Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.

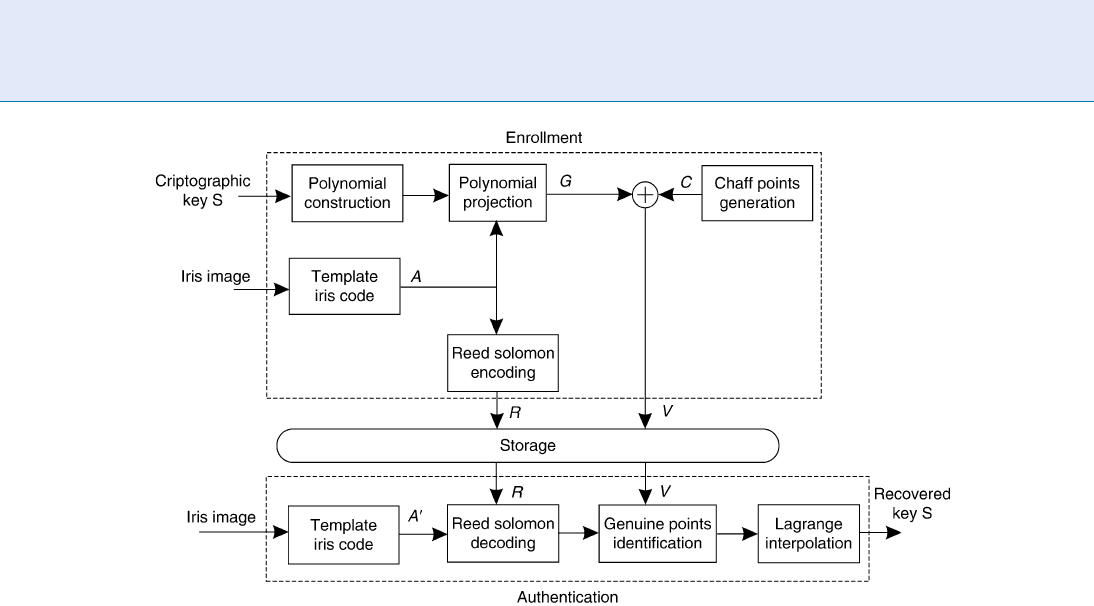
eyelids and eyelashes are selected. From each selected
region, eight iris blocks are derived and transformed
using Independent Component Analysis thus obtain-
ing 16 feature vectors. In order to take into account
the intra-class variations, the blocks extracted from
each image are clustered, employing a K-means algo-
rithm, thus generating an iris code of sixteen 8-bit
symbols, which represents the elements of the locking
set A. The vault locking is performed as sketched in
Figure 3 and uses the general principle of the fuzzy
vault scheme. However, in the implementation
proposed in [12], the locking set A is also encoded
using Reed Solomon codes, thus obtaining a set
R which is stored together with the set V obtained
by concatenating the genuine points at v obtained
concatenation G ¼fða
1
; pða
1
ÞÞ; ða
2
; pða
2
ÞÞ; ; ða
N
;
pða
N
ÞÞg, coming from the polynomial pðxÞ, and the
set c derived from the chaff point set C ¼fðc
1
; d
1
Þ;
ðc
2
; d
2
Þ; ; ðc
M
; d
M
Þg. The set R is employed during
authentication to correct potential errors, due to intra-
class variations, in the query iriscode. When the query
iris image is analyzed during authentication, the iris
blocks are extracted, compared with the cluster maps
thus generating a new iris code, which is corrected using
the stored Reed Solomon redundancy set and employed
to unlock the vault. The secret key is thus revealed.
