Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.


by Bolle et al. [2] when it was observed that the empir-
ical false reject rate (FRR) was significantly better than
predicted by their theoretical model. This fact implied
that the bits of an iris code are not equally susceptible
to ‘‘flip’’, given different environmental conditions that
affect the quality of the captured iris images. Hollings-
worth et al. demonstrated that by eliminating (mask-
ing) inconsistent bits, one could dramatically improve
the FRR of an iris template.
Although the work of Hollingsworth et al. improves
the FRR by identifying and removing fragile bits, our
preliminar y results show that it may be possible, based
on bit instability, to further reduce the number of iris
code bits needed for recognition. Our results show that
this can also be done without an increase in the false
accept rate (FAR). By using GRIT (Genetically Refined
Iris Templates), iris code templates can be refined and
transformed into templates that use a significantly
smaller number of iris code bits for iris recognition.
GRIT is a system that uses the concepts of bit inconsis-
tency [1] and simulated evolution [3–6] in an effort to
evolve iris code templates that use fewer iris code bits.
Bit Inconsistency
In [1], Hollingsworth et al. selected a dataset of 1251
images that were mostly unoccluded by eyelids or
lashes. If an individual iris code bit was mostly one
particular bit value and ‘‘flipped’’ to the other bit value
some threshold percentage of the time, the bit was
considered fragile (inconsistent). For their analysis, a
bit was considered fragile if it flipped more than 40%
of the time. The ir results indicated that on average,
15% of the bits had probability greater than 40% of
flipping and 85% of the bits had probability less than
40% of flipping. The implication of these rates indi-
cates that the FRR of systems using Daugman-style [7]
iris recognition system s could be dramatically reduced
by focusing only on consistent bits. With this modified
strategy, iris images would be analyzed to create an iris
template that would mask out inconsistent bits. This
mask would be combined with the typical masks used
to eliminate eyelids and eyelashes.
Genetically Refined Iris Templates
(GRIT)
GRIT is a system for evolving iris tem plates that have a
decreased FRR; use a smaller number of iris code bits;
and do not have an increased FAR. GRIT is composed
of two components: a preprocessor and a Geneti c
Algorithm (GA) [3–6]. The GRIT preprocessor uses
the concept of bit instability to eliminate fragile bits as
well as develop a probability distribution function to
be used by the GA to further reduce the number of iris
code bits needed for recognition. GAs belong to a class
of search techniques based on simulated evolution [5]
and have been successfully used to solve a wide range
of complex real-world search, optimization, and
machine-learning problems.
The GRIT Preprocessor
In order to describe the GRIT preprocessor, let I ={i
0
,
i
1
, ..., i
n1
} and M ={m
0
, m
1
, ..., m
n1
} be sets of iris
codes along with their associated bit masks. The pre-
processor, as shown in Fig. 1, works as follows. Given a
set of iris codes a nd masks it sets i to the first iris code,
i
0
, in the set of iris codes and m to the associated mask
of i
0
, m
0
. Next a hyper iris code and a hyper mask are
created. The hyper iris code, v, simply records the
number of iris codes in I that have the same value for
each corresponding bit in i. The hyper mask, w,
records the number of iris codes in I (along with
their masks in M) that used a particular mask bit
(associated with the best offset resulting in the best
hamming ratio [7]) when comparing those iris codes
with i, given m.
Given v and w, the relative worth of flipping a bit in
i can be computed. The hyper gain, g, represents the
number of iris codes in I that i will become closer to
Iris Template Extraction Via Bit Inconsistency and GRIT.
Figure 1 The GRIT Preprocessor.
860
I
Iris Template Extraction Via Bit Inconsistency and GRIT

(with respect to hamming ratio) by flipping a par ticu-
lar bit. Those bits in i that have an associated positive
gain can be flipped, because they will make the result-
ing iris template, i
0
, closer to a greater number of iris
codes in I. Those bits in i that have an associated gain
of zero represent bits that have a 50% inconsistency
rate, and therefore, can be ‘‘turned off
0
’’ (or masked)
by setting the associated bit in m to zero. The GRIT
preprocessor returns a modified iris code, i
0
, and mask,
m
0
, that has a lower FRR w ith respect to I than the iris
template consisting of i and m. The hyper gain, g, is also
returned and used as a probability distribution func-
tion (heuristic) to guide the mutation operator of the
GRIT genetic search method. Figure 1 provides a pseu-
do-code example of the GRIT preprocessor.
The GRIT GA
The GRIT GA takes as input i
0
, m
0
,g,I,M,andd,
where d represents the number of bits to mutate in
creating an offspring template. The GRIT GA begins
by creating P-1 mutants of m
0
, where P represents the
population size of the GA. These mutants along with i
0
make up the initial population of candidate bit masks.
In creating the initial population, each of the mutants
is created by mutating 100d bits of m
0
as follows. Two
bit positions are select ed at random and their asso-
ciated gains (using g) are compared. The bit that has
the highes t gain is then mutated (flipped). This is how
the Mutate method of the GRIT GA operates.
