Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.

performance is typically measured by conventional error
measures such as False A c cept Rate (FAR), False R eject
Rate (FRR), and Equal Error Rate (EER). In terms of
EER, many of the previously cited works achiev e
performance 5% (see Table 1). Naturally, FAR and
FRR’s can be tailo red based on where one wishes to
fall on a traditional Receiver Operating Characteristic
(ROC) curve. It is important to note that the literature
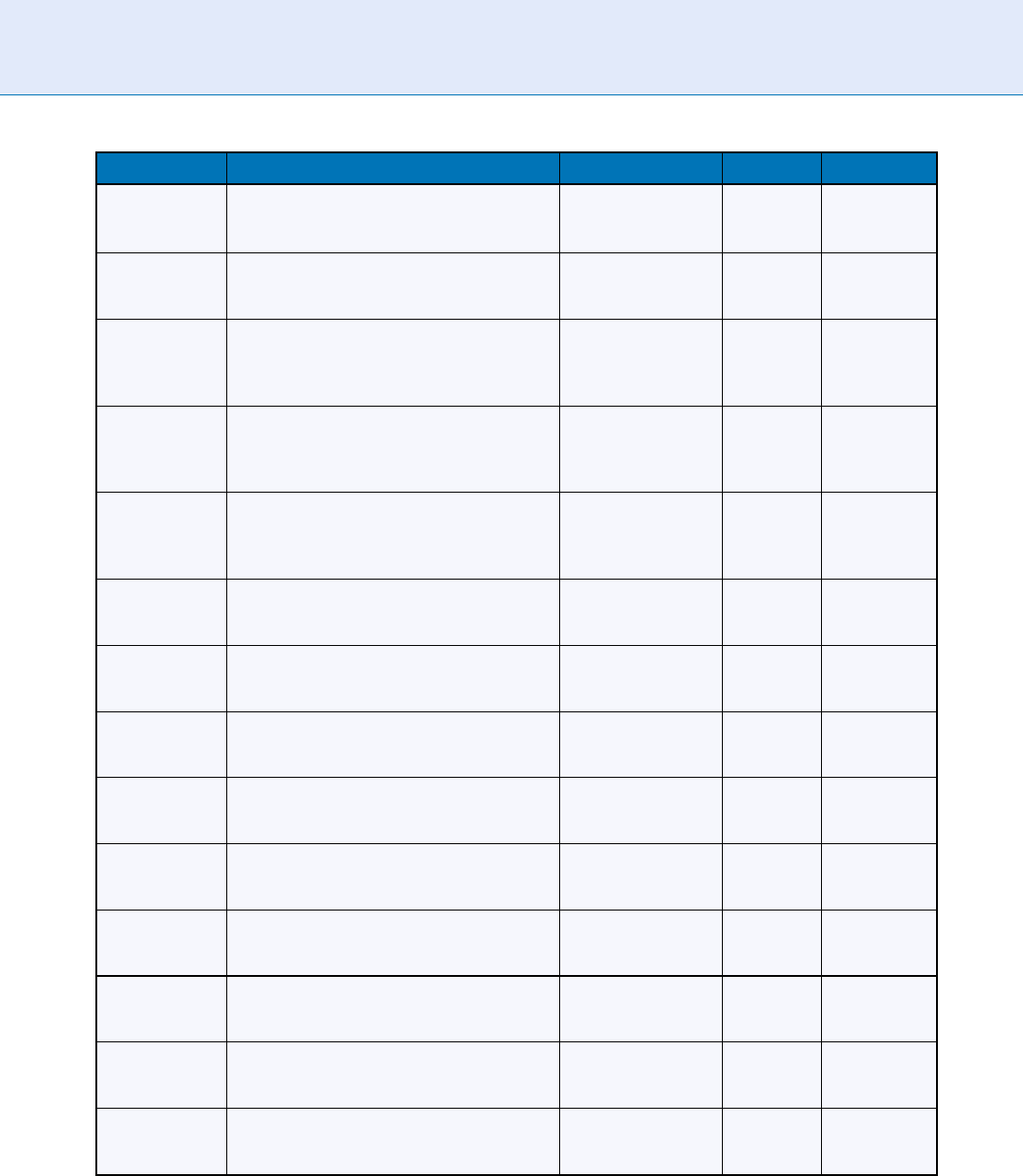
Keystroke Recognition. Table 1 Overview of Selected Works in Keystroke Recognition
Work Feature(s)/Algorithm Input Scope Performance
Gaines and
Lisowski
(1980) [4]
Latency between 87 lowercase digraphs using
sample t-tests
300–400 word
passage 2 times
7 secretaries FAR 0% (0/55)
FRR 4% (2/55)
Garcia
(1986) [10]
Latency between 87 lowercase digraphs and
space key and complex discrimination using
Mahalanobis distance function
Individual’s name
and 1000 common
words 10 times each
(N/A) FAR 0.01%
(N/A) FRR 50%
(N/A)
Young and
Hammon (1989)
[11]
Plurality of features including: digraph
latencies, time to enter selected number
of keystrokes and common words using
Euclidean distance
(N/A) (N/A) (N/A)
Joyce and Gupta
(1990) [5]
Digraph latencies between reference strings
using mean and standard deviation of latency
distance vectors
Username, password,
first name, last name
8 times each
33 users of
varying
ability
FAR 0.25%
(2/810) FRR
16.36%
(27/165)
Brown and
Rogers
(1993) [12]
Latencies and hold times using Euclidean
distance and neural networks
Usernames, 15–16
character avg.
