve. There are about 110 to
125 million rods and 6.3 to 6.8 million cones in each
human retina.
▶ Anatomy of Eyes
▶ Iris Image Data Interchange Formats, Standardization
Retina Recognition
YOICHI SETO
Advanced Institute of Industrial Technology, Tokyo
Metropolitan University, Tokyo, Japan
Synonyms
Retinal scan; Vein Recognition; Vascular Recognition;
Ocular biometrics
Definition
Retina recognition is a biometric technique that uses
the unique patterns on a person’s retina for person
identification. The retina is the layer of blood vessels
situated at the back of an eye. The eye is positioned in
front of the system at a capture distance ranging from
8 cm to one meter. The person must look at a series of
markers, viewed through the eyepiece, and line them
up. The eye is op tically focused for the scanner to
capture the retina pattern. The retina is scanned with
the near infrared (NIR 890 nm) irradiation and the
unique pattern of the blood vessels is captured. Retina
recognition makes use of the individuality of the
patterns of the blood vessels. It has been developed
commercially since the mid-1970s. Sandia Laboratory
reported a false rejection rate of lower than 1.0%.
Introduction
The idea for retinal identification was first conceived
by Dr. Carleton Simon and Dr. Isodore Goldstein and
was published in the New York State Journal of Medi-
cine in 1935, which while studying eye disease, made a
study that every eye has its own totally unique pattern
of blood vessels [1]. They subsequently published a
paper on the use of retinal photographs for identifying
people based on blood vessel patterns.
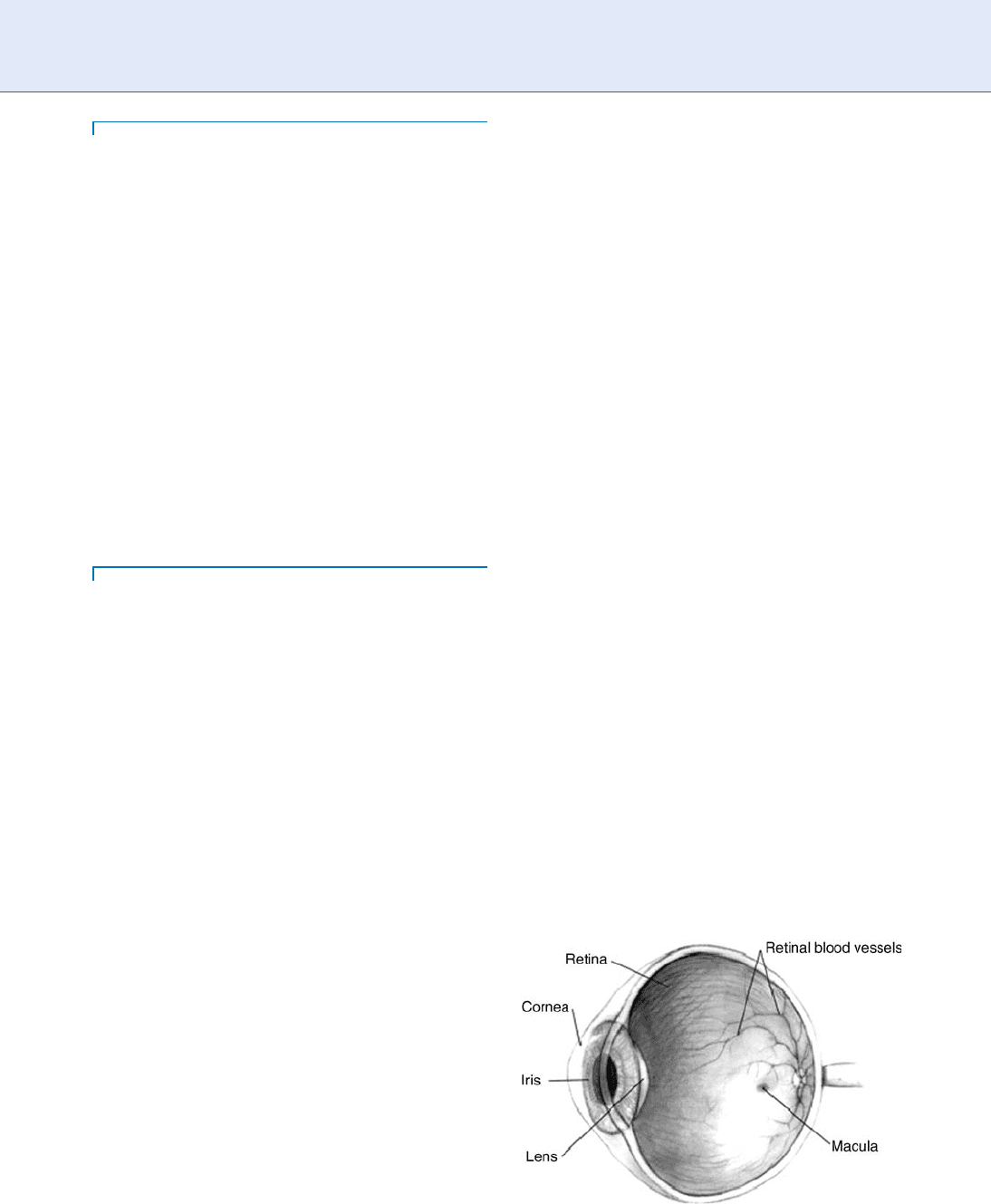
Referring to Fig. 1, the retina is to the eye as film is
to the camera. Both detect incident light in the form of
an image that is focused by a lens. The amount of light
reaching the retina is a function of the iris. The retina is
located on the back inside of the eyeball. Blood reaches
the retina through vessels that come from the optic
nerve. Just behind the retina there is a matting of
vessels called the choroidal vasculature.