Each candidate bit mask in the initial population is
evaluated using the following evaluation function:
Fði
0
; c
mask
; I; M; tÞ¼
X
j
bði
0
; c
mask
; i
j
; m
j
; tÞ
þ Rði
0
; c
mask
; I; M; t Þ;
where c
mask
represents a candidate mask,
bði
0
; c
mask
; i
j
; m
j
; tÞ represents the number of iris code
bits used in the comparison between the candidate
iris template and the jth iris code in I, and
Rði
0
; c
mask
; I; M; t Þ represents the penalty if any of the
iris codes in I is rejected by the template, (i
0
, c
mask
), by
have a hamming ratio greater than a user-specified
threshold, t. The penalty is simply the summation of
the amount by which the rejected iris codes exceed the
threshold plus a constant value, a.
After each candidate mask has been evaluated and
assigned a fitness by the evaluation function F, the
counter, t, is set to |P| and the GA begins its evolution-
ary process. When the user-specified number of iris
template evaluations has not been reached, the GA
creates an offspring iris template mask by (1) selecting
two individuals from the current population as par-
ents; (2) crossing over [8] the parents to form an
‘‘embryo’’ by taking 50% of the bits from one parent
and 50% of the bits from the other parent; and
(3) mu tating the ‘‘embryo’’. The offspring is then eval-
uated and replaces the worst-fit individual in the pop-
ulation (regardless of whether the worst-fit indiv idual
has a better fitness than the offspring). This process is
repeated until the user-specified number of evaluations
(Max_Evaluations) has been met. After the evolution-
ary process, the iris template with the lowest fitness in
the population is then returned as the best solution
evolved by the GA. Figure 2 provides a pseudo-code
version of the GRIT GA.
The parent selection method works as follows:
(1) randomly select two individuals from the popula-
tion (excluding the worst-fit individual) and return the
individual with the lower fitness as the first parent
(mom); (2) repeat this process to get a second parent
(dad). This parent selection method is commonly re-
ferred to as tournament selection [5].
Preliminary Results
For this work, the iris images were segmented using the
algorithm proposed by Thornton et al. [9], which finds
Iris Template Extraction Via Bit Inconsistency and GRIT.
Figure 2 GRIT (Genetically Refined Iris
Templates).
Iris Template Extraction Via Bit Inconsistency and GRIT
I
861
I
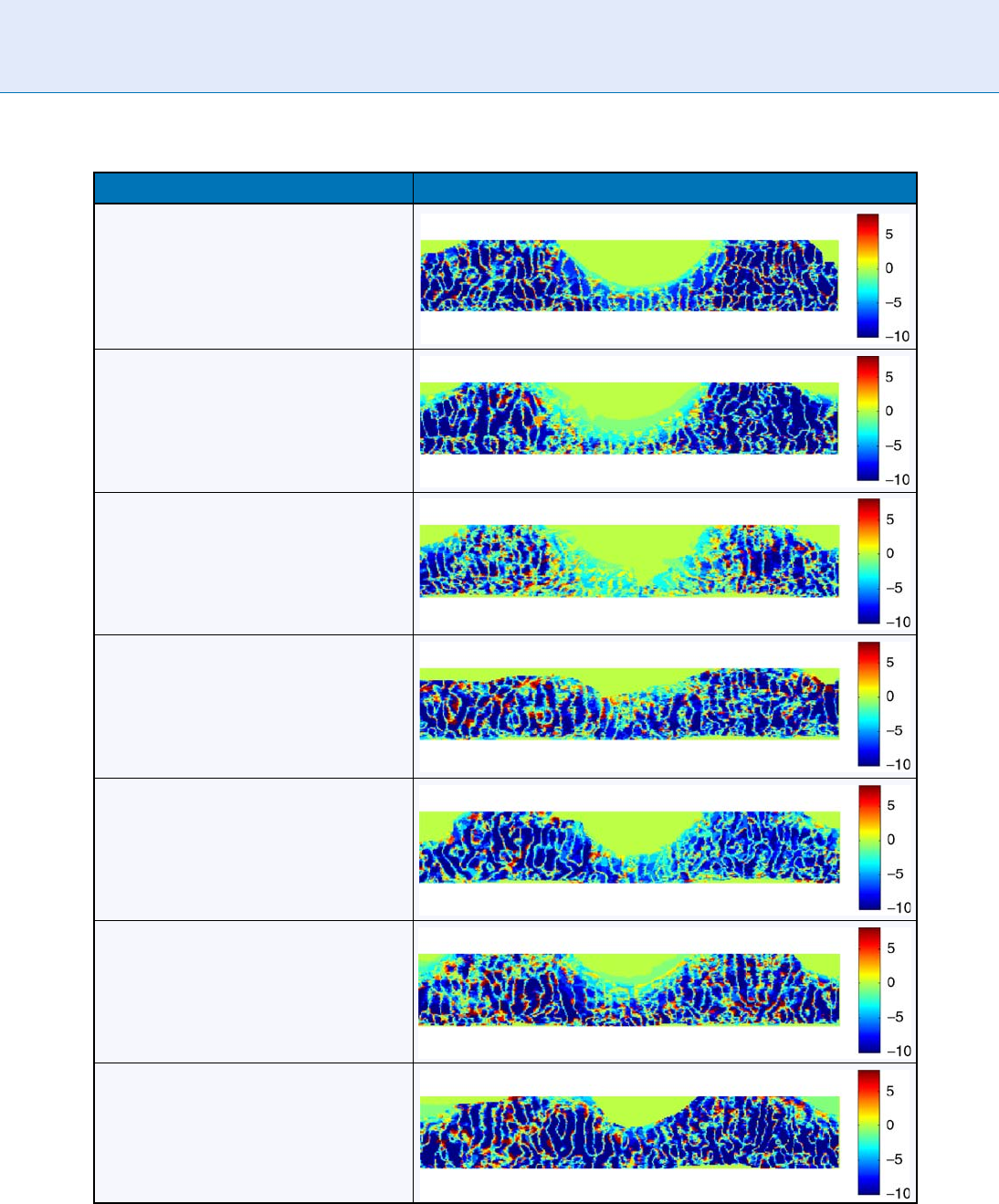
Iris Template Extraction Via Bit Inconsistency and GRIT. Table 1 The Hyper Gains of Subjects Before Revising the
Templates
Subject Hyper Gain
4
5
38
51
67
75
93
862
I
Iris Template Extraction Via Bit Inconsistency and GRIT

nonconcentric circles for both pupil and iris bound-
aries with high accuracy. Eyelids and eyelashes were
manually segmented. Given the iris images with occlu-
sion masks, iris codes are generated by convolving
them with a one-dimensional log Gabor filter row by
row. As in the Daugman’s algorithm [7, 10], the phase
information at each pixel is quantized into two bits,
and then Hamming distances are calculated by com-
paring these bits.