1,000 sequences
tested
21 and V 25
users
FAR 4.2%–
11.5% (N/A)
FRR (N/A)
Obaidat and
Macchiarolo
(1993) [6]
Digraph latencies between reference strings
using neural networks
15 character phrase
20 times each
6 users 97% overall
accuracy
Obaidat and
Sadoun
(1997) [7]
Digraph latencies and key hold times using
multiple machine learning algorithms
Username 225 times/
day for 8 weeks
15 users FAR 0% (N/A)
FRR 0% (N/A)
Monrose and
Rubin (1997) [1]
Latencies and durations with normalized
Euclidean distance and weighted/
nonweighted maximum probability
Passages of text over
7 weeks
(N/A) Identification
framework
Maisuria and
Ong and Lai
(1999) [13]
Digraph latencies with neural networks
(multi-layer perceptron)
passwords 60 times
over 3 periods
20 users FAR 30%
(N/A) FRR
15% (N/A)
Monrose, Weiter,
and Wetzel
(2001) [8]
Digraph latencies and key hold times,
algorithm employed is unclear
8 character password 20 users FAR % (N/A)
FRR 45% (N/A)
Bergadano,
Gunetti, and
Picardi (2002) [9]
Trigraph duration using degree of disorder 683 character text
5 times
44 users FAR 0.04%
(1/10,000) FRR
4% (N/A)
Yu and Cho
(2004) [14]
GA-SVM’s and wrapper FSS on hold times and
digraph intervals
6–10 character
passwords 150–400
gen/user and 75 imp
21 users FAR 0% (N/A)
FRR 3.69%
(N/A)
Bartlow and
Cukic (2006) [2]
Random Forests on digraph latencies and
hold times digraph latencies
usernames + 8 and 12
char passwords
9,000 sequences
41 users FAR 2% (N/A)
FRR 2% (N/A)
Sung and Cho
(2006) [15]
GA-SVM’s and wrapper FSS on hold times and
digraph intervals
6–10 character
passwords 150–400/
user and 75 imposter
21 users FAR 3.85%
(N/A) FRR
13.10% (N/A)
880
K
Keystroke Recognition

has not firmly established whether the technology is
sufficient for biometric systems operating in identi fi-
cation mod e as the focus of past research is almost
exclusively tailo red to verification based systems. It is
also important to note the trend of decreasing data
requirements as earlier works required extremely long
passages of text whereas most recent works require
only usernames, passwords, or both. Related to this
trend, keystroke dynamics need not be appl ied only at
the time of login, which may lead to time-of-check-
time-of-use vulnerabilities. Instead, they can be ap-
plied transparently throughout the span of a period
of use. This feature can allow systems to continually
check for the presence of insider threat where an
authorized user may login to a system and subsequent-
ly allow an unauthorized user access. If a system does
not require a continual verification environment, key-
stroke recognition is also very suitable for a
▶ chal-
lenge response type framework where the user is
periodically authenticated.
Besides stand-alone biometric systems, keystroke
recognition can be used as an augment to traditional
username/password systems. This process is often
called
▶ credential hardening or password hardening.
Monrose et al. first proposed the idea [8] and Bartlow
et al. also explored the concept [2]. Both works show
how the addition of keystroke recognition to tradi-
tional authentication mechanisms can drastically
reduce the penetration rate of these systems. Works
of this nature may also bode well in online authentica-
tion environments such as banking and e-commerce
websites which now commonly require secondary
verification layers.
Either as a stand-alone biometric or an augment
to a traditional username/password scheme, key-
stroke dynamics are arguably more cancelable or re-
placeable than physiological biometrics. The idea
of cancellable biometrics touches on the fact that
the threat of biometric compromise exists and is
often realized. With fingerprint, face, iris, etc., it is
often difficult to reissue a biometric authentication
mechanism as fingers, faces, and irises are not easily
removed and replaced in humans. In keystroke recog-
nition however, the behavior which induces the bio-
metric can be changed. In other words, if a user’s
keystroke recognition template is compromised, the
data in which the template is based (i.e., password/
passphrase) can simply be changed which will result
in a new biometric template. For obvious reasons, this
is seen as a very attractive feature of keystroke
recognition.
Beyond the scope of academic research, many
patents have been issued in the field including:
Garcia (4,621,334 - 1986) [10], Young and Hammon
(4,805,222 - 1989) [11], Brown and Rogers (5,557,686 -
1996), and Bender and Postley (7,206,938 - 2007). In
addition to patents, there are many commercial offer-
ings of keystroke recognition systems. Two popular sys-
tems are BioPassw ord ß(http://www.biopassword.com/)
and iMagic Software ß(http://www.imagicsoftware.
com). Systems such as these are attractive as the over-
head of keystroke recognition in terms of hardware
deployment and seamless integration into currently
existing authentication systems is typical ly much less
than that associated with physiological biometrics such
as fingerprint, iris, and face.
Despite the maturity of the field over t he last
30 years, there are still many challenges that are yet to
be solved. Three main challenges are associated with
the data required to train keystroke recognition sys-
tems. First, few works have formally set out to deter-
mine the amount of sequen ces required to sufficiently
establish a typing signature ready for operational
deployment. For a system to be deployable, it must
have a realistic training requirement that the users are
willing to incur. It seems that repeatedly typing a
username and password combination 50 or more
times would be unacceptable in the eyes of most
users, yet five may be insufficient in terms of meeting
established security goals. Second, as passwords need
to be replaced or reissued, the problem of retraining
needs to be addressed. Once again, these retraining
requirements are yet to be firmly established. Third,
the behavioral nature of this keystroke recognition
requires a slightly more involved data collection pro-
cess than what is ty pical in conventional physiological
biometric systems. Most notably, one cannot simply
compare genuine input of one use r to genuine input
of another user in order to establish an instance of
imposter input as the data is often different for every
user (i.e., usernames/passwords). As a result, most
academic research will have users type the credentials
or data associate d with other users to arrive
at imposter sequences for training. Clearly this is not
feasible in operational system s as passwords are fre-
quently reset. Therefore, the issue of automatic gener-
ation of imposter data is an area that needs to
be explored.