The retina is essentially transparent to the wave-
length of light. The mat of vessels of the choroids just
behind the retina reflects most of the useful informa-
tion used to identify individuals [2, 3].
A retinal scan is used to map the unique patterns of
a per son’s retina. The blood vessels within the retina
absorb light more readily than the surrounding tissue
and are easily identified with appropriate lighting.
A retinal scan is performed by casting an undetectable
ray of low-energy infrared light into a person’s eye as
they look through the scanner’s eyepiece. This beam of
light outlines a circular path on the retina. Because
retinal blood vessels are more sensitive to light than
the rest of the eye, the amount of reflection fluctuates.
Retina Recognition. Figure 1 Schematic representation
of ball of the eye. Refer from Wikipedia.
1128
R
Retina

The results of the scan are converted to a computer
code and stored in a database.
Processing
The process of enrollment and verification/identi-
fication in a retinal scanning system is the same as
the process for the other biometric technologies,
which are (1) Acquisition and preprocessing of images,
(2) Feature extraction, (3) Template data creation and
(4) Matching processing [4].
Image Acquisition and Preprocessing
Illumination was provided by a narrowband near-
infrared (NIR) LED. This wavelength selection was
made for several reasons. Near-infrared light was not
distracting to the subject and caused no v isual discom-
fort. Additionally, it is important to choose wave-
lengths that give the best blood vessel contrast. The
oxy-hemoglobin and reduction-hemoglobin can be
found in the veins and arteries adequately absorb in
the NIR. However, there are tradeoffs that one must
consider when choosing NIR. A reduction-hemoglo-
bin strongly absorbs the NIR irradiation energy, and
then the part of vein pattern becomes dark.
The user must first place their eye onto a lens located
in the retinal scanning device at an extremely close range.
It is very important that the user must remain perfectly
still at this point, in order to insure that a robust image
will be captured. Also, the user must remove any eye-
glasses that he or she might be wearing, because any light
reflection from the lens of the eyeglasses could cause
interface with the signal of the retinal scanning device.
Once the user is situated comfortably, he or she then will
notice a green light embedded against a white back-
ground through the lens of the scanning device. Once
the retina scanning device is activated, this green light
moves in a complete circle (360 degrees) and captures
images of the blood vessel pattern of the retina through
the pupil. At this phase, normally three to five images are
captured. Also, this phase can take over 1 minute to
complete, depending upon how cooperative the user is.
This is considered to be a very long time in comparison
to the image acquisition and processing times of the
other biometric technologies.
The first encoding step was the identification of
blood vessels within each image. Blood vessels were
separated from distracters such as choroidal texture.
The location and path of the retinal blood vessels were
then quantitatively described. Sections of blood vessels
were segme nted and linked together. The identified
blood vessel structure was then reduced to an efficient
encoding template. Retina matching involves defining
a similarity score between encoded blood vessel pat-
terns. The encoding and final calculati on of this simi-
larity score must take into account the differences
between the two source images.
Feature Extraction
A very strong advantage of retina recognition is that
genetic factors do not dictate what the blood vessel
pattern of the retina will be. This allows the retina to
have very rich, unique features. As a result, it is possible
that up to 400 uni que data points can be obtained from
the retina as opposed to other biometrics, such as
fingerprint scanning, where only 30–40 data points
(the minutiae) are available.
Template Data Creation
The unique features gathered from the blood vessel
pattern of the retina forms the basis of the enrollment
template, which is only 96 bytes, and as a result, is
considered to be one of the smallest biometric templates.
Matching
The retinal matching involves defining a similarity
score between encoded blood vessel patterns. The
encoding and final calculation of this similarity score
must take into account the differences between the two
sources of images which is the same as the process for
the other biometric technologies.
Sandia Laboratory has tested the retina recognition
product of EyeDentify. The false rejection rate with
databases of several hundred individual eyes is
reported to be lower than 1.0% [3, 4].
Related Entries
▶ Back-of-hand Vein recognition
▶ Finger Vein recognition
Retina Recognition
R
1129
R
