FitzGerald J., Dennis A., Durcikova A. Business Data Communications and Networking
Подождите немного. Документ загружается.

7.3 BACKBONE NETWORK ARCHITECTURES 245
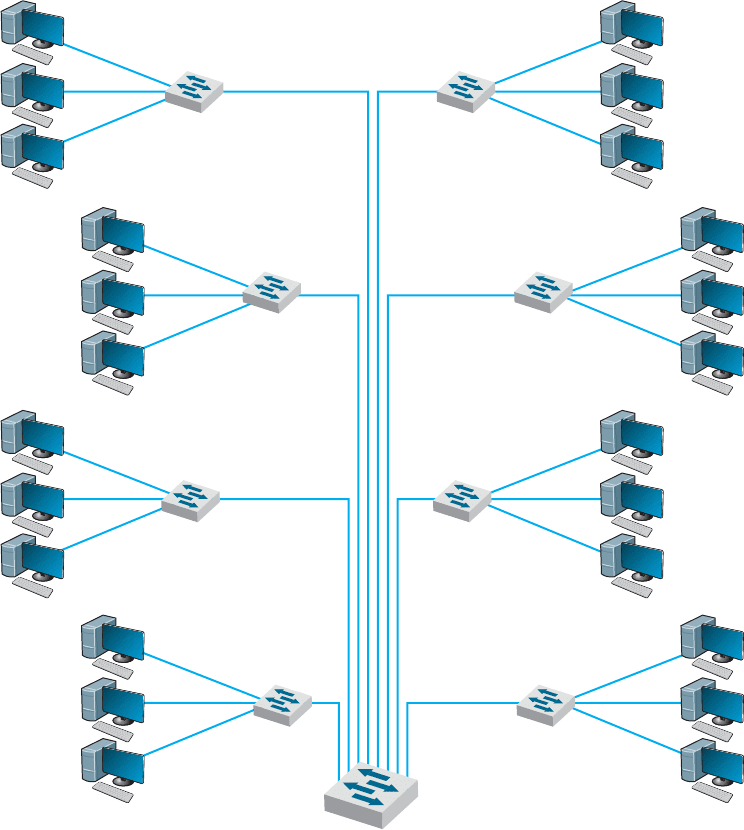
Switched backbone networks use a star topology with one switch at its center.
Figure 7.6 shows a switched backbone connecting a series of LANs. There is a switch
serving each LAN (access layer) which is connected to the backbone switch at the bottom
of the figure (distribution layer). This figure implies that the LAN switches are close to
the computers in their LANs and farther from the backbone switch. Most organizations
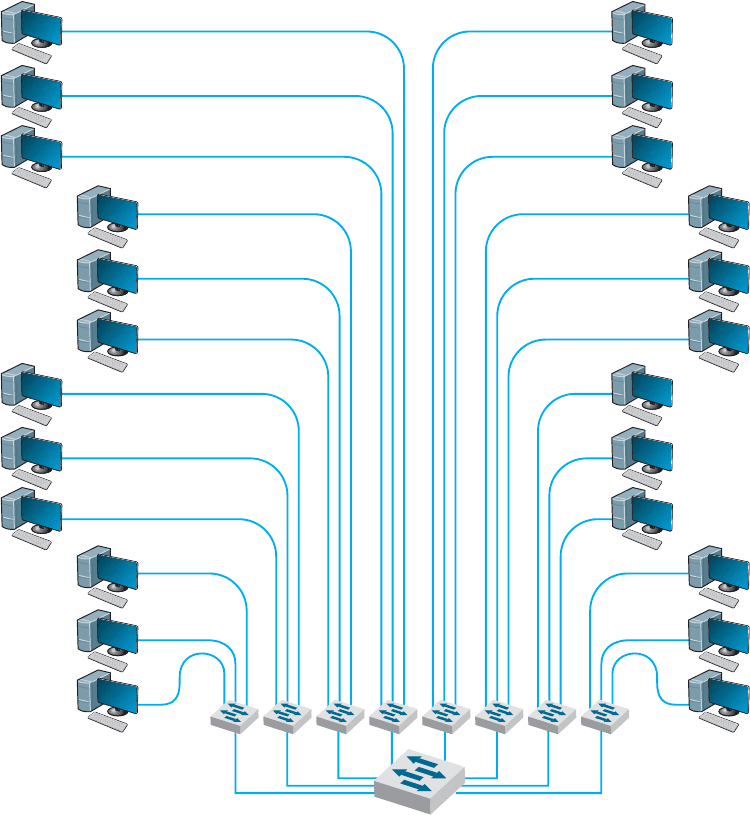
now use switched backbones in which all network devices for one part of the building
are physically located in the same room, often in a rack of equipment. This form of
switched backbone is shown graphically in Figure 7.7. This has the advantage of placing
Switch
Switch
Switch
Switch
Switch
Switch
Switch
Switch
Switch
FIGURE 7.6 Switched backbone network design
246 CHAPTER 7 BACKBONE NETWORKS
Switch
Switch
Switch
Switch
Switch
Switch
Switch
Switch
FIGURE 7.7 Rack-mounted switched backbone network design
all network equipment in one place for easy maintenance and upgrade, but it does require
more cable. In most cases, the cost of the cable itself is only a small part of the overall cost
to install the network, so the cost is greatly outweighed by the simplicity of maintenance
and the flexibility it provides for future upgrades.