Keystroke Recognition
K
881
K
Summary
Keystroke recognition is a behavioral biometric which
authenticates an individual not on the basis of what is
typed but the nature of how it is typed. A large base of
research has accumulated in the field over the last
30 years estab lishing its potential both as a stand-
alone biometric and an augment to traditional
username/password authentication schem es. Due to
its transparent nature, low cost of deployment, and
seamless fit into currently existing commercial and
governmental applications, it is an excellent candidate
for increasing the security of authentication systems.
Related Entries
▶ Biometric Encryption
▶ Cancelable Biometrics
▶ Verification
References
1. Monrose, F., Rubin, A.D.: Authentication via Keystroke Dynam-
ics. In: ACM Conference on Computer and Communications
Security, pp. 48–56 (1997)
2. Bartlow, N., Cukic, B.: Evaluating the Reliability of Credential
Hardening through Keystroke Dynamics. In: ISSRE, IEEE Com-
puter Society, Washington, DC, USA, pp. 117–126 (2006)
3. Mueller, S.: Upgrading and Repairing PCs, 15th edn. QUE,
Indianapolis, IN (2004)
4. Gaines, R., Lisowksi, W., Press, W., Shapiro, S.: Authenti-
cation by keystroke timing: Some preliminary results. Rand
Report R-256-NSF, The Rand Corporation, Santa Monica, CA
(1980)
5. Joyce, R., Gupta, G.: Identity authentication based on keystroke
latencies. Commun. ACM 33(2), 168–176 (1990)
6. Obaidat, M.S., Macchairolo, D.T.: An on-line neural network
system for computer access security. IEEE Trans. Industrial
Electronics 40(2), 235–241 (1993)
7. Obaidat, M.S., Sadoun, B.: Verification of computer users using
keystroke dynamics. IEEE Trans. Syst. Man Cybern. 27(2),
261–269 (1997)
8. Monrose, F., Reiter, M.K., Wetzel, S.: Password hardening based
on keystroke dynamics. Int. J. Inf. Sec. 1(2), 69–83 (2002)
9. Bergadano, F., Gunetti, D., Picardi, C.: User authentication
through keystroke dynamics. ACM Trans. Inf. Syst. Secur. 5(4),
367–397 (2002)
10. Garcia, J.: Personal identification apparatus. Patent 4,621,334,
US Patent and Trademark Office, Washington, DC (1986)
11. Young, J., Hammon, R.: Method and apparatus for verifying an
individuals identity. Patent 4,805,222, US Patent and Trademark
Office, Washington, DC (1989)
12. Brown, M., Rogers, S.J.: User identification via keystroke char-
acteristics of typed names using neural networks. Int. J. Man
Mach. Stud. 39(6), 999–1014 (1993). DOI http://dx.doi.org/
10.1006/imms.1993.1092
13. Maisuria, L.K., Ong, C.S., Lai, W.K.: A comparison of
artificial neural networks and cluster analysis for typing
biometrics authentication. In: International Joint Conference
on Neural Networks (IJCNN), vol. 5, pp. 3295–3299 (1999)
14. Yu, E., Cho, S.: Keystroke dynamics identity verification - its
problems and practical solutions. Comput. Secur. 23(5),
428–440 (2004)
15. Sung, K.S., Cho, S.: GA SVM wrapper ensemble for keystroke
dynamics authentication. In: ICB, Springer-Berlin-Hiedelberg,
pp. 654–660 (2006)
Kinematic Body Model
Virtual skeleton structure comprising a fixed number
of joints with specified angular degrees-of-freedom.
The values assigned to these joint angles define the
3D pose of the body.
▶ Markerless 3D Human Motion Capture from
Images
Kinematics
The description of object motion over time, generally
expressed in terms of posi tion, velocity, and
acceleration.
▶ Human Detection and Tracking
Knowledge-based Gait Recognition
▶ Gait Recognition, Model-Based
Known Traveler
▶ Registered Traveler
882
K
Kinematic Body Model

L
L2 norm
L2 norm is a standard method to compute the length
of a vector in Euclidean space. Given x =[x
1
x
2
...x
n
]
T
,
L2 norm of x is defined as the square root of the sum of
the squares of the values in each dimension.
▶ Iris Super-Resolution
Lambertian Law
Lamberts cosine law states that the reflected or trans-
mitted luminous intensity in any direction from an
element of a perfectly diffusing surface varies as the
cosine of the angle between that direction and the
normal vector of the surface.
▶ Face Recognition, Near-infrared
▶ Heterogeneous Face Biometrics
Lambertian Surface
Lambertian surface is a technique used to light partic-
ular surfaces of vir tual objects within a scene, which
causes all clo sed polygons to reflect light equally in all
directions. This means that the surface brightness to an
observer is the same regardless of the observer’s angle
of view.
▶ Face Sample Quality
▶ Illumination Compensation
Large Scale Biometric Database
Based on their size all biometric datasets are classified
into three (some sources indicate four) categories:
small size, medium size, large scale, and very large
scale data bases. The size of datasets is determined by
the number of participating users. A small size data-
base can contain biometric data of up to 1,000 users.
A medium size database accounts for 10,000–100,000
users. A large (and very large) scale datasets incl ude
biometric data of more than 1,000,000 users. Since
each user can be represented by two or more classes
in a database, some references indicate the size of
datasets in classes rather than in users.