GRIT was used to develop iris templates for a total
of seven subjects taken from the ICE 2006 dataset [11]:
4, 5, 38, 51, 67, 75, and 93. For these subjects, the first
10 iris codes in their respective sets were used to
develop an iris template. The other 20 iris codes were
used as a FRR test set. Each resulting iris template was
checked with all of the other instances of the ICE 2006
dataset to determine its FAR.
The GRIT GA used a population size of 20 candi-
date bit masks and evolved an additional 4820 while
keeping the best 19 candidate bit masks ever found at
all times. The value of d, the number of bits to mutate
in creating an offspring, was set to 100, and the penalty
Iris Template Extraction Via Bit Inconsistency and GRIT. Table 2 The Hyper Gains of Subjects After Revising the
Templates
Subject Hyper Gain
4
5
38
51
67
75
93
Iris Template Extraction Via Bit Inconsistency and GRIT
I
863
I
constant, a, used in the penalty function, R, was set to
43,920, because the dimensions of the iris codes and
masks used were 613602 bits.
Table 1 presents the hyper gains developed by the
GRIT preprocessor for each of the seven subjects.
In Table 1, for each visualization, the values associated
with higher magnitudes (farthest away from zero) are
more consistent (less fragile) than those bits with lower
magnitudes. The red areas of a given subject represent
the bits of the initial iris code template that were
flipped in an effor t to reduce the FRR of the 10 training
instances. The green areas in the hyper gains represent
those bits of the iris code mask that have been removed
(‘‘turned off’’). The larger solid green regions that
appear at the top of each of the hyper gains in Table 1
represent the initial masked bits. Table 2 presents the
hyper gains after the iris template, (im), has been
revised to form ( i
0
m
0
). Notice that the visualizations
show that there are a number of bits w ith hyper gain
values close to zero that may be removed.
In Table 3, a comparison of the original masks, the
masks developed by the GRIT preprocessor, and the
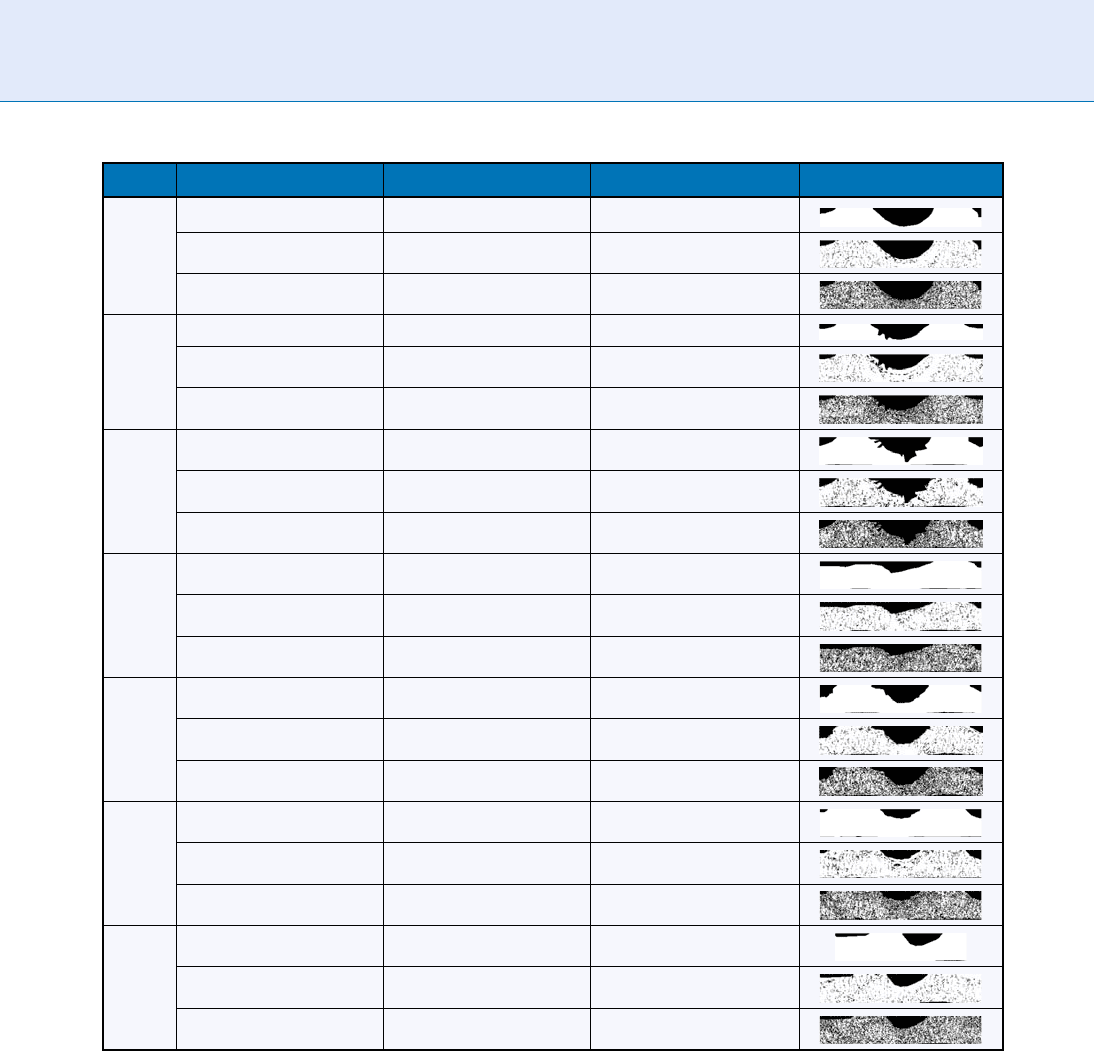
Iris Template Extraction Via Bit Inconsistency and GRIT. Table 3 Preliminary GRIT Results
Subject Mask Type FRR Bits Used Visualized Masks
4 Original 0.0 (0.07) 31196
GRIT-PP 0.0 (0.07) 30545