The room containing the rack of equipment is sometimes called the main distribu-
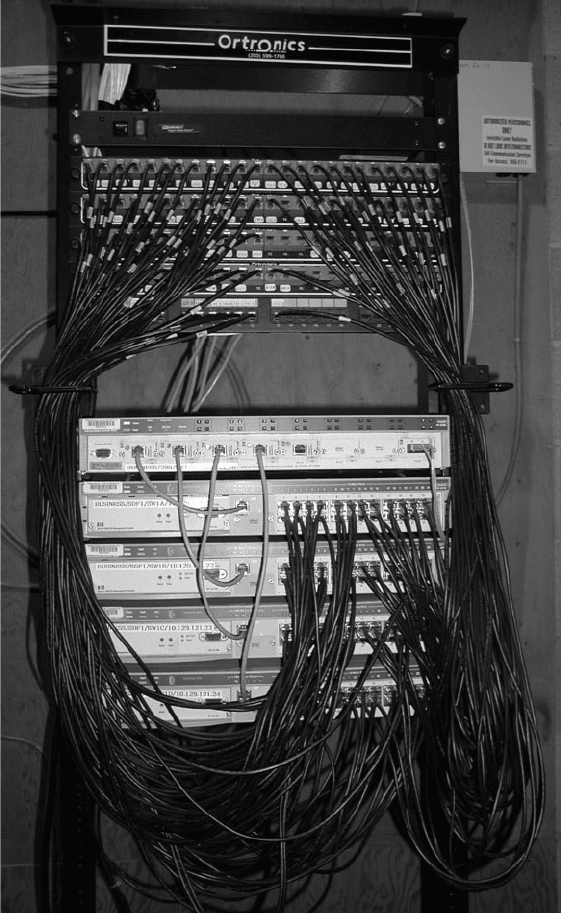
tion facility (MDF) or central distribution facility (CDF). Figure 7.8 shows a photo of an
MDF room at Indiana University. Figure 7.9 shows the equipment diagram of this same
room. The cables from all computers and devices in the area served by the MDF (often
7.3 BACKBONE NETWORK ARCHITECTURES 247
FIGURE 7.8 An MDF with
rack-mounted equipment. A layer-2
chassis switch with six 100Base-T
modules (center of photo) connects
to four 24-port 100Base-T switches.
The chassis switch is connected to
the campus backbone using
1000Base-F over fiber-optic cable.
The cables from each room are
wired into the rear of the patch
panel (shown at the top of the
photo), with the ports on the front of
the patch panel labeled to show
which room is which. Patch cables
connect the patch panel ports to the
ports on the switches
hundreds of cables) are run into the MDF room. Once in the room, they are connected
into the various devices. The devices in the rack are connected among themselves using
very short cables called patch cables.