▶ Face Databases and Evaluation
▶ Iris Sample Synthesis
▶ Large Scale System Design
Large Scale Biometric System Design
▶ Large Scale System Design
Large Scale System Design
CHIN-HUNG TENG
1
,WEN-HSING HSU
2
1
Yuan Ze University, Taiwan, ROC
2
National Tsing Hua University, Taiwan, ROC
Synonym
Large scale biometric system design
#
2009 Springer Science+Business Media, LLC

Definition
A large scale biometric system is a system involving
the authentication of a huge number of users via the
biometric features. A Large Scale
▶ Biometric Database
is generally designed for civ ilian applications and is not
merely the increased size of database compared to the
personal use system. In the case of a large scale system,
there is greater emphasis on the issues of system reli-
ability and flexibility. To meet the requirements of
public use, the system must have a high enrollment
rate and adapt to environmental variations. Security is
another issue in designing such a system due to the
large number of users enrolled. A one-to-many match-
ing may sometimes lead to system breakdown, thus
other authentication policies may be applied to com-
plement the one-to-many matching to enhance system
reliability, such as cross validation of multiple biomet-
ric features.
Introduction
There is a long history of fingerprint verification/identifi-
cation in law enforcement, a large scale biometric system
which is primarily used for determining the identity of a
suspect or a dead person. In the early stage, fingerprint
verification is achieved by an expert who must visually
match the
▶ minutiae of different fingerprints, which is
undoubtedly a tedious and time consuming task. In
recent years, due to advances in computer recognition
techniques and the extensive development of biometric
sensor devices, the identity of an individual can be
authenticated through biometric features fully auto-
matically by computers. A biometric system has the
distinct advantages of high security and convenience,
thus theoretically it can find many applications where
the users need to prove the claimed identity to access
the required services. However, due to the issue of
human rights (it is unfortunate that a fingerprint is
always associated with crime), many people are unwill-
ing to provide their biometric features in public sys-
tems, thus most biometric applications are at present
restricted to personal use such as notebook or mobile
phone login. After 9/11 attacks, many people have
realized the importance of securit y and this has pus hed
the government to initiate many large scale biometric
systems to enhance the security for access in the gov-
ernment’s facilities and information systems. In fact,
a biometric system is not merely used for preventing
terrorist attacks. Many government provision such as
welfare disbursement, driver license application, and
voter registration can benefit from the construction of
a nationwide biometric system. For example, many
airports have installed a biometric authentication sys-
tem to expedite the procedure of visa and passport
examination. The United States government has
launched a Personal Identity Verification (PIV) pro-
gram [1] to manage the authentication of federal
employees and contractors for access to federal facil-
ities and information systems. It is obvious that in the
future more and more large scale biometric systems
will be developed. This essay outlines some issues
that should be considered in designing a large scale
biometric system and lists some of the applications
of a system.
Operation of a Large Scale Biometric
System
Typically, there are two authentication modes for a
biometric system: verification (one-to-one matching)
and identification (one-to-many matching). Verifica-
tion is a procedure for comparing a biometric feature
set against a template with claimed identity. For a large
scale system, the enrolled template can be stored in
a centralized database, a set of distributed databases
(sometimes at distant places), or a user carried medi-
um such as an IC card, depending on the requirements
of applications. Different arrangements have their own
advantages and disadv antages. For instance, in the PIV
program, the biometric templates are distributed to
the user’s PIV card, thus saving effor t in managing
the huge number of records of biometric data. How-
ever, the data stored in the card must be carefully
protected so as to prevent an impostor replacing or
stealing the biometric data to crack the system. Usually,
the protection mechanism is achieved by a Public Key
Infrastructure (PKI).
Identification is a procedure for comparing a bio-
metric feature set against all templates in the database
to determine the correct identity. Generally, if a biomet-
ric system cannot achieve a sufficient low False Matching
Rate (FMR), it is not recommended to use the one-to-
many matching to guard access to some services
or resources since it will greatly reduce the security
level and result in a long matching time. However,
884
L
Large Scale System Design
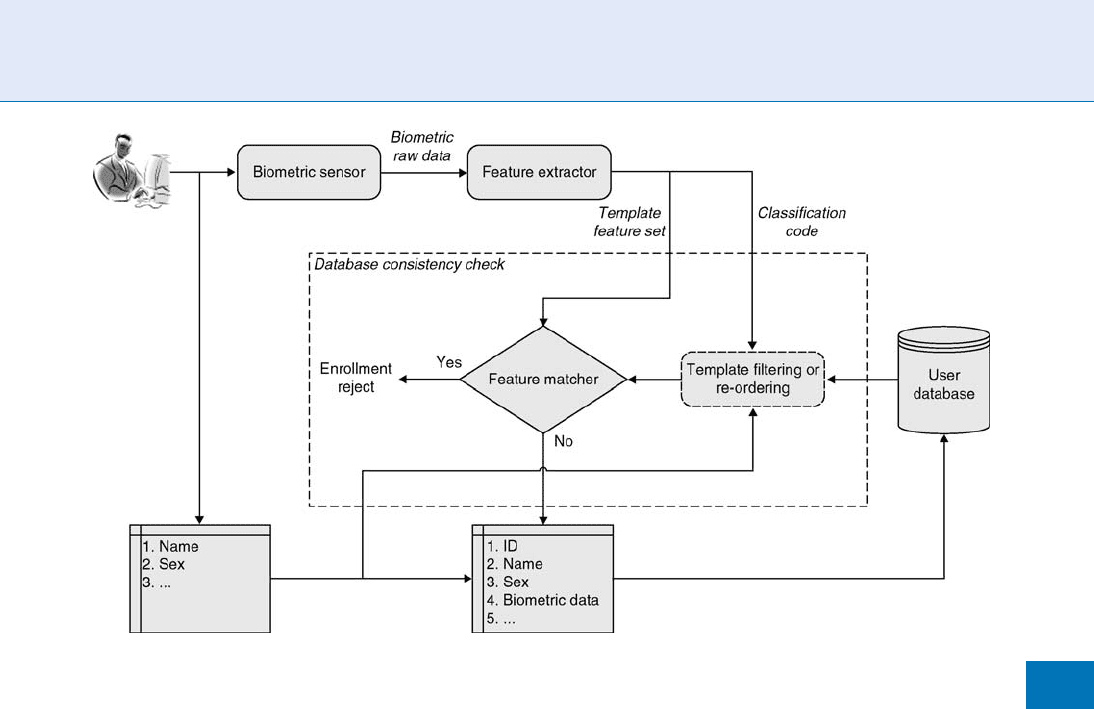
identification is at times necessary for some applications
such as detecting multiple enrollments in a system. If an
application requires identification in a large scale bio-
metric system, some strategies must be applied to reduce
the searching size so as to enhance security as well as to
expedite the matching process. An enrollment process
for a large scale system with the functionality of detecting
duplicate enrollments is presented in Fig.1. To reduce
the number of matchings, some reliable information
about the applicant can be used to filter out incorrect
biometric templates. For example, it is possible to cut
out a large portion of templates to be matched by
the sex of the applicant. If other information such as
the applicant’s eye color can also be used to reliably
classify the users, the search size can be further
reduced. Normally, a biometric classification mecha-
nism can also be included in the system to accelerate
the identification process. For instance, a fingerprint
can be categorized on the basis of the ridge pattern into
arch, right loop, left loop, whorl, etc. Typically, if a
classification system cannot achieve a sufficiently high
level of accuracy to effectively cut out the templates
to be matched, classification is just a re-ordering of the
templates that increases the probability of matching
the biometric templates from the same individual
as soon as possible. This implies that a classification
system can efficiently detect duplicate enrollments if
the applicant has enrolled in this system previously,
but for a new applicant, re-ordering of matching tem-
plates has no benefit to the system since the biometric
template of the applicant is not in the database.