GRIT-GA 0.0 (0.03) 20382
5 Original 0.0 (0.00) 32250
GRIT-PP 0.0 (0.00) 31635
GRIT-GA 0.0 (0.00) 21200
38 Original 0.6 (0.67) 30371
GRIT-PP 0.0 (0.00) 29667
GRIT-GA 0.0 (0.00) 19173
51 Original 0.2 (0.13) 31456
GRIT-PP 0.0 (0.00) 30743
GRIT-GA 0.0 (0.00) 20169
67 Original 0.1 (0.03) 31206
GRIT-PP 0.0 (0.00) 30455
GRIT-GA 0.0 (0.00) 19766
75 Original 0.4 (0.37) 32724
GRIT-PP 0.0 (0.03) 31831
GRIT-GA 0.0 (0.03) 21759
93 Original 0.0 (0.07) 33070
GRIT-PP 0.0 (0.00) 32365
GRIT-GA 0.0 (0.00) 21728
864
I
Iris Template Extraction Via Bit Inconsistency and GRIT

masks evolved by the GRIT GA are compared for each of
the seven subjects. For each of the masks, the FRR on the
training set of 10 instances is presented. For each of the
masks, the number in parenthesis represents the FRR of
the templates, compared with the 30 instances of I. In the
next column, the average number of bits used in the
comparisons with instances in the ICE dataset is pre-
sented. The final column in Table 3 shows a visualiza-
tion of the original mask, the modifie d mask developed
by the GRIT preprocessor, and the mask evolved by the
GRIT GA. The FARs for all of the templates were zero.
In Table 3, notice that except for Subjects 4 and 75,
the GRIT preprocessor was able to develop a modified
iris code template and mask that reduced the FRR
to zero. For Subject 4, the GRIT GA was able to reduce
the FRR on the test set. This suggests that long runs
of the GA may reduce the test set FRR further.
Also, notice in Table 3 that the GRIT preproc essor is
able to reduce the number of iris code bits needed to be
used for recognition; however, the GRIT GA is able to
reduce this number even further. The resulting iris codes
bits needed are reduced by approximately 30% for each of
the seven subjects.
Summary
In this article, GRIT, a novel approach toward devel-
oping iris templates, has been described. GRIT uses the
concepts of bit inconsistency and genetic search to
evolve iris templates that use a reduced number of
iris code bits for iris recognition. The preliminary
results show that the combination of bit inconsistency
and genetic search provides a powerful hybrid for
developing iris templates. Our results show that the
reduction in the iris code bits needed does not result in
an increase in FRR and FAR.