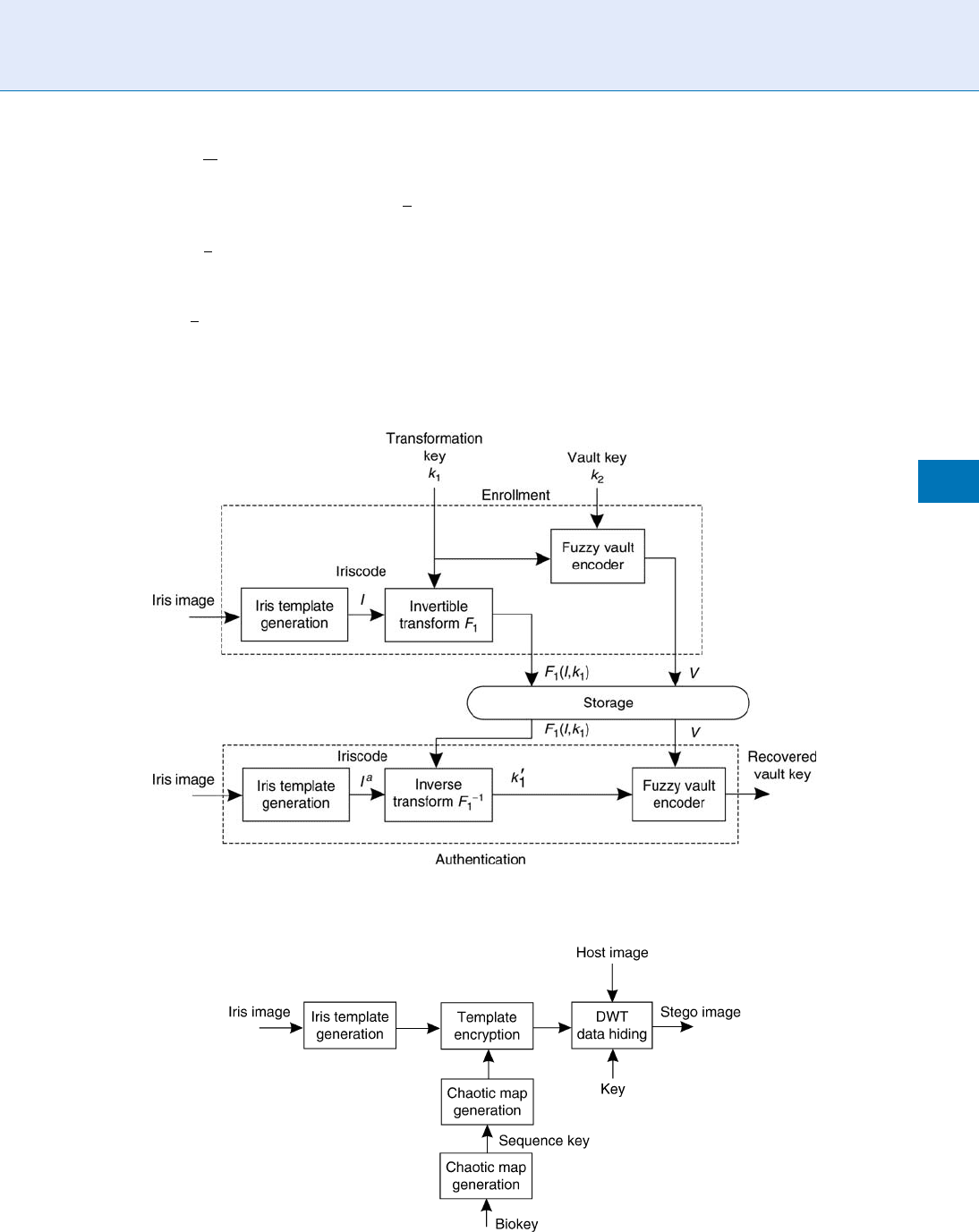
In [13] an iris cryptosystem relying on an invertible
transform, followed by fuzzy vault locking has been
proposed to secure the iriscode [6]. The scheme is
given in Fig. 4. More in detail the proposed iris cryp-
tosystem is a two step process. In the first step, an
invertible transform F
1
, chosen on the base of a ran-
domly generated transformation key k
1
, is applied to
the iriscode I. In the second step, the fuzzy vault
scheme, with key k
2
, is applied to secure the transfor-
mation key k
1
, thus giving the vault V . Both the trans-
formed iriscode and the vault, which locks the
transformation key k
1
, are eventually stored. In the
authentication stage, the inverse transformation F
1
1
is applied to the transformed iris code template using
the query iriscode I
a
, thus obtaining the transforma-
tion key k
0
1
. Then the transformation key k
0
1
is used to
decode the vault V. If the vault key k
2
is successfully
recovered this implies that there is a match between the
iriscode template I and the iriscode used in the authen-
tication stage I
a
. The author of [13] points out that
both the invertible transform and the fuzzy vault intro-
duce error correction, therefore the proposed crypto-
system is able to manage a higher intra class variation.