With rack-mounted equipment, it becomes simple to move computers from one
LAN to another. In the switched backbone design as shown in Figure 7.6, for example,
all the computers in the same general physical location are connected to the same switch
248 CHAPTER 7 BACKBONE NETWORKS
7.1
SWITCHED BACKBONES
AT
INDIANA UNIVERSITY
MANAGEMENT
FOCUS
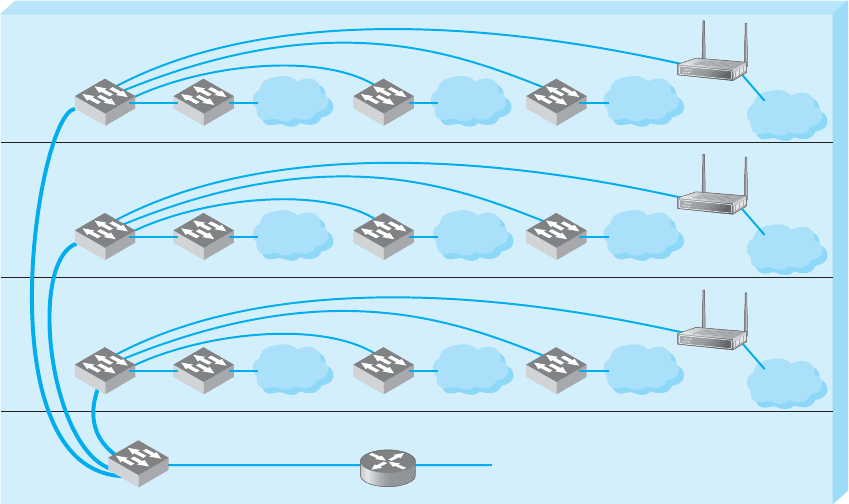
At Indiana University we commonly use switched
backbones in our buildings. Figure 7.10 shows a
typical design. Each floor in the building has a set
of switches and access points that serve the LANs
on that floor. Each of these LANs and WLANs are
connected into a switch for that floor, thus forming
a switched backbone on each floor. Typically, we
use switched 100Base-T within each floor.
The switch forming the switched backbone on
each floor is then connected into another switch
in the basement, which provides a switched
backbone for the entire building. The building
backbone is usually a higher speed network run-
ning over fiber-optic cable (e.g., 100Base-F or 1
GbE). This switch, in turn, is connected into a
high-speed router that leads to the campus back-
bone (a routed backbone design).
and thus share the capacity of the switch. Although this often works well, it can cause
problems if many of the computers on the switch are high-traffic computers. For example,
in Figure 7.6, if all the busy computers on the network are located in the upper left area
of the figure, the switch in this area may become a bottleneck.
Layer-2 Chassis Switch
Serial
(1 Port)
100Base-T
(1 Port)
100Base-T
(1 Port)
100Base-T
(1 Port)
100Base-T
(1 Port)
100Base-T
(1 Port)
Empty Empty
1000Base-F
(1 Port)
To Building
Backbone
LAN
24 port 100Base-T Switch
LAN
24 port 100Base-T Switch
LAN
24 port 100Base-T Switch
LAN
24 port 100Base-T Switch
FIGURE 7.9 MDF network diagram
7.3 BACKBONE NETWORK ARCHITECTURES 249
LAN
WLAN
LAN
LAN
Third Floor
LAN
WLAN
LANLAN
Second Floor
LAN
WLAN
LANLAN
First FloorBasement
To Campus Backbone
Router
Switch
Switch Switch Switch Switch
Switch Switch Switch Switch
Wireless AP
Wireless AP
Wireless AP
Switch Switch Switch Switch
FIGURE 7.10 Switched backbones at Indiana University
With an MDF, all cables run into the MDF. If one switch becomes overloaded, it
is straightforward to unplug the cables from several high-demand computers from the
overloaded switch and plug them into one or more less-busy switches. This effectively
spreads the traffic around the network more efficiently and means that network capacity is
no longer tied to the physical location of the computers; computers in the same physical
area can be connected into different network segments.
Sometimes a chassis switch is used instead of a rack. A chassis switch enables
users to plug modules directly into the switch. Each module is a certain type of network
device. One module might be a 16-port 100Base-T switch, another might be a router,
whereas another might be a 4-port 1000Base-F switch, and so on. The switch is designed
to hold a certain number of modules and has a certain internal capacity, so that all the
modules can be active at one time. For example, a switch with four 1000Base-T switches
(with 24 ports each), and one 1000Base-F port would have to have an internal switching
capacity of at least 97 Gbps ([4 × 24 × 1 Gbps] + [1 × 1 Gbps]).
The key advantage of chassis switches is their flexibility. It becomes simple to add
new modules with additional ports as the LAN grows and to upgrade the switch to use
new technologies. For example, if you want to add gigabit Ethernet, you simply lay the
cable and insert the appropriate module into the chassis switch.