Some Issues for Designing a Large Scale
Biometric System
In general, designing a large scale biometric system is
different from personal use systems. Some issues
should be carefully considered.
1. Cross-sensor problem and the development of stan-
dards: For a personal use biometric system, the
biometric features for enrollment and verification
are usually acquired from the same biometric sensor.
This obviously rules out the problem of cross-sensor
matching which sometimes leads to performance
degradation due to sensor discrepancy. However,
cross-sensor matching is quite common in a large
scale system where the enrollment and verification
sensors are typically different. Sensor discrepancy
is due to several factors such as the manufacturing
process, sensors developed by different vendors, and
even the different sensor design methodologies
Large Scale System Design. Figure 1 The enrollment module of a large scale biometric system.
Large Scale System Design
L
885
L

such as optical-based and chip-based fingerprint
sensors. One way of solving the problem of cross-
sensor matching is to establish a standard to regulate
the quality of captured biometric data such as the
FBI’s fingerprint image quality specification [2].
Biometric standards, however, are not restricted to
the area of defining the quality of biometric data.
The standards for the format of biometric template
and the
▶ application programming interface
(API) have also been developed. Not only, finger-
print image quality standard has been established,
but also biometric API has been developed such as
BioAPI [3 ]. In fact, many standards for the security
industry, such as the interface of access control,
audio verification, and control panels, have also
been developed. The Open Systems Integration
and Performance Standards (OSIPS) of the Securi-
ty Industry Association (SIA) [4] is a well-known
program for the development of security standards.
Under the OSIPS, a series of standards have been
published to meet the requirements of emerging
IT products and services in the securit y industry.
These standards allow different manufacturers to
cooperate for designing very large scale biometric
systems and create more business benefit from
security applications. It is likely that in the future
only those biometric products that comply with
these standards may be accepted by the market.
2. Poor biometric quality in the case of specific users: It
has been known that the quality of biometric features
of some specific users is very poor, especially those
engaged in particular occupations. For instance, the
fingerprints of some porters are generally worn to
such an extent that it is quite difficult to recognize
their fingerprints. Because a large scale biometric
system is generally designed for public use, it cannot
reject those users with poor biometric quality or
those with biometric deficiency. In addition to non-
technique complement schemes, a biometric system
should further improve their performance, including
biometric feature enhancemen t as well as matching
algorithm, to accommodate those users with poor
biometric features. This system should generate high
quality biometric data or templates for a very large
proportion of the user population.
3. Environmental variations: Environmental variations
such as illumination or temperature variations
sometimes lead to performance degradation of
a biometric system because of unequal sensor
conditions of the captured biometric templates
to be matched. For instance, face recognition is typi-
cally quite sensitive to ambient illumination varia-
tions. For a personal use biometric system, biometric
sensors are generally set up in an indoor and control-
lable situation so as to minimize environmental var-
iations. However, for a public use biometric system,
sensors may be set up outdoors, thus any biometric
quality degradation that may be due to environmen-
tal variations should be taken into account when
designing a large scale biometric system. A large
scale system is expected to generate high quality bio-
metric data across the full range of environmental
variations for the intended applications.
4. Performance degradation for one-to-many match-
ing: As outlined previously, one-to-many matching
may have performance degradation. For example, if
a biometric system has 0.0001 false matching rate
(FMR) and there are 10,000 biometric templates in
the database, then a one-to-many matching against
this database will always produce a successful
matching with a statistical probability of 1. Thus,
when applying a one-to-many matching in a large
scale system, system designer must carefully compute
the resulting error rate and check whether it satisfies
the demand of the intended application. If a one-
to-many matching is inevitable for a large scale
application, several mechanisms can be included in
the system to enhance the security level. For instance,
it is possible to reduce the probability for false
alarm matching by cross validation of multiple bio-
metric features. Multiple biometric features may be
obtained from the same biometric type such as fin-
gerprints of different fingers, or from different types
such as face, voice, fingerprint, and hand geometry
etc. Regardless of which biometric features are used
for cross validation, the resulting security level
should be carefully calculated to ensure that it
meets the security requirements. Beside a degraded
error rate for one-to-many matching, the increased
matching time may at times become a design issue
for a large scale system. If cost is not a critical factor,
the matching time can be greatly reduced by distri-
buting the matching task into several matching
machines. An efficient classification scheme can
also be used to reduce the matching time. If a classi-
fication algorithm can effectively filter out the un-
necessary templates to be matched, it can also
improve the error rate of one-to-many matching.