References
1. Hollingsworth, K., Bowyer, K., Flynn, P.: All iris code bits are not
created equal. In: 2007 IEEE Conference on Biometrics: Theory,
Applications, and Systems, September (2007)
2. Bolle, R.M., Pankanti, S., Connell, J.H., Ratha, N.: Iris individu-
ality: A partial iris model. In: Proceedings of the 17th Interna-
tional Conference on Pattern Recognition, vol. 2, pp. 927–930
(2004)
3. Davis, L.: Handbook of Genetic Algorithms. New York, Van
Nostrand Reinhold (1991)
4. Dozier, G., Homaifar, A., Tunstel, E., Battle, D.: An Introduction
to Evolutionary Computation (Chapter 17). In: Zilouchian, A.,
Jamshidi, M. (eds.) Intelligent Control Systems Using Soft Com-
puting Methodologies, pp. 365–380. Boca Raton, FL, CRC press
(2001)
5. Fogel, D.B.: Evolutionary computation: Toward a new philoso-
phy of machine intelligence, 2nd edn. Las Alomitas, IEEE Press
(2000)
6. Goldberg, D.E.: Genetic Algorithms in Search, Optimization &
Machine Learning. Addison-Wesley Publishing Company, Inc.,
Reading, Massachusetts (1989)
7. Daugman, J.: How iris recognition works. IEEE Trans. Circ. Syst.
Video Technol. 14(1), 21–30 (2004)
8. Syswerda, G.: Uniform Crossover in Genetic Algorithms. In:
David S. (eds.) Proceedings of the Third International Confer-
ence on Genetic Algorithms (ICGA-89), pp. 2–9. San Francisco,
CA, Morgan Kaufmann (1989)
9. Thornton, S.M., Kumar, V.: Robust iris recognition using advanced
correlation techniques. Proceedings of the International Confer-
ence On Image Analysis and Recognition, pp. 1098–1105 (2005)
10. Daugman, J.: High confidence visual recognition of persons by a
test of statistical independence. IEEE Trans. Pattern Anal.
15(11), 1148–1161 (1993)
11. Iris Challenge Evaluation. National Institute of Standards and
Technology, http://iris.nist.gov/ICE/, (2006)
Iris Template Protection
PATRIZIO CAMPISI,EMANUELE MAIORANA,
A
LESSANDRO NER I
University of Roma TRE, Rome, Italy
Synonym
Iris template security
Definition
▶ Template protection is a crucial requirement when
designing a biometric based authentication system. It
refers to techniques used to make the stored template
unaccessible to unauthorized users. From a template,
information about the user can be revealed. Moreover,
identity theft can occur. Therefore, it is of dramatic
importance, if a template is compromised, to cancel,
to revoke, or to renew it. Template protection can be
performed using
▶ template distortion techniques,
Iris Template Protection
I
865
I

▶ biometric cryptosystems, and ▶ data hiding techni-
ques. Template protection techniques specifically
designed and applied to
▶ iris images are hereafter
summarized.
Introduction
Template protection is a key issue that has to be
addressed when a biometric based authentication sys-
tem is designed. It is highly desirable to keep secret a
template both for security and for privacy reasons, and
in case a template is compromised it is necessary to
revoke, to cancel, or to renew it. Also, it is highly
recommended to obtain from the same biometric dif-
ferent templates in order to avoid unauth orized track-
ing across different databases. In the recent past several
techniques have been proposed to secure biometric
templates and to provide the desirable cancelability
and renewability properties. In the following limi-
tations of classical cryptography, when applied within
the biometric framework, are highlighted. Moreover,
recently introduced techniques like template distor-
tions, biometric cryptosystems, and data hiding tech-
niques are briefly discussed first in general and later
with specific application to iris template protection.
Cryptography [1] allows secure transmission of
data over a reliable but insecure channel. The privacy
of the message and its integrity are ensured, and the
authenticity of the sender is guaranteed. However,
cryptographic systems rely on the use of keys which
must be stored and released on a password based
authentication protocol. Therefore, the security of a
cryptographic system relies on how robust is the pass-
word storage system to brute force attacks. However,
template encryption cannot solve the biometric tem-
plate protection problem. In fact, at the aut hentication
stage, when a genuine biometrics is presented to the
system, the match must be performed in the template
domain, after decryption. However, this implies that
there is no more security on the biometric templates.
The match in the encrypted domain could solve this
problem. However, because of the intrinsic noisy na-
ture of biometric data, the match in the encrypted
domain would inevitably bring to a failure because
small differences between data would bring to sig-
nificant differences between their encrypted versions.
Some activities are flourishing to define signal
processing operations in the encrypted domain,
which could allow, for example, to perform operations
on encrypted biometric templates on not trusted
machines. However, this activity is still in its infancy
and does not provide tools within the biometric frame-
work yet.
Among the possible approaches recently proposed
to address the issue of template protection, techniques
based on intentional template distortions on the origi-
nal biometrics have been introduced in [ 2]. Specifical-
ly, the distortion can take place either in the biometric
domain, that is, before feature extraction or in the
feature domain. Moroever, the distor tion can be per-
formed using either an invertible or a non invertible
transform on the base of a user key which must be
known at the authentication stage . On ly the distorted
data are stored in the database. This implies that, even
if the database is compromised, the biometric data
cannot be retrieved unless, when dealing with invert-
ible transforms, user dependent keys are revealed.
Moreover, different templates can be generated from
the same original data, simply by changing the para-
meters of the employed transforms. The described
technique allows obtaining both cancelability and
renewability.