The protection of iris templates is also discus sed in
[14], where a trade-off between the authentication
performances and the security of key binding schemes,
is discussed from an information theoretic perspective.
A practical cryptosystem for iris templates, based on
Low Density Parity Codes (LDPC) and belief propaga-
tion, is also proposed. The pre-processing of the iris
Iris Template Protection. Figure 3 Fuzzy Vault scheme as in [12].
870
I
Iris Template Protection
images is performed according to [6], thus obtaining a
binary sequence
m. The bits corresponding to unreli-
able positions, identified during training, are discar-
ded from m. The obtained binary vector
z is then
mapped into the secure biometr ic S by computing
the syndrome of
z with respect to a low density parity
check code, whose parity check matrix H is randomly
chosen. When a user claims his identity, the realiable
feature vector
z
0
is computed and a belief propaga-
tion algorithm is applied to retrieve the sequence
whose syndrome is S. The trade-off between the False
Rejection Rate and the security of the proposed
implementation is discussed, while the False Accep-
tance Rate is not taken into account.
Iris Template Protection using Data
Hiding
In [15] a steganagraphic technique for covert commu-
nication of biometric data using chaos theory is pro-
posed with application to irisdata. The proposed data
hiding scheme is sketched in Fig. 5. Specifically, the iris
template, namely the iriscode, is extracted using the
Iris Template Protection. Figure 4 Iris cryptosystem [13].
Iris Template Protection. Figure 5 Chaos based data hiding scheme [15].
Iris Template Protection
I
871
I

method in [6]. Then two chaotic maps are used for
encrypting the iris template. The first map is used to
generate a 1D sequence of real numbers used as a
sequence key. A biometric generated key, the biokey,
is used to set the initial condition and the parameters
of the chaotic map. Then, the so obtained 1D sequence
is used as the sequence key of a different chao tic map
which is used to encrypt the template. The authors of
[15] point out that this approach assures robus tness
against different kind of attacks. After encryption, the
template is embedded into the cover image by using a
discrete wavelet transform (DWT) decomposition. The
template extraction and decryption is made on the
authentication side by performing dual operations
with respect to the ones done at the embedding side.
The authors hig hlights that their method offers better
performance than those given by using only one cha-
otic map.
Summary
Template protection is a key requirement when de-
signing a biometric based authentication system. A
brief overview of the main approaches based on the
use of transforms, bio metric cryptosystems, and data
hiding techniques, either specifically tailored or simply
applied to iris template protection have been here
outlined.
Related Entries
▶ Biometric Encryption
▶ Biometric Security Overview
▶ Iris Databases
▶ Iris Digital Watermarking
▶ Template Security
References
1. Menezes, A., van Oorschot, P., Vanstone, S.: Handbook of
applied cryptography, CRC Press (1996)
2. Bolle, R.M., Connell, J.H., Ratha, N.K.: Biometric perils and
patches. Pattern Recognit. 35, 2727–2738 (2002)
3. Jain, A.K., Nandakumar, K., Nagar, A.: Biometric template secu-
rity. EURASIP J. Adv. Signal. Process, Special Issue on Advanced
signal processing and pattern recognition methods for
Biometrics, article ID 579416 (2008)
4. Cox, I., Miller, M., Bloom, J., Miller, M., Fridrich, J.: Digital
watermarking and steganography 2nd edn. Morgan Kaufmann
(2007)
5. Chin, C.S., Teoh, A.B.J., Ngo, D.C.L.: High security iris verifica-
tion system based on random secret integration. Comput. Vis.