7.3.3 Routed Backbones
Routed backbones move packets along the backbone on the basis of their network
layer address (i.e., layer-3 address). Routed backbones are sometimes called subnetted
250 CHAPTER 7 BACKBONE NETWORKS
backbones or hierarchical backbones and are most commonly used to connect different
buildings within the same campus network (i.e., at the core layer).
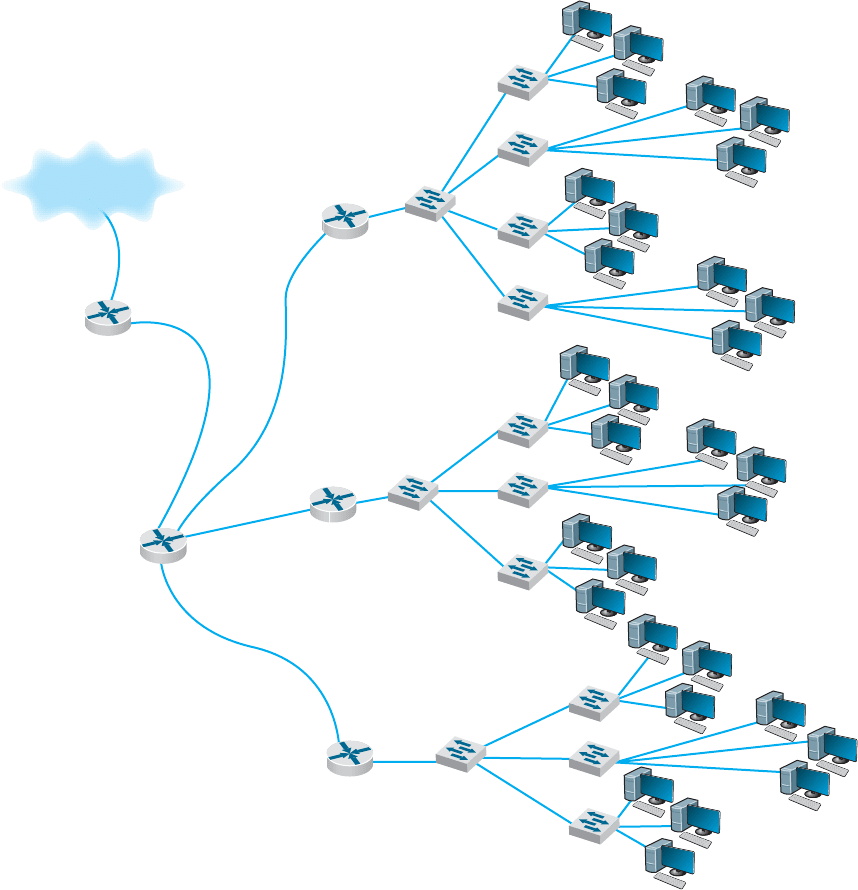
Figure 7.11 illustrates a routed backbone used at the core layer. A routed backbone
is the basic backbone architecture we used to illustrate how TCP/IP worked in Chapter 5.
There are a series of LANs (access layer) connected to a switched backbone (distribution
layer). Each backbone switch is connected to a router. Each router is connected to a core
Internet
Internet
Router
Core
Router
Router
Backbone
Switch
Computers
Computers
Computers
Switches
Switches
Switches
Backbone
Switch
Backbone
Switch
Router
Router
FIGURE 7.11 Routed backbone design

7.3 BACKBONE NETWORK ARCHITECTURES 251
router (core layer). These routers break the network into separate subnets. The LANs
in one building are a separate subnet. Message traffic stays within each subnet unless it
specifically needs to leave the subnet to travel elsewhere on the network, in which case
the network layer address (e.g., TCP/IP) is used to move the packet. For example, in a
switched backbone, a broadcast message (such as an ARP) would be sent to every single
computer in the network. A routed backbone ensures that broadcast messages stay in the
one-network segment (i.e., subnet) where they belong, and are not sent to all computers.
This leads to a more efficient network.
Each set of LANs is usually a s eparate entity, relatively isolated from the rest of
the network. There is no requirement that all LANs share the same technologies. Each
set of LANs can contain its own server designed to support the users on that LAN, but
users can still easily access servers on other LANs over the backbone as needed.