886
L
Large Scale System Design
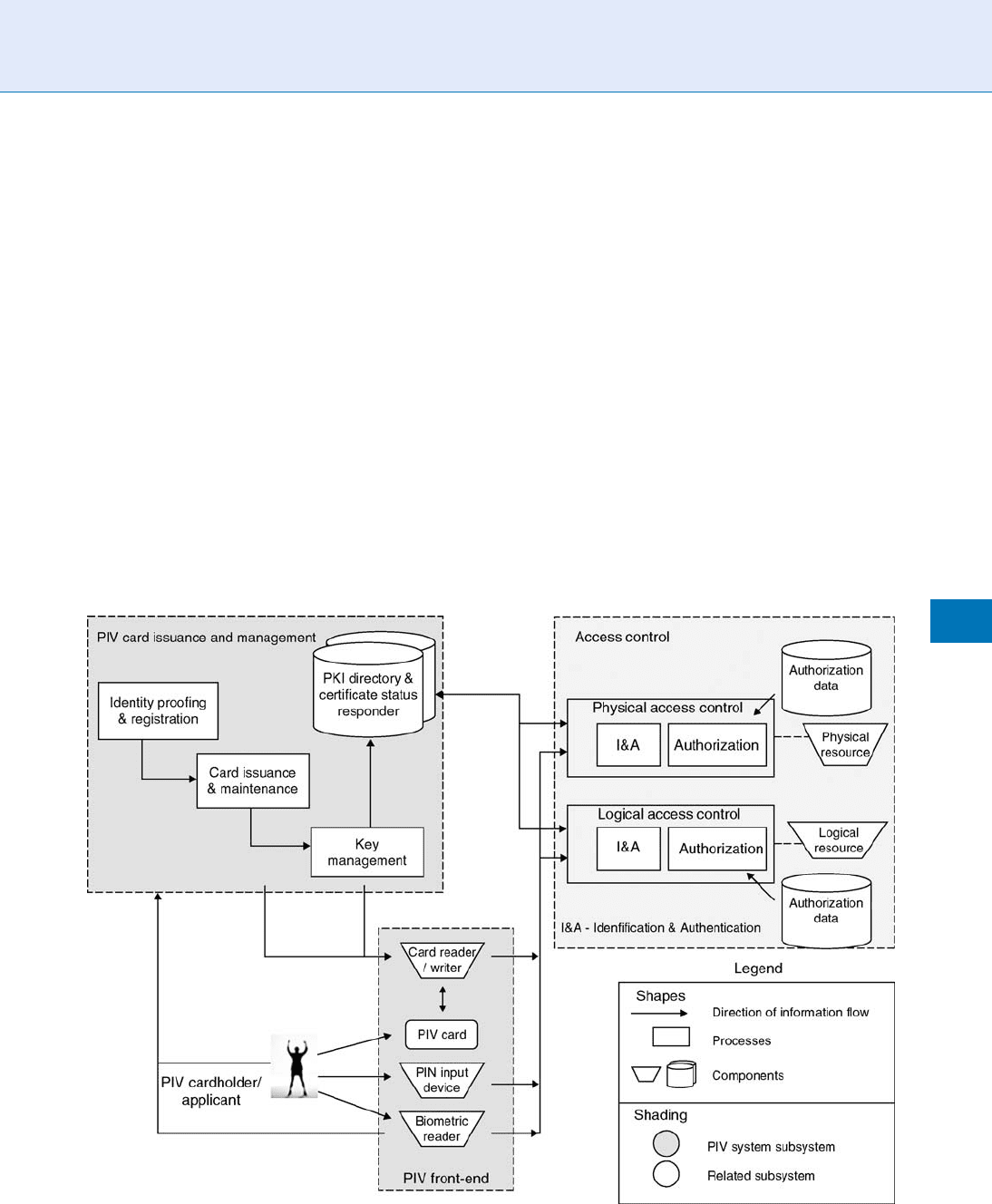
The PIV Progr am of the United
States Government
The PIV program of the United States government is
a large scale biometric authentication project intended
to control the federal employees and contractors for
access to federal facilities and information systems.
Under this program, every applicant is issued a PIV
card on which two types of bio metric information are
recorded: one is the photograph of the applicant which
is printed on the card and the other is the applicant’s
fingerprint template which is stored in the card mem-
ory. The photograph of the applicant is used for visual-
based authentication which serves as the lowest level
of identity assurance. This visual-based authentication
is necessary in situations where electronic biometric
authentication is not workable, e.g., the PIV card read-
ers cannot be installed on the site. In other situations,
authentication is automatically achieved by comparing
the cardholder’s fingerprint against the template stored
in the card. The system notional model of the PIV
program and its conceptual operation are summarized
in Fig.2.
The PIV program is open to biometric manufac-
turers worldwide, thus any biometric vendor whose
techniques comply with the requirements of the PIV
can join this program. For this purpose, the Depart-
ment of Commerce and the National Institute of Stan-
dard and Technology (NIST) have published a series of
standards to regulate the biometric tech niques. The
NIST has also designed a performance evaluation test
to cross verify the fingerprint verification techniques
developed by different manufacturers [5]. In this test,
the entire process of fingerprint verification is divided
into two phases: feature extraction and template
matching. The goal of this test is to ensure the reliabil-
ity of extracted fingerprint features and the capability
of fingerprint matching algorith m. The false matching
Large Scale System Design. Figure 2 The system notional model of the PIV program. (Reprinted from Personal Identity
Verification (PIV) of Federal Employee and Contractors, Federal Information Processing Standards Publication).