Image Underst. 102(2), 169–177 (2006)
6. Daugman, J.: How iris recognition works. IEEE Trans. Circuits
Syst. Video Technol. 14(1), 21–30 (2004)
7. Juels, A., Wattenberg, M.: A fuzzy commitment scheme, In: Sixth
ACM Conference on Computer and Communication Security,
pp. 28–36 (1999)
8. Juels, A., Sudan, M.: A fuzzy vault scheme, In: Proceedings of
the IEEE on International Symposium on Information Theory,
pp. 408 (2002)
9. Yang, S., Verbauwhede, I.: Secure iris verification, In: Proceed-
ings of the IEEE ICASSP 2007, vol. 2, pp. 133–136 (2007)
10. Hao, F., Anderson, R., Daugman, J.: Combining crypto with
biometrics effectively. IEEE Trans. Comput. 55(9), 1081–1088
(2006)
11. Bringer, J., Chabanne, H., Cohen, G., Kindarji, B., Zemor, G.:
Optimal iris fuzzy sketches. In: First IEEE International Confer-
ence on Biometrics: Theory, Applications, and Systems, BTAS
2007, pp. 1–6 (2007)
12. Lee, Y.J., Bae, K., Lee, S.J., Park, K.R.: Biometric key binding:
Fuzzy vault based on iris images. ICB 2007, LNCS 4642,
pp. 800–808 (2002)
13. Nandakumar, K.: Multibiometric systems: Fusion strategies and
template security, Dissertation, Michigan State University, De-
partment of Computer Science and Engineering (2008)
14. Martinian, E., Yekhanin, S., Yedidia, J.S.: Secure biometrics via
syndromes. In: 43rd Annual Allerton Conference on Commu-
nications, Control, and Computing, Monticello, IL, Oct (2005)
15. Khan, M.K., Zhang, J., Tian, L.: Chaotic secure content-based
hidden transmission of biometric templates, Chaos Solitons &
Fractals, Elsevier, 32, pp. 1749–1759 (2007)
Iris Template Security
▶ Iris Template Protection
Iris2pi
This is a most widely used iris recognition algorithm as
of 2008. This is a version of the Daugman algorithm.
It differs from an earli er version, ‘‘bowtie,’’ in the way
it handles eyelid (and other) occlusions. The bowti e
872
I
Iris Template Security

algorithm analyzed a bowtie shaped section of the iris –
two triangular wedges extending to the left and right –
that avoided most eyelid occlusion at the expense of
throwing away information for eyes that are wide
open. Iris2pi attempts to analyze all the iris that can
be seen – a full 2p radians if possible. Iris2pi note
regions that are occluded or otherwise invalid for bio-
metric identification; it records that information in the
biometric template. When two templates are com-
pared, the algorithm only compares regions that have
valid data.
▶ Iris Device
▶ Iris Encoding and Recognition using Gabor Wavelets
IrisCode
IrisCode is a digitized, normalized, compact encoding
of the unique texture visible in the iris of an eye, for
purposes of automated biometric identification. The
IrisCode is mapped between the inner and outer
boundaries of the iris, so it is size-invariant, distance-
invariant, and also invariant to changes in pupil
dilation. This intrinsic normalization facilitates the
searching and matc hing operations. In the standard
format (called ‘‘iris2pi’’) used in public deployments
of iris recognition, the IrisCode is based on a phase
encoding by Gabor wavelets, and it also incorporates
masking bits signifying the detection of eyelids, eye-
lashes, reflections, or other noise. Standard code
lengths are 512 or 1,024 bytes. The IrisCode enables
simple parallel logical operators XOR (Exclusive-OR)
and AND to generate Hamming Distance scores
for similarity between IrisCodes, at speeds of typically
1 million complete IrisCode comparisons per second.