In the recent past, some efforts have been devoted
to design biometric cryptosystems (see [3] for a review)
where a classical password based authentication ap-
proach is replaced by biometric based authentica-
tion. Biometric cryptosystems can be used for either
securing the keys obtained when using traditional
cryptographic schemes or for providing the whole
authentication system. A possible classification of the
operating modes of a biometric cryptosystem is given
in [3] where key release, key binding,andkey generation
modes are identified. Specifically, in the key release
mode the crypto graphic key is stored together with
the biometric template and the other necessary infor-
mation about the user. After a successful biome tric
matching, the key is releas ed. However, this approach
has several drawbacks, since it requires access to the
stored template and then the one bit output of the
biometric matcher can be overridden by using Trojan
horse attacks. In the key binding mode the key is bound
to the biometric template in such a way that both of
them are inaccessible to an attacker and the key is
released when a valid biometric is presented. It is
worth pointing out that no match between the tem-
plates nee ds to be performed. Among the key binding
approaches it is worth citing the fuzzy commitment
866
I
Iris Template Protection

and the fuzzy vault scheme. In the key generation mode
the key is obtained from the biometric data and no
other user intervention besides the donation of the
required biometrics is needed. Both the key binding
and the key generation modes are more secure than
the key release mode . However, they are more difficult
to implement because of the variability of the biomet-
ric data.
Data hiding techniques [4] complement encryp-
tion. In fact, encryption can be applied to ensure
privacy, to protect the integrity, and to authenticate a
biometric template. However, among the possible
drawbacks, encryption does not provide any protec-
tion once the content is decrypted. On the other hand,
data hiding techniques can be used to insert additional
information, namely the watermark, into a digital ob-
ject. Within the biomet ric fram ework, data hiding can
be applied for copy protection, fingerprinting, data
authentication, and timestamping in such a way that
after the expiration date the template is useless. It is
worth pointing out that some security requirements
are also needed when dealing with data hiding techni-
ques. In fact, according to the application, we should
be able to face unauthorized embedding, unauthorized
extraction, and unauthorized removal of the watermark.
Recently some efforts are being devoted to the integra-
tion between watermarking and cryptography. Howev-
er, much more research activity is still needed before
deployment. In the following, after a quick overview
on iris template generation, the most significant
approaches for iris template protection are discribed.
Iris Template Generation
An iris image is preprocessed to select the actual iris
region to use for feature extraction, thus removing
unwanted elements such as eyelid, eyelashes, pupil,
reflections, and all the other noise components. Then
an iris normalization process takes place, since the
extracted iris regions, both from different people and
from the same people, can differ because illumi nation
changes, variation of the eye-camera dista nce, elastic
deformations in the iris texture, and similar. These
effects can generate matching problems. In some
approaches a scale-invariant transform like the Four-
ier-Mellin is used. In some others, a mapping of the iris
image from raw cartesian coordinates to non concen-
tric polar coordinate system is used. After the normali-
zation stage, the features extraction procedure takes
place. This task can be accomplished using different
approaches such as multi-scale Gabor wavelet filtering
and its variants, singular value decomposition, principal
component analysis, and so on.
Cancelable Iris Template
A cancelable iris biometric approach, namely S-Iris
Encoding, is proposed in [5]. The method is roughly
sketched in Fig. 1 and briefly summarized in the fol-
lowing. Iris preprocessing is performed first. Specifi-
cally iris segmentation by means of the Canny edge
detector, to find the edge map, followed by the Circular
Hough Transform, to detect the iris and pupils bound-
aries are carried out. Linear Hough transform is used
to discard eyelids and eyelashes. The normalization is
performed using the Daugman’s rubber sheet model
[6]. The iris feature extraction is performed by con-
volving the normalized 2D pattern rows, each
corresponding to a circular ring of the iris region, by
using 1D Log-Gabor filter. The magnitude of the so
obtained complex features are then collected in a vec-
tor
w that is further processed to obtain the S-Iris code
Iris Template Protection. Figure 1 S-Iris Encoding scheme [5].
Iris Template Protection
I
867
I
as described in the next steps. A set of m orthonormal
pseudorandom vectors f
r
?;i
g, with i ¼ 1; 2; ; m, are
then generated using a token. The inner products
a
i
¼ <w; r
?;i
>, with i ¼ 1; 2; ; m, are then evalu-
ated. The m bits of the S-Iris code
s ¼fs
i
j i ¼ 1; ; mg are computed as
s
i
¼
0ifa
i
< m
i
s
i
; a
i
> m
i
þ s
i
1ifm
i
s
i
a
i
m
i
þ s
i
;
where m
i
and s
i
are the average and standard deviation
of a
i
respectively. This approach allows to discard those
inner products which are numerically small and which
therefore must be excluded in order to improve the
verification rate. The authors of [5] point out that the
system authentication performance have a significant
improvement over the solely biometric system.
Iris Template Protection using
Cryptosystems
Among the methods which can be classified as key
binding based approaches [3] we can cite the fuzzy
commitment scheme [7], based on the use of error
correction codes and the fuzzy vault scheme [8],
based on polynom ial based secret sharing .