Large Scale System Design
L
887
L
rate (FMR) and the false non-matching rate (FNMR)
for pairs of feature extraction module and fingerprint
matching algorithm from different vendors are evalu-
ated to check whether they can achieve the desired
security level. This test does not only examine the
compatibility of biometric techniques developed by
different vendors but also checks the fingerprint recog-
nition accuracy of the vendors. Only those biometric
manufacturers who pass the test can serve as the bio-
metric technique s providers for the PIV program.
Web Service Authentication (WSA)
With advances in internet technology, a biometric au-
thentication system can also be applied to the browser
to replace the traditional password-based login system
(i.e., a web service biometric authentication), leading
to a more convenient and secured biometric solution
on the internet. This web service authentication is not
limited to biometric applications of personal use but
can be extended to a large scale biometric system such as
a web-based time-attendance system for a global com-
pany with a number of branches around the world. Each
employee can register his/her attendance time via this
web service authentication system even when he/she
is in a remote branch. Typically, there are three compo-
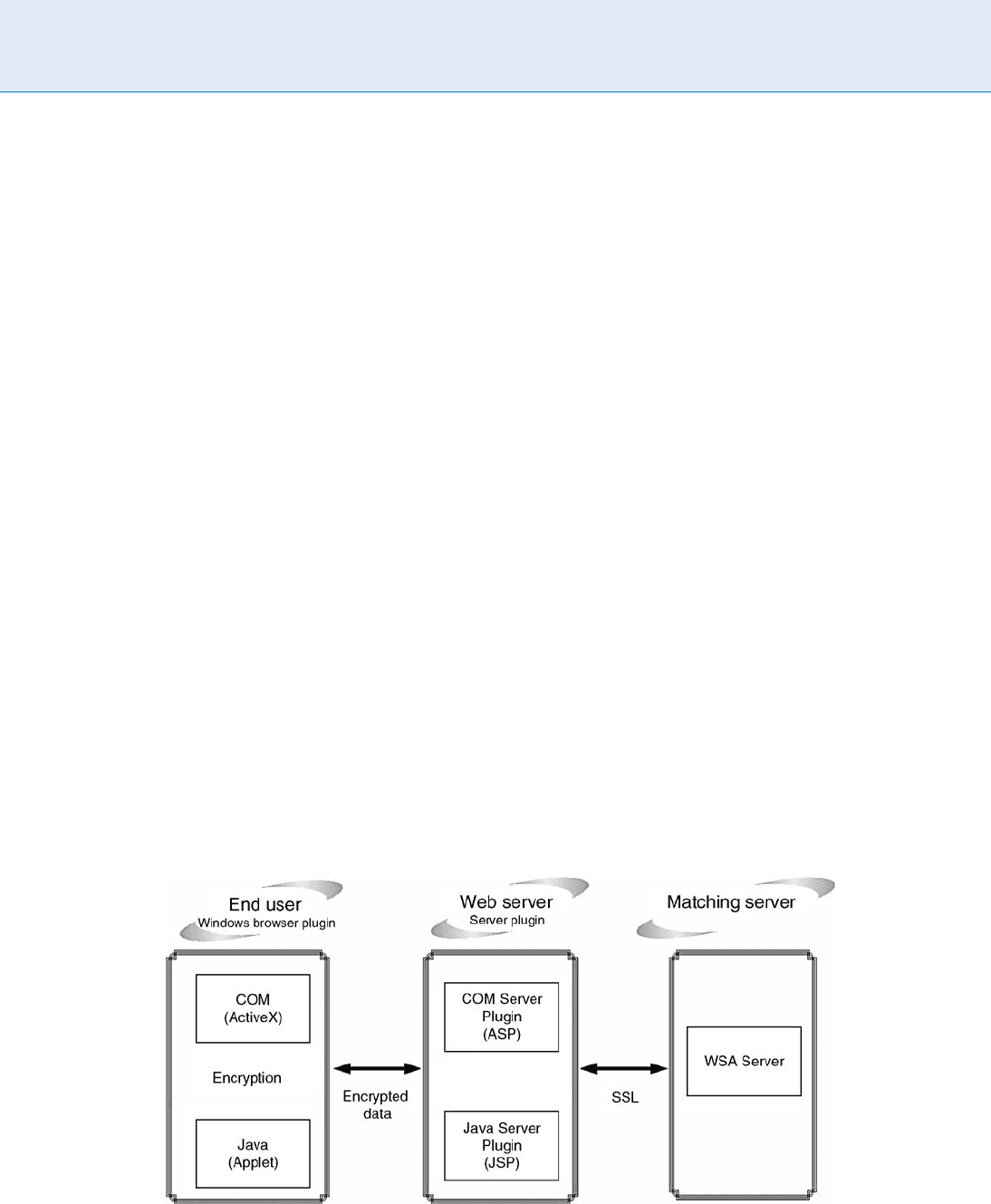
nents of a web service authentication system as illu-
strated in Fig.3. The terminal of End User is usually
a browser with some plugins ( ActiveX in IE or Java
applet for other platforms) in charge of connecting the
biometric sensor and sending the extracted biometric
template to the Web Server. The Web Server is respon-
sible for managing the biometric templates and send-
ing the templates to be matched to the Matching
Server. The Matching Server deals with the requests
from different Web Servers (which may be devised for
various functions and applications) and respond w ith
the authentication results. All the communication data
between servers and browsers are transmitted via a secure
channel which is typically achieved by a data encryption
scheme. In this framework, each component has its
distinct functionality and role, thus the overall system
is easy to manage and maintain. In addition, since the
plugins can be installed directly by the internet, setting
up a web service authentication system is fairly simple.