▶ Iris Encoding and Recognition using Gabor
Wavelets
▶ Iris Recognition at Airports and Border-Crossings
▶ Score Normalization Rules in Iris Recognition
▶ Wavefront Coding for Enhancing the Imaging
Volume in Iris Recognition
ISO
ISO is an acronym referring to International Standard
Organization, an international entity responsible for
defining standards and providing certifications of
compliance.
▶ Biometric Sensor and Device, Overview
ISO
I
873
I


J
JPEG and JPEG2000 Image
Compression
Images can be encoded much more efficiently than by
pixel arrays if local regions are represented as combi-
nations of elementary functions. Computing the coef-
ficients on those elementary functions such that their
linear combination becomes equivalent to, or closely
approximates, the original image is the same operation
as computing a transform. Each local image region is
multiplied by each of several such elementary func-
tions and integrated to obtain each such coefficient.
The resulting coefficients usually have lower entropy
than the original pixel distribution, enabling more
compact coding; in addition, their values can be
coarsely quantized without detrimental effect. An
image is recovered from the coded coefficients by es-
sentially an inverse transform. The most ubiquitous
image compression protocol is JPEG, defined by ISO
Standard 10918. It applies the Discrete Cosine Trans-
form (DCT) to local square tiles of an image (typically
8 8 pixels), but the abrupt truncation of each cosine
wave causes ‘‘block quantization’’ artifacts which be-
come noticeable when only subsets of cosine waves are
used in order to achieve compression ratios above
about 30:1. JPEG2000 overcomes this problem by
replacing the block DCT cosine waves with Daubechies
wavelets which are smoothly attenuated instead of
chopped; the resulting Discrete Wavelet Transform
(DWT) is the core of JPEG2000 ISO Standard 15444.
JPEG2000 also has other advanced features to allocate
the coding budget inhomogeneously across an image if
needed. Both protocols allow control over the com-
pression factor (CF for JPEG2000; quality factor QF
for JPEG). Despite its superior mathematical basis and
performance, JPEG2000 is not as widely used as JPEG
nor as freely available.
▶ Iris Recognition Performance Under Extreme Image
Compression
#
2009 Springer Science+Business Media, LLC


K
Kernel
A kernel k is a function that for all x, z 2 X: satisfies
kðx; zÞ¼FðxÞFðzÞ, where F is a mapping from
the input space X to the feature space H ,
i.e., F : x 7! F ðxÞ2H . A kernel function can also
be characterized as follows: Let X be the input space.
A function k: X X: 7! R (or C) is kernel if and
only if for any M 2 N and any finite data set
fx
1
; ; x
M
gX, the associated Gram matrix is
positive semi-definite.
▶ Non-linear Techniques for Dimension Reduction
Key Binding
▶ Biometric and User Data, Binding of
Keypoints
▶ Local Image Features
Keystroke Dynamics
▶ Keystroke Recognition
Keystroke Pattern Classification
▶ Keystroke Recognition
Keystroke Recognition
NICK BARTLOW
West Virginia University, Morgantown, WV, USA
Synonyms
Behavioral biometrics; Keystroke dynamics; Keystroke
pattern classification
Definition
Keystroke recognition is a ▶ behavioral biometric
which utilizes the unique manner in which a person
types to verify the identity of an individual. Typing
patterns are predominantly extracted from computer
keyboards, but the information can potentially be
gathered from any input device having traditiona l
keys with tactile response (i.e., cellular phones, PDA’s,
etc). Although other measurements are conceivable,
patterns used in keystroke dynamics are derived
mainly from the two events that make up a keystroke:
the Key-Down and Key-Up. The Key-Down event takes
place at the initial depression of a key and the Key-Up
occurs at the subsequent release of that key. Various
unique features are then calculated based on the intra-
key and inter-key timing variations between these
events. After feature extraction, a wide range of algo-
rithms can be employed to establish whether the
unique pattern confirms or denies the claimed identity.
#
2009 Springer Science+Business Media, LLC

Introduction
The earliest form of keystroke recognition emerged
in the early 1900s during the days of World War I.