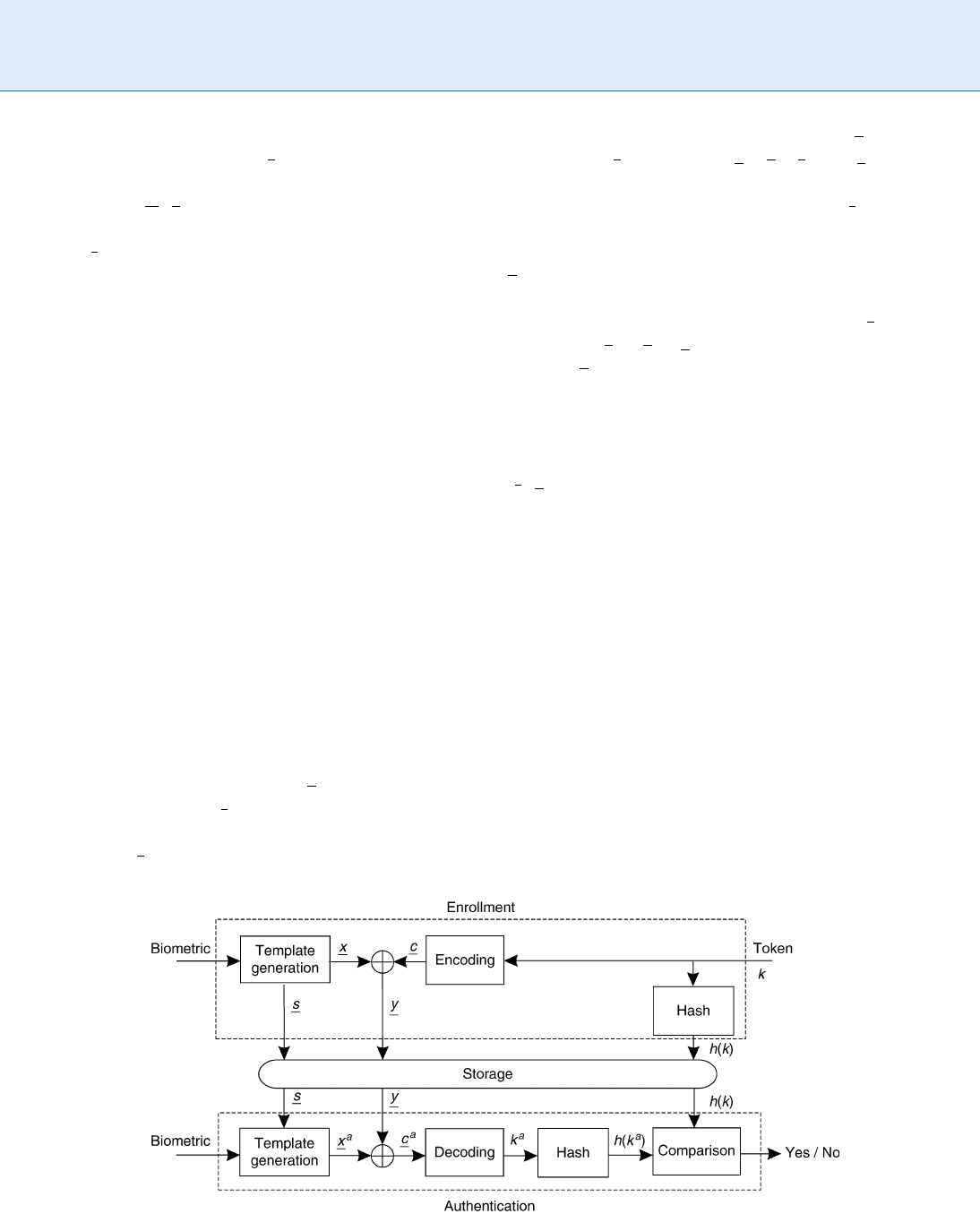
Specifically, the fuzzy commitment scheme is
depicted in Fig. 2 in its general form. In the enrollment
stage, the biometric template
x is used to derive some
side information
s which is stored to be used in the
authentication stage. Then a randomly chosen code-
word
c is gen erated on the base of a token k. The
binding between the biometric meas urement
x and
the codeword
c is obtained as y ¼ x c. Both y and
a hashed version of the token k are eventually stored. In
the authentication stage, the side information
s is re-
trieved and, together with the actual biometric mea-
surement, it is used to obtain the biometric templa te
x
a
. This latter usually differs from the template
obtained in the enrollment stage because of the intrin-
sic variability of biometrics. Then the codeword
c
a
is
obtained as
c
a
¼ x
a
y. Finally k
a
is obtained by
decoding
x
a
. Its hashed version hðk
a
Þ is obtained and
compared with the stored hðkÞ. If the obtained values
are identical, the authentication is successful. It is
worth pointing out that this scheme provides both
template protection, since from the stored information
ð
s; y; hðkÞÞ it is not possible to retrieve the template,
and template renewability, since by changing the token
k the template representation changes.
In [9] the fuzzy commitment scheme here de-
scribed is applied to iris protection. Iris preprocessing
consists in the edge map extraction followed by Circu-
lar Hough Transform to detect the iris and pupils
boundaries followed by Linear Hough transform to
discard eyelids and eyelashes. The normalization is
performed using the Daugman’s rubber sheet model.