The primary advantage of the routed backbone is that it clearly segments each
part of the network connected to the backbone. Each segment (usually a set of LANs
or switched backbone) has its own subnet addresses that can be managed by a different
A Day in the Life: Network Operations Manager
The job of the network operations manager is to ensure
that the network operates effectively. The operations
manager typically has several network administrators
and network managers that report to him or her and is
responsible for both day-to-day operations as well as
long-term planning for the network. The challenge is
to balance daily firefighting with longer-term planning;
they’re always looking for a better way to do things.
Network operations managers also meet with users to
ensure their needs are met. While network technicians
deal primarily with networking technology, a network
operations manager deals extensively with both tech-
nology and the users.
A typical day starts with administrative work that
includes checks on all servers and backup processes to
ensure that they are working properly and that there are
no security issues. Then it’s on to planning. One typi-
cal planning item includes planning for the acquisition
of new desktop or laptop computers, including meeting
with vendors to discuss pricing, testing new hardware
and software, and validating new standard configura-
tions for computers. Other planning is done around
network upgrades, such as tracking historical data to
monitor network usage, projecting future user needs,
surveying user requirements, testing new hardware and
software, and actually planning the implementation of
new network resources.
One recent example of long-term planning was the
migration from a Novell file server to Microsoft ADS
file services. The first step was problem definition;
what were the goals and the alternatives? The key driv-
ing force behind the decision to migrate was to make it
simpler for the users (e.g., now the users do not need
to have different accounts with different passwords)
and to make it simpler for the network staff to pro-
vide technical support (e.g., now there is one less type
of network software to support). The next step was
to determine the migration strategy: a Big Bang (i.e.,
the entire network at once) or a phased implementa-
tion (several groups of users at a time). The migration
required a technician to access each individual user’s
computer, so it was impossible to do a Big Bang. The
next step was to design a migration procedure and
schedule whereby groups of users could be moved at
a time (e.g., department by department). A detailed
set of procedures and a checklist for network tech-
nicians were developed and extensively tested. Then
each department was migrated on a one-week sched-
ule. One key issue was revising the procedures and
checklist to account for unexpected occurrences during
the migration to ensure that no data were lost. Another
key issue was managing user relationships and dealing
with user resistance.
With thanks to Mark Ross
252 CHAPTER 7 BACKBONE NETWORKS
network manager. Broadcast messages stay within each subnet and do not move to other
parts of the network.
There are two primary disadvantages to routed backbones. First, the routers in
the network impose time delays. Routing takes more time than switching, so routed
networks can sometimes be slower. Second, routers are more expensive and require
more management than switches.
Figure 7.11 shows one core router. Many organizations actually use two core routers
to provide better security, as we discuss in Chapter 10.
7.3.4 Virtual LANs
For many years, the design of LANs remained relatively constant. However, in recent
years, the introduction of high-speed switches has begun to change the way we think
about LANs. Switches offer the opportunity to design radically new types of LANs.
Most large organizations today have traditional LANs, but many are considering the
virtual LAN (VLAN), a new type of LAN-BN architecture made possible by intelligent,
high-speed switches.
Virtual LANs are networks in which computers are assigned to LAN segments
by software rather than by hardware. In the preceding section, we described how in
rack-mounted collapsed BNs a computer could be moved from one hub to another by
unplugging its cable and plugging it into a different hub. VLANs provide the same
capability via software so that the network manager does not have to unplug and replug
physical cables to move computers from one segment to another.
Often, VLANs are faster and provide greater opportunities to manage the flow of tra-
ffic on the LAN and BN than do the traditional LAN and routed BN architecture. However,
VLANs are significantly more complex, so they usually are used only for large networks.