During the war, the French used listening posts in
which operators were able to recognize the ‘‘fist’’ of
enemy radio operators communicating in Morse code.
These trained individuals would learn to recognize
operators by differing lengths of pauses, dots and
slashes, and varying transmission speeds. This intelli-
gence subsequently allowed the French to establish the
identity of entities such as enemy battalions. Far more
sophisticated than electromechanical telegraphs used
to transmit Morse code, keyboards of today offer many
more opportunities to establish the unique manner in
which one types. Intuitively, coarse level differentiation
can be achieved by investigating typing speeds. For
instance, a professional ty pist who averages 90 or
more words per minute would be easily distinguished
from a ‘‘hunt and peck’’ amateur who averages only
20–25 words per minute. That said, this feature only
goes so far as many people type at similar speeds and
the average speed that an individual types can vary
significantly depending on many factors. The time it
takes an individual to locate a key (sometimes referred
to as ‘‘seek-time’’) also varies from key to key. For
instance, left-handed individuals may have quicker
seek-times for keys on the left side of the keyboard
and vice versa [1]. Along those same lines, use of the
shift keys to modify characters can also vary from
individual based on handedness and typing skill.
Trained professionals will always modify characters
on the right side of the keyboard with the left shift
key while amateurs may continually use the right shift
key to do so [2]. Language undoubtedly plays a large
role in the individuality of a typing signature. Given
that a person speaks English, commonly used words
like {the, and, you, are} are often ‘‘programmed’’ in
one’s mind and typed quickly as oppo sed to an indi-
vidual of a different native language. Additionally,
individuals typically exhibit a consistent pattern of
errors including replacements, reversals, and extrane-
ous hits. In an extreme case, the consistent lack of
errors is a pattern in itself.
Keyboard Technology and Semantics
There are four different kinds of switch technology
used in keyboards today; pure mechanical, foam
element, rubber dome, and membrane [3]. Each switch
type has various characteristics such as feel, durability,
price, etc. No matter the key switch technology chosen,
when a key is depressed, a degree of ‘‘bounce’’ is pres-
ent. Bounce can be defined as the effect when the
contact device rapidly engages and disengages over an
extremely short period of time [3]. Keyboards, either
external to desktop PCs or internal to laptops and
other devices are computers in their own right as
they contain a microprocessor, RAM, and sometimes
ROM. Using their processors and controllers, they
filter out the difference between bounce and two suc-
cessive keystrokes. Each stroke therefore consists of two
events, when the plates are engaged and when the
engagement is released or disengaged. Scan codes
resulting from thes e events are sent from the controller
in the keyboard to the event handler in the BIOS of the
device in question (usually a PC) [3]. Scan codes are
recorded by the processor based on a matrix composed
of all the keys on the keyboard. The keyboard matrix
operates on a buffer that allows for the processing of
simultaneous keystroke events. As mentione d before,
when a key is pressed down, the plates become en-
gaged. It is at this point that the keyboard processor
sends a ‘‘make code’’ encoded as a hex value to the
device. The make code can be thought of as including
both the key engaged and various other state flags
indicating if/how the key was modified by any of the
various control keys such as shift, alt, etc. Once the key
disengages, a corresponding ‘‘break code’’ is sent to the
PC [3]. These ideas form the basis of keyboard tech-
nology at its lowest-level.
Using this background as a foundation, the upper
level semantics of keyboard operation can be defined.
The basis of all features included in keystroke recogni-
tion is founded on the keystroke event and the associated
make code or break code correlation described previ-
ously. Instead of dealing with terms like ‘‘make code,’’
‘‘disengagement,’’ etc., researchers usually yield to
the more intuitive, higher level definitions below.
1. Key-down. The event that fires when a key is pressed
down. This corresponds to the event of the key-
board processor sending the device (usually a PC) a
‘‘make code.’’ It should be noted that this event will
continually fire until the key being depressed is
released. The speed at which the Key-down event
fires while a key is depressed is referred as the
‘‘repeat rate.’’ This is a user customizable property
in virtually all operating systems.