The iris feature extraction is performed by convolving
the rows of the normalized 2D pattern by using 1D
Log-Gabor filter. The phase information from both
the real and the imaginary part is eventually quantized.
A reliable bits selection is then performed according
to the assumption that the more reliable bits are those
coming from the pixels closer to the pupil center,
Iris Template Protection. Figure 2 Fuzzy Commitment scheme.
868
I
Iris Template Protection

where eyelid and eyelashes are not likely to be found.
With respect to the general scheme in Figure 2,in[9 ],
the feature vector
x is split into two feature vectors x
1
and x
2
of the same length and two BCH encoder are
used. Specifically, two tokens k
1
and k
2
are employed
to generate two codewords
c
1
and c
2
obtained each
from one of the two employed BCH encoders. Eventu-
ally the secret data
y
1
¼ x
1
c
1
and y
2
¼ x
2
c
2
are
obtained. Therefore the stored information will be
given by ð
s; y
1
; y
2
; hðk
1
Þ; hðk
2
ÞÞ. The authentication
step is dual with respect to the enrolment stage. The
authors of [9] point out that the division strategy is
needed to balance the desired verification accuracy and
the BCH code error correction capabi lity.
In [10] the authors use the fuzzy commitment
scheme for the protection of binary iris template,
namely the iriscode [6], by employing a cascade of
Reed Solomon codes and Hadamard codes to handle
the intra-variability of the biometric templates. This
choice has been driven by an exhaustive study of the
error patterns which can be encountered employing
iris codes. The authors propose a fuzzy commitment
architecture, where a two-layer error correction
method is performed. The outer layer uses a Hada-
mard code to correct random errors at the binary level
which are generated by CCD camera pixel noise, iris
distortion, or other image-capture effects which can
not be corrected by the initial preprocessing. The inner
layer uses a Reed Solomon code to correct burst errors
in the iriscode, due to und etected artefact like eyelashes
or specular reflections in the iris image. The proposed
architecture is tested on a proprietary database with
700 iris samples from 70 different eyes, with 10 samples
from each eye. It has been found out that an error
free key can be reproduced from an actual iriscode
with a 99:5% success rate. Iris orientation is of big
concern when unlocking the key in the fuzzy commit-
ment scheme. Multiple attempts have to be performed,
shifting the observed iris code by octect-bits, being
impossible to cyclically scroll the iris sample as in the
unprotected approach.
In [11] the application of the fuzzy commitment
scheme, for the protection of biometric data, is dis-
cussed. Specifically, a method for finding an upper
bound on the underlying error correction capability,
when using a fuzzy commitment scheme is provided.
The analysis is conducted by introducing a model for
the recognition process, composed of two binary sym-
metric channels, the matching and the non matching
channel. Specifically, the first is used to model the
errors coming from the matching between templates
belonging to the same user. The latter is used to model
the errors coming from the matching between tem-
plates belonging to different users. An erasure mecha-
nism is introduced in the matching channel to manage
the template dimension variability due for example to
occlusions. Moreover, a practical implementation of
the fuzzy commitment for iris template protection is
proposed, employing as error correcting codes the
product of two Reed Muller codes, together with a
specific decoding process, derived from the min-sum
decoding algorithm. The proposed protection scheme
is tested on a public iris database. The authors show
that correction performance close to the theoretical
optimal decoding rate are obtained.
The fuzzy vault cryptographic scheme [8] consists
in placing a secret S in a vault and in securing it by
using a set of unordered data A ¼fa
1
; a
2
; ; a
N
g,
which in our biometric context represents the biomet-
ric template. Specifically, a polynomial pðxÞ, whose
coefficients are given by the secret S, is generated
and the polynomial projections pða
i
Þ, for all the
elements belonging to A, are evaluated. Then a
large number of chaff points, which do not lie on
the polynomial pðxÞ, are arbitarily chosen. Specifically,
M unique points fc
1
; c
2
; ; c
M
g are randomly set
with the constraint that c
j
6¼ a
i
, for j ¼ 1; 2; ; M
and i ¼ 1; 2; ; N. Then, anoth er set of M ran-
dom points fd
1
; d
2
; ; d
M
g, such that d
j
6¼ pðc
j
Þ,
j ¼ 1; 2; ; M, is chosen. The concatenation of the
two sets fða
1
; pða
1
ÞÞ; ða
2
; p ða
2
ÞÞ; ; ða
N
; pða
N
ÞÞg
and fðc
1
; d
1
Þ; ðc
2
; d
2
Þ; ; ðc
M
; d
M
Þg represents the
vault V which secures both the secret and the template.
When a user tries to unlock the vault, another set of
unordered data A
0
can be used. If the set A
0
substan-
tially overlaps with the set A then the user can identify
many points of the vault lying on the polynomial. If the
overlapping point number is sufficient, the polynomial
can be identified by using Lagran ge interpolation, thus
identifying the secret. If the two sets are significantly
different, the polynomial reconstruction is unfeasible.
Many implementations of the general principle here
sketched have been proposed in literature.
In [12], iris data are used for securing the vault. The
method is depicted in Fig. 3. Specifically, the feature
extraction is performed as follows. After having loca-
lized the iris region, it is transform ed into a polar
coordinate image and two regions not occluded by
Iris Template Protection
I
869
I