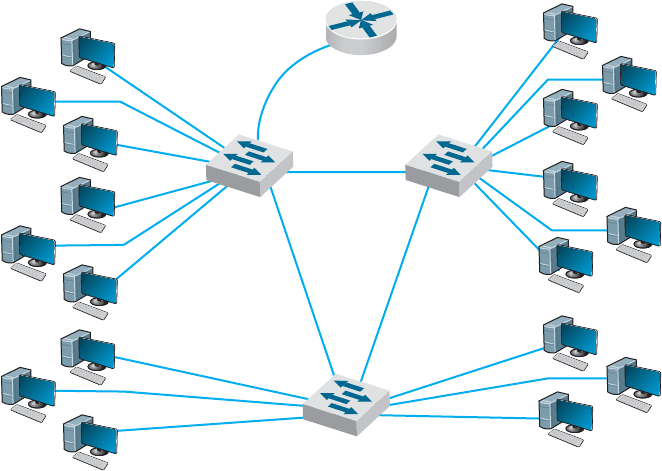
The simplest example is a single-switch VLAN, which means that the VLAN
operates only inside one switch. The computers on the VLAN are connected into the
one switch and assigned by software into different VLANs (Figure 7.12). The network
manager uses special software to assign the dozens or even hundreds of computers
attached to the switch to different VLAN segments. The VLAN segments function in the
same way as physical LAN segments or subnets; the computers in the same VLAN act as
though they are connected to the same physical switch or hub in a certain subnet. Because
VLAN switches can create multiple subnets, they act like layer-3 switches or routers,
except the subnets are inside the switch, not between switches. Therefore, broadcast
messages sent by computers in one VLAN segment are sent only to the computers on
the same VLAN.
Virtual LANs can be designed so that they act as though computers are connected
via hubs (i.e., several computers share a given capacity and must take turns using it) or
via switches (i.e., all computers in the VLAN can transmit simultaneously). Although
switched circuits are preferred to the shared circuits of hubs, VLAN switches with the
capacity to provide a complete set of switched circuits for hundreds of computers are
more expensive than those that permit shared circuits.
We should also note that it is possible to have just one computer in a given VLAN.
In this case, that computer has a dedicated connection and does not need to share the
network capacity with any other computer. This is commonly done for servers.

7.3 BACKBONE NETWORK ARCHITECTURES 253
Switch
FIGURE 7.12 VLAN-based backbone network design
Benefits of VLANs Historically, we have assigned computers to subnets based on
geographic location; all computers in one part of a building have placed in the same sub-
net. With VLANs, we can put computers in different geographic locations in the same
subnet. For example, in Figure 7.12 a computer in the lower left could be put on the
same subnet as one in the upper right—a separate subnet from all the other computers.
254 CHAPTER 7 BACKBONE NETWORKS
A more common implementation is a multiswitch VLAN, in which several
switches are used to build the VLANs (Figure 7.13). VLANs are most commonly found
in building backbone networks (i.e., access and distribution layers) but are starting to
move into core backbones between buildings. In this case, we can now create subnets
that span buildings. For example, we could put one of the computers in the upper left of
Figure 7.13 in the same subnet as the computers in the lower right, which could be in a
completely different building. This enables us to create subnets based on who you are,
rather than on where you are; we have an accounting subnet and a marketing subnet, not
a Building A and a Building B subnet. We now manage security and network capacity
by who you are, not by where your computer is. Because we have several subnets, we
need to have a router—but more on that shortly.
Virtual LANs offer two other major advantages compared to the other network
architectures. The first lies in their ability to manage the flow of traffic on the LAN and
backbone very precisely. VLANs make it much simpler to manage the broadcast traffic
that has the potential to reduce performance and to allocate resources to different types of
traffic more precisely. The bottom line is that VLANs often provide faster performance
than the other backbone architectures.
The second advantage is the ability to prioritize traffic. The VLAN tag information
included in the Ethernet packet defines the VLAN to which the packet belongs and also
specifies a priority code based on the IEEE 802.1q standard (see Chapter 4). As you will
recall from Chapter 5, the network and transport layers can use RSVP quality of service
(QoS), which enables them to prioritize traffic using different classes of service. RSVP
is most effective when combined with QoS capabilities at the data link layer. (Without
QoS at the hardware layers, the devices that operate at the hardware layers [e.g., layer-2
VLAN
Switch 1
Router
VLAN ID: 20; IP: 179.58.7.1
VLAN ID: 10; IP: 179.58.10.1
VLAN ID: 30; IP: 179.58.11.1
VLAN ID: 10
IP: 179.58.10.101
VLAN ID: 10
IP: 179.58.10.102
VLAN ID: 10
IP: 179.58.10.103
VLAN ID: 30
IP: 179.58.7.30
VLAN ID: 20
IP: 179.58.11.20
VLAN ID: 10
IP: 179.58.10.50
VLAN Switch 3
VLAN
Switch 2
FIGURE 7.13 Multiswitch VLAN-based backbone network design