A biometric reader installed on a computer with web-
access functionality is sufficient for completing the sys-
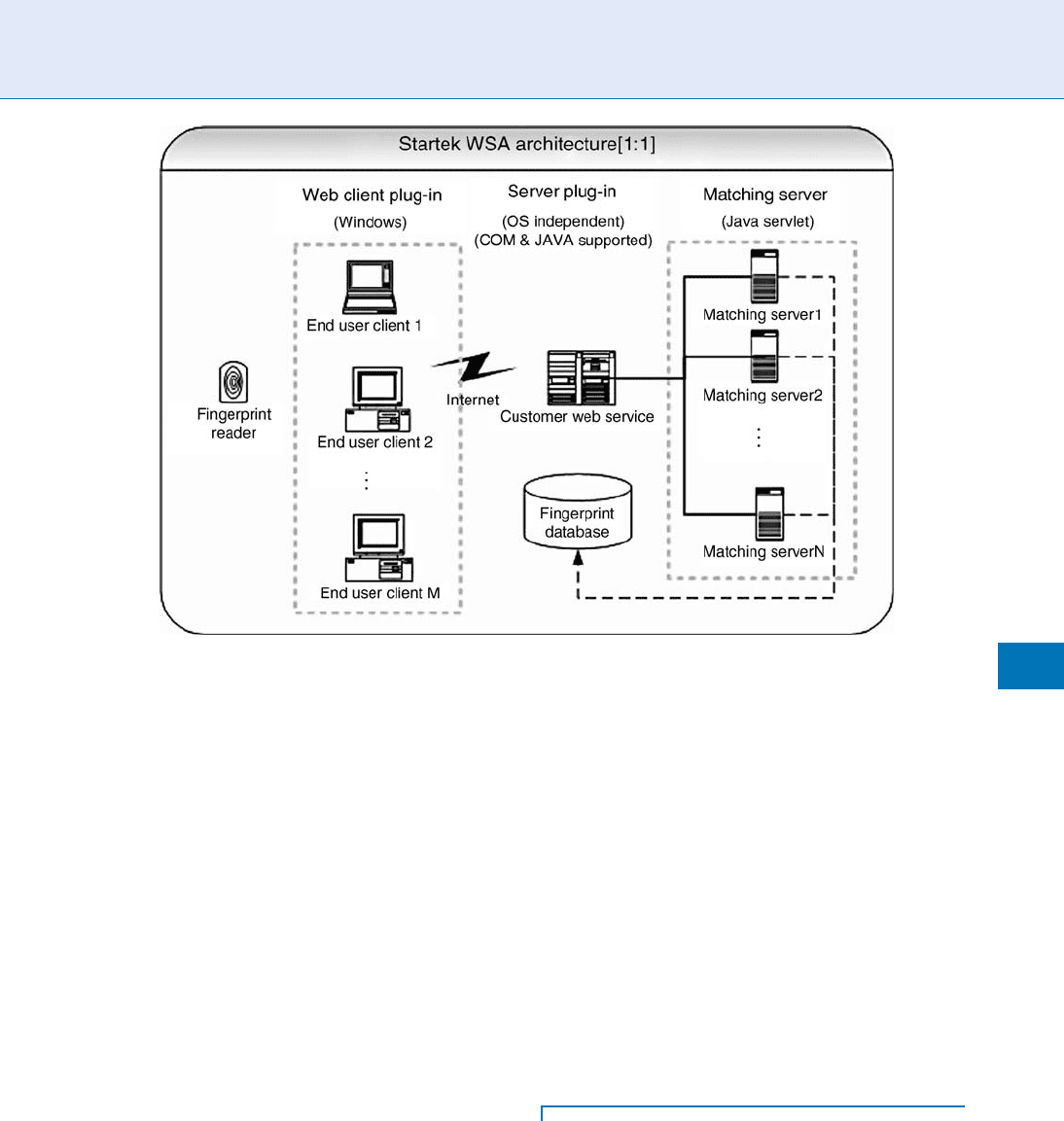
tem. A more general framework is depicted in Fig.4. The
matching servers can be extended to a matching array
thus significantly enhancing the matching efficiency. In
short, this web service authentication scheme is easy to
install, easy to manage and maintain, platform inde-
pendant, flexible function extension, and easy to inte-
grate to other systems, thus it is likely to be widely used
in the area of biometric recognition on the internet.
Summary
This essay presents a brief description of the operation
of a large scale biometric system and highlights several
Large Scale System Design. Figure 3 The three components for a web service authentication scheme (Data Source:
Startek).
888
L
Large Scale System Design
issues in designing such a system. It discusses a large
biometric project, the PIV program of the United States
government, and also examines a framework for bio-
metric application on the internet. Besides, it enumer-
ates the advantages of such a biometric network
application. The authors of this contribution aims to
provide a simple view to those who seek an initial
understanding of the design of a large scale biometric
system.
Related Entries
▶ Authentication
▶ Automated Fingerprint Identification System
▶ Biometric
▶ Enrollment
▶ Identification
▶ Verification
References
1. Personal Identity Verification; information available at: http://
csrc.nist.gov/piv-program/
2. Test Procedures for Verifying IAFIS Image Quality Requirements
for Fingerprint Scanners and Printers, MITRE Corporation
Technical Report, MTR-050000016, April 2005. Document
available at: http://www.mitre.org/tech/mtf
3. BioAPI Consortium; information available at: http://www.
bioapi.org/
4. http://www.siaonline.org
5. http://fingerprint.nist.gov/minexII/index.html
6. Personal Identity Verification (PIV) of Federal Employees
and Contractors, Federal Information Processing Standards
Publication
7. http://www.startek-eng.com/EN/prod_WSA20Solution.html
Large-Scale Evaluation
Large-scale evaluation is the evaluation that involves
testing on significant amounts of data, that is, Large
Scale Biometric Databases. It normally provides results
using the statistical measurements, such as average FAR,
FRR and/or ROC, and CMC curves.
▶ Face Databases and Evaluation
Large Scale System Design. Figure 4 A more general architecture for web service authentication (Data Source: Startek).
Large-Scale Evaluation
L
889
L