878
K
Keystroke Recognition

2. Key-up. The event that fires when a currently de-
pressed key is subsequently released.
3. Keystroke. The combination of an initial Key-down
event and the corresponding Key-up event.
4. Hold time. The length of time between an initial
Key-down event and the corresponding Key-up
event. Hold time is sometimes referred to as
‘‘dwell time.’’
5. Delay. The length of time between two successive
keystrokes. It should be noted that this time can be
positive or negative (overlapping strokes). Some
works refer to delay as ‘‘latency’’ or ‘‘flight.’’
Some highly specialized keyboards can record other
information such as the pressure of key strikes, but
the foundation of the technolo gy is based on the events
defined above.
Feature Representation and
Classification
A wide variety of algorithmic approaches have been
explored as suitable candidates for the task of keystroke
recognition. The problem of keystroke recognition fits
well within the general fields of pattern recognition and
machine learning; the two main tasks involved in solv-
ing problems within these fields are to define the repre-
sentation of the feature space and the algorithm used to
predict the class of samples. As mentioned in previous
sections, the features in keystroke recognition are pri-
marily derived from the elements that make up a key-
stroke. Most algorithms utilize first order statistics such
as minimum, maximum, mean, median, and standard
deviation of hold times and latencies [2, 4–8] for feature
representation. Here, hold times are for individual keys
whereas latencies are measured between two keystrokes
often defined as ‘‘digraphs.’’ Using these statistics, one
can either calculate fixed length feature vectors as out-
lined in [2] or variable length feature vectors as outline
in [9]. Fixed length or static size feature vectors will
always have a predetermined length despite the length
of the input sequence. The size of variable length or of
dynamic feature vectors will depend on the size of the
input sequence. Although the vast majorit y of key-
stroke recognition systems rely on single key hold
times and digraph latencies, some approaches define
other feature sets including trigraph durations, order-
ing of keystrokes (when shift-key modification is re-
quired), etc. [9].
Beyond feature representation, a keystroke recogni-
tion system must employ an algorithm to predict the
class of incoming samples. In general, the approaches
can be broken down into two sections: distance metric
based approaches and machine learning approaches.
After calculating the feature vector for an incoming
sample, the chosen algorithm must predict the class
of the sample (genuine or imposter). Many approaches
will do so by comparing the incoming sample to one or
more reference samples in a template database through
a distance metric. Popular distance metrics include:
Euclidean, Mahalanobis, Manhattan, Chebyshev, and
Hamming. When distance metrics are employed to
compare two samples, the smaller the score the closer
the two samples are to each other. Gaines and Lisowski
[4], Garcia [10], Young and Hammon [11], and Joyce
and Gupta [5] are all examples of algorithms that
utilize one or more of these distance metrics as classi-
fication schemes. Table 1 provides an over view of se-
lected work in keystroke recognition including the
works listed above. The table includes the features/
algorithm used, input requirements, the scope, and
performance. Under the performance column the raw
totals in terms of FAR and FRR are presented within
parentheses when listed in the work.
As the field has matured, many other machine
learning approaches have emerged as viable solutions
for prediction mechanisms in keystroke recognition.
Neural networks have widely been employed with
works by Obaidat et al. [6, 7], Brown et al. [12], and
Maisuria et al. [13]. Cho and Yu have applied Support
Vector Machines (SVM’s) to the problem extensively
[14, 15]. Additionally, Bartlow and Cukic explored the
decision tree approach of Random Forests [2] (see
Table 1 for more information on listed works).
Applications and Challenges
In application, the uses of keystroke rec ognition
can range anywhere from stand-alone biometric
systems to augmenting general computer security sys-
tems. Depending on various system specific security char-
acteristics such as database size and operational risks,
keystrok e recognition is suitable as a stand-alone biomet-
ric. Although not on the level of physiological biometrics
such as iris, fingerprint, and face, many works in the
literature indicate that the attainable performance rates
are within the scope of what some operational profiles
would require. Much like the physiological biometrics,
Keystroke Recognition
K
879
K
